You give me 100 red envelopes, how about I give you 200 tomorrow.
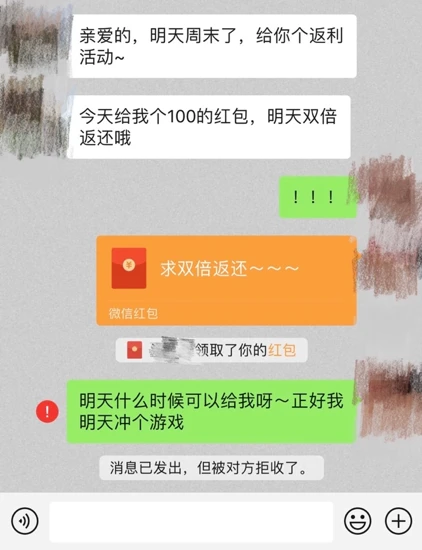 Those who dare to send red envelopes are sure to receive rewards, and I am afraid that only the most trusted people. Legal programs often broadcast some similar scams to warn everyone. However, the essence of being fooled lies in these two words: trust.
Those who dare to send red envelopes are sure to receive rewards, and I am afraid that only the most trusted people. Legal programs often broadcast some similar scams to warn everyone. However, the essence of being fooled lies in these two words: trust.
image description
In order to give back to everyone (in order to support Bitcoin), I will give back to everyone now. You only need to transfer 1,000 US dollars to the following address, and I will return you 2,000 US dollars. The activity is limited to half an hour!
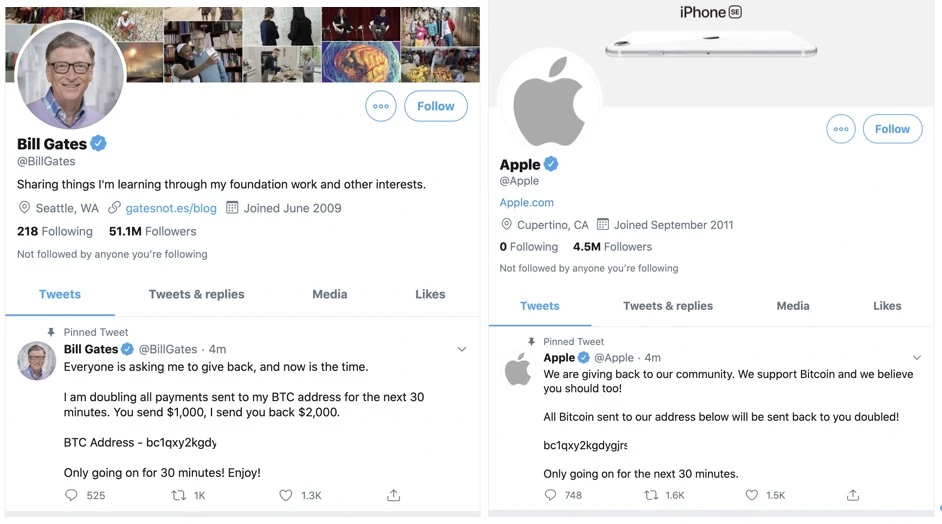
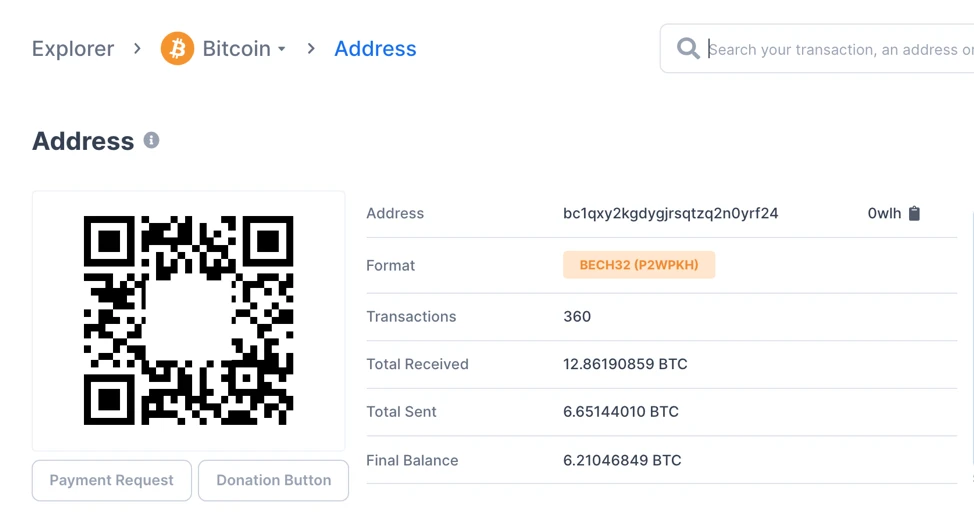
The content of the above pictures are all screenshots from CertiK security experts
image description
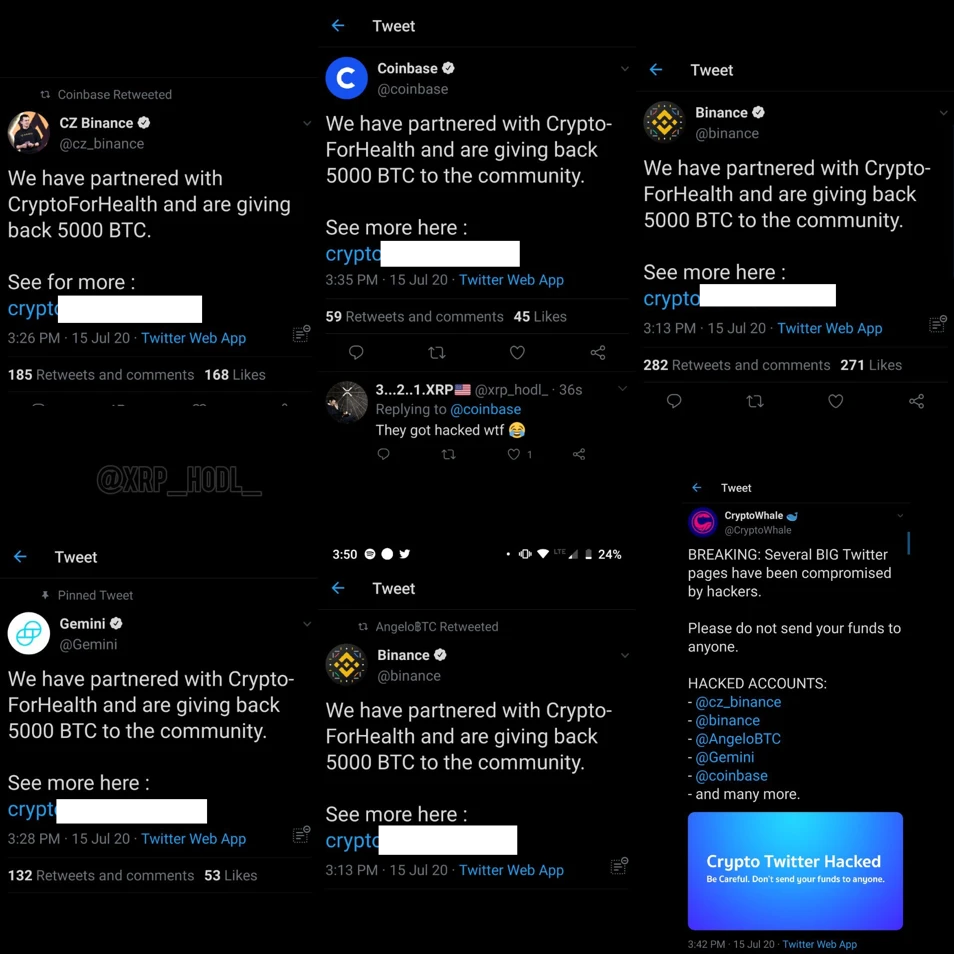
The content of the above pictures are all screenshots from CertiK security experts
image description
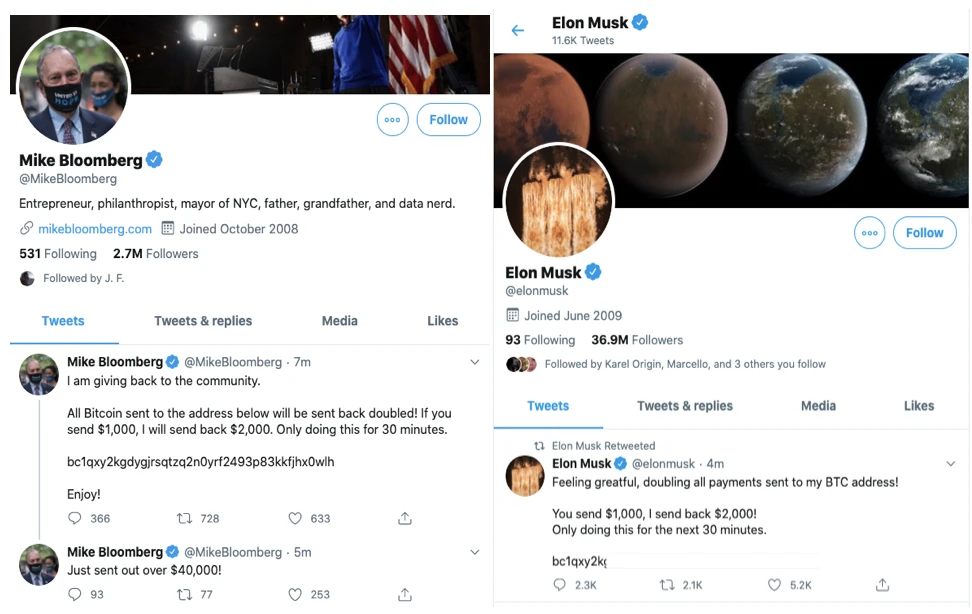
The content of the above pictures are all screenshots from CertiK security experts
text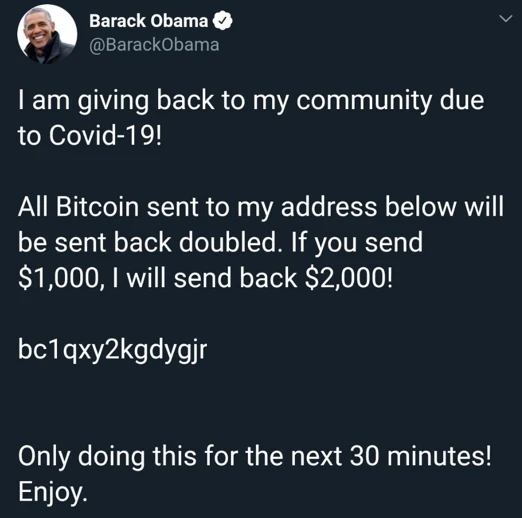
image description
secondary title
Rumors on the Internet
1. Twitter employee accounts hacked, hackers gain admin access
The screenshots that broke out on telegram are suspected to be the background management interface of Twitter employees. Hackers can modify the user mailbox through the background management interface, and then send the link to reset the password to the mailbox controlled by themselves, so as to gain control of the target account.
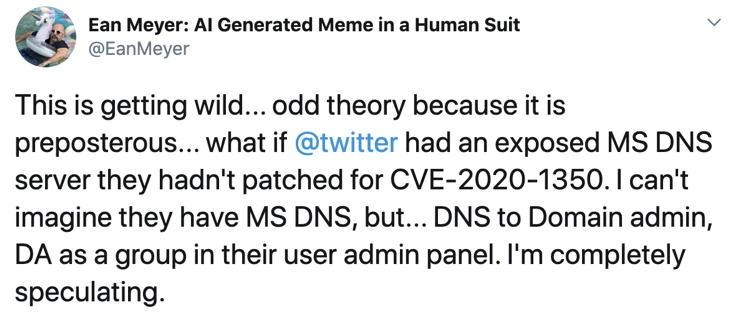
2. Hackers use the recently exposed vulnerabilities to attack the Twitter server and gain access to the management background
secondary title
Twitter official response
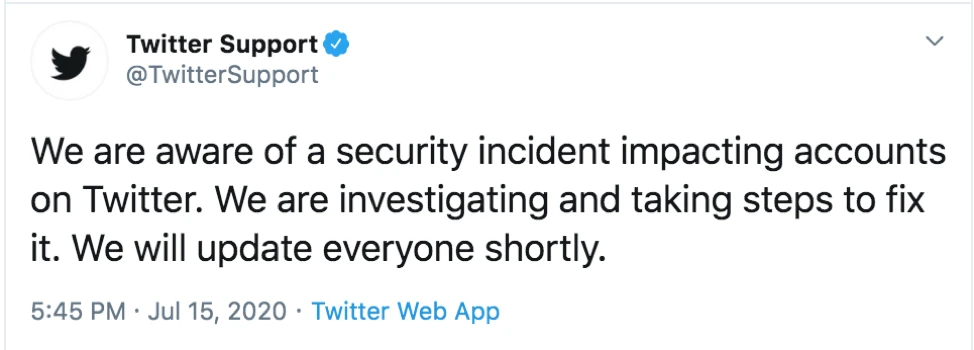
At present, the reasons for the hacking of each account have not been officially disclosed. Twitter also issued an official reply at 5:45 a.m. Beijing time on the same day, saying that it will investigate the reasons as soon as possible.
secondary title
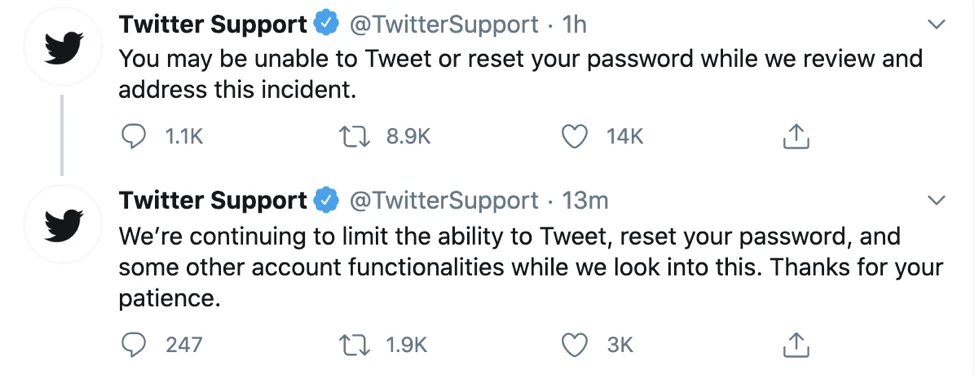
Safety Measures and Recommendations
There may be frequent incidents of one or two account thefts on social networking sites, but large-scale hacking incidents may be counted as the memorabilia of the magical year of 2020. Here the CertiK security team has compiled some measures to strengthen the security of Twitter accounts.
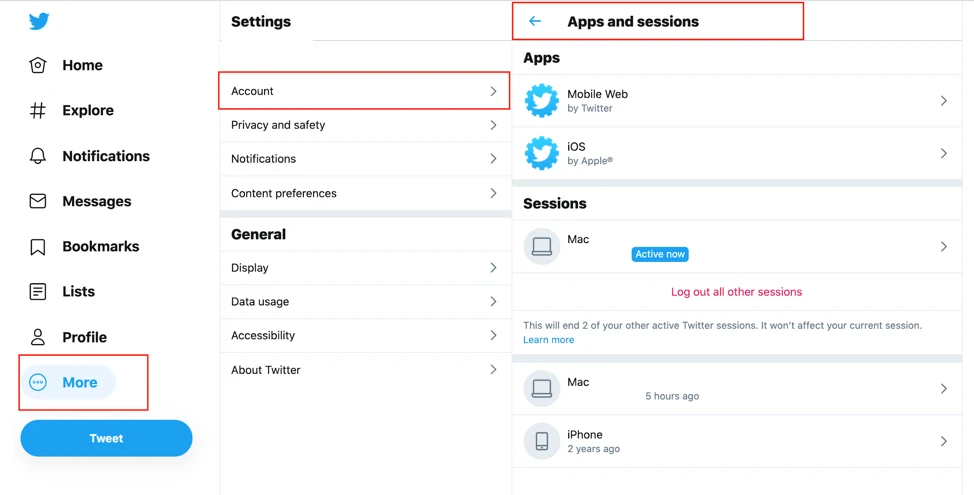
1. Cancel the application authorized to use your Twitter account
After logging in to Twitter, in More -> Settings and privacy -> Account -> Data and permissions -> Apps and sessions, you can see the applications currently authorized to obtain your Twitter-related permissions and the logged-in Sessions. The CertiK security team recommends regularly checking authorized Apps and removing unnecessary Apps in time. Log out suspicious Sessions.
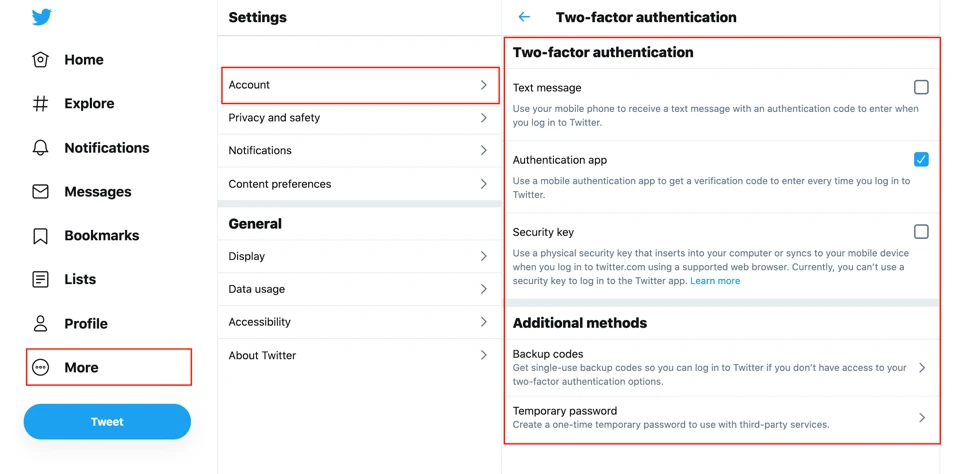
2. Enable two-factor authentication
secondary title
Insufficient investment in security
Twitter has a bug bounty program on the HackerOne bug bounty platform (https://hackerone.com/twitter). Someone pointed out that Twitter only rewards $7,700 for Account takeover (account stealing) vulnerabilities, and this time hackers have stolen more than $100,000 by exploiting such vulnerabilities. Such a comparison is thought-provoking.
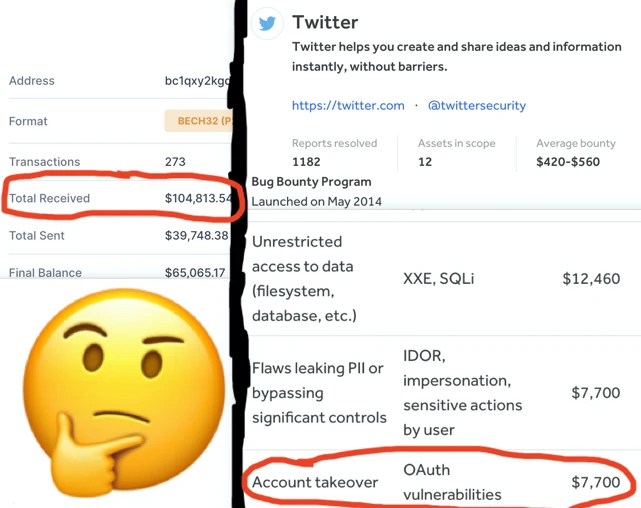
For a company, security does not matter when it is not hacked, and it is unwilling to invest money in security. And after being hacked, the losses caused are immeasurable.

Here, CertiK would like to remind everyone that even a tweet that looks very powerful may be hacked. So don’t be too convinced that a certain project is 100% safe. Once there is a 0.00000000000001% possibility of being attacked, according to Murphy’s Law, it will definitely happen. Therefore, investment in safety is essential. CertiK, as the worlds top blockchain security expert, is to help you find that 0.00000000000001% loophole and eliminate it. If your project requires,Welcome to send email to bd@certik.orgMake a consultation.










