Chengdu Lianan: Analysis of YFV extortion incident
YFV is a DeFi project based on Ethereum. Earlier today, YFV officially issued a document stating that it was blackmailed. The attacker can use the staking contract vulnerability to reset the YFV locked by the user arbitrarily.
Vulnerability analysis
Vulnerability analysis
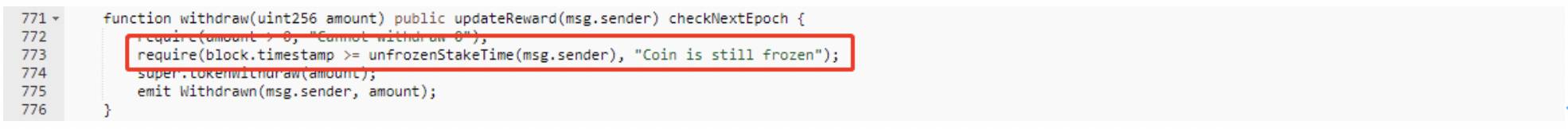
There is a stakeOnBehalf function in the contract so that the attacker can stake for any user, as shown in the following figure:

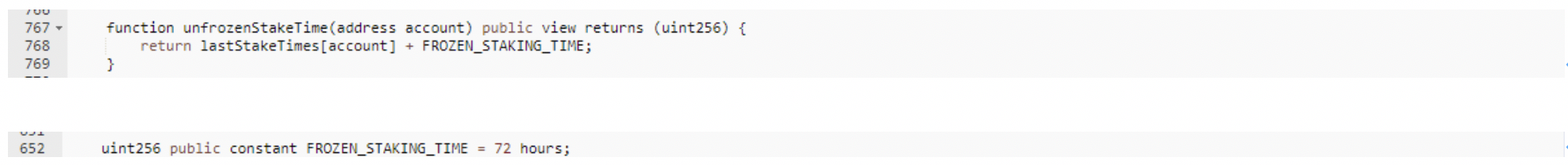
The lastStakeTimes[stakeFor] = block.timestamp; statement in this function will update the laseStakeTimes[user] of the user address mapping. And there is verification in the function used by the user to withdraw the mortgage, which requires the user to withdraw the time must be greater than lastStakeTimes[account]+72 hours. As shown below:
UnfrozenStakeTime is shown in the figure below:
To sum up, malicious users can mortgage small amounts of funds to normal users, thereby locking the funds of normal users.
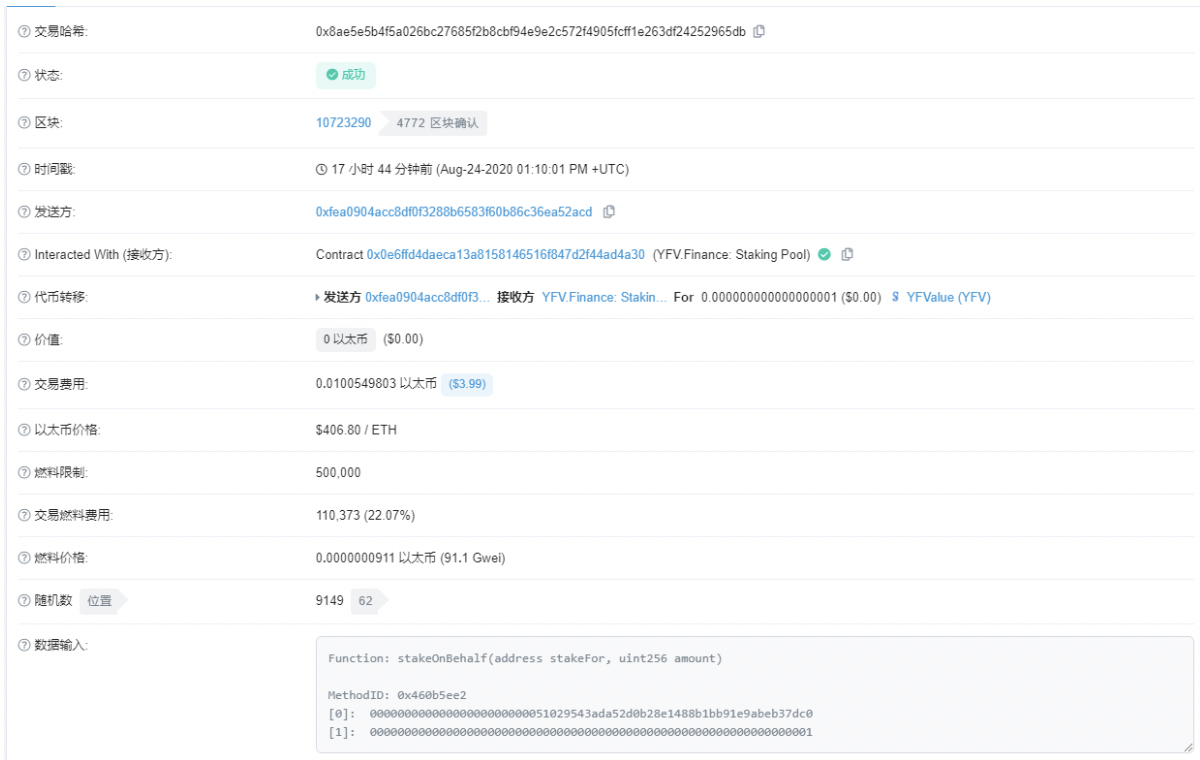
According to the information on the chain, we found two suspected attacks, as follows:
0xf8e155b3cb70c91c70963daaaf5041dee40877b3ce80e0cbd3abfc267da03fc9
0x8ae5e5b4f5a026bc27685f2b8cbf94e9e2c572f4905fcff1e263df24252965db
One of them is shown in the figure below:
Summarize
Summarize
For this incident, the root cause is that the code audit work before going online was not done well. This incident is actually a loophole at the business level.
According to Chengdu Lianan’s experience in code auditing, individual project parties did not provide complete project-related information when conducting code audits, making code audits unable to find some business loopholes, resulting in heavy losses after going online.
Chengdu Lianan Security Lab hereby reminds all project parties: security is the cornerstone of development, and a good code audit is a prerequisite for going online.



