CertiK Security Analysis: Analysis and Summary of Digital Currency-related Attacks in August
"One day in the currency circle, one year in the world", "One day in DeFi, one year in the currency circle".
In the recent blockchain and currency circles, almost all the popularity has been robbed by DeFi.
With the continuous emergence of projects and the influx of a large number of users, the total locked position of the DeFi protocol has reached 10.38 billion US dollars.
The extremely high investment returns have attracted a large number of currency holders to join, and August is a month when liquidity mining projects are in full swing.
From the experimental liquidity mining project Yam to SushiSwap, which is still highly topical, the entire blockchain community continues to discuss the huge profits and hidden security risks.
During this month, a large number of new mining projects appeared, most of which directly copied the codes of other similar projects and went online in a hurry without security audits. As a result, the discovered smart contract security vulnerabilities are numerous and similar in nature. Nowadays, the first condition to determine whether a project can be invested should be to check whether the project and its contracts have been professionally audited by a well-known security team and have obtained a high security rating.
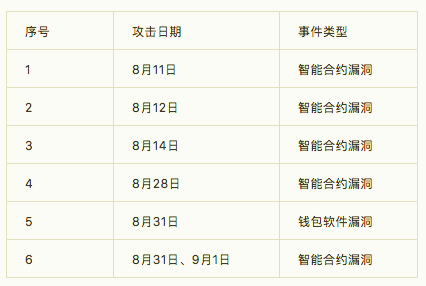
According to the statistics of the CertiK security technology team, the inventory of blockchain-related security incidents in August is as follows:
On August 11, the Ethereum-based token project NUGS had a security problem. There were security holes in its smart contract, which caused huge inflation in its token system. Since the security loopholes in the smart contract could not be fixed, the NUGS project officially announced that it had decided to abandon the project, and the tokens deposited in it could not be withdrawn.
On August 12, the liquid mining project Yam broke out a smart contract loophole, which would reserve a huge number of tokens, resulting in an increase in the number of tokens required for project governance. In the end, the community did not have enough tokens currency, any governance behavior cannot be carried out.
On August 14, the liquidity mining project Based had a smart contract security vulnerability and was attacked by an attacker. The function in the smart contract of the No. 1 pool of the project was wrongly set to be arbitrarily called by the outside, causing it to be preempted by the outside attacker. Initialization, resulting in the inability to complete any pledge in Pool 1.
On August 28, multiple security loopholes were discovered in the Sushiswap smart contract, which allowed the smart contract owner to withdraw money arbitrarily without any community authorization. At the same time, the contract also has a reentrancy attack vulnerability, which will cause potentially malicious code to be executed multiple times.
On August 31, 1,400 bitcoins were stolen due to users using an old version of the electrum wallet application with vulnerabilities.
On August 31 and September 1, the smart contracts of Sushiswap imitation disk Yuno and Kimchi were both found to have security vulnerabilities. inflation.
event details
event details
The following is a specific analysis of typical security incidents in August:
Incident No. 1 is a very typical vulnerability caused by mistakes in logic implementation. The commercial implementation model of the NUGS project is a lottery draw system. The lottery draw is based on rounds. In each round of lottery draws, investors can deposit funds into the round prize pool.
After a period of time, the lottery function in the NUGS smart contract can be called externally to determine the winner of this round of lottery draws. The winner gets the prize pool prize, and the caller from the outside calling the lottery function also gets a small part of the reward. When this round of lottery drawing ends, the amount in the prize pool will be cleared to zero. Therefore, when each round of lottery drawing starts, the initial amount in the prize pool should be "zero".
However, there is a logic implementation loophole in the NUGS smart contract regarding the initial amount of the prize pool bonus: when a round of lottery draws ends, the amount in the prize pool is not cleared, resulting in the initial amount in the prize pool being the previous round after the next round of lottery draws. total prize money. Therefore, there will be more and more bonuses in the prize pool, which will eventually lead to inflation and rapid depreciation of the currency value.
The No. 2 incident occurred in the Yam liquidity mining project, and it was also a security hole caused by a mistake in logic implementation.
There is a rebase function in the Yam smart contract, the purpose of which is to ensure the price stability of tokens. However, due to negligence at the code level, when each rebase is executed, the value of the total supply of tokens is calculated incorrectly. The number of totalSupply can only continue to increase, which eventually leads to inflation.
The loopholes in the above two incidents belong to the loopholes in the logic implementation level. Although the loopholes in the logic implementation are very intuitive, they cannot be checked by any existing automatic detection tools. Only professional security audits and/or rigorous mathematical proofs can be used to avoid such loopholes.
Incident No. 3 occurred in the liquidity mining project Based. When deploying its smart contract, Based officially only declared the owner by calling the renounceOwnership function in the smart contract, but did not initialize the smart contract. And an external attacker called the initialize function to initialize the smart contract before the official based.
This makes the owner of the smart contract inconsistent with the operator of the initialization, and eventually any pledge cannot be completed.
This security vulnerability is caused by the simultaneous impact of "the security risk of calling the smart contract itself" and "the risk of deploying the smart contract". The deployment of this kind of smart contract should ensure the atomicity of sending and deploying the smart contract and the initialization of the smart contract and other operational transactions (atomic operations can be one step or multiple operation steps, but the order cannot be broken) chaos, nor can it be cut to execute only part of it), that is, the two transactions should be related to each other to ensure that no third party takes advantage of the time difference to conduct malicious attacks.
The incidents No. 4 and No. 6 are the same: there are multiple smart contract vulnerabilities, and no security audit has been conducted before its launch. There is no corresponding community supervision mechanism for the problem of excessive rights of project owners.
The protagonist projects of these two events are SushiSwap (No. 4 event) and its imitations Yuno and Kimchi (No. 6 event). In the smart contract of the SushiSwap project, the smart contract owner has the right to use the setMigrator function to arbitrarily modify the value of the migrator without supervision, and then call any external code of the smart contract by calling migrator.migrate. This external code is unknown to the smart contract itself, so the smart contract owner can execute malicious code through this operation.
Similar loopholes also exist in the Yuno and Kimchi projects: smart contract owners have the right to perform an unlimited number of coin minting operations through the mint function.
Initially, the solution to this type of vulnerability was to use the timelock smart contract to add delay locks to any operations from the smart contract owner. SushiSwap, Yuno, and Kimchi all added a 48-hour operation delay to themselves through this method. Its original intention is to give investors a 48-hour window for any suspected malicious transaction from the owner of the smart contract, and there is enough time for withdrawal and other operations. Although Chef Nomi in the SushiSwap project successfully transferred a large amount of tokens and later returned them, in the end the SushiSwap project adopted a multi-signature wallet to ensure the decentralization of the project. It can be said that the delay lock has no way to fundamentally solve the loopholes in the smart contract itself.
Incident No. 5 was due to the fact that the victim used an old version of the Electrum wallet, and the attacker used a software vulnerability in the old version to conduct a phishing attack.
This software vulnerability renders HTML rendering of transaction error messages returned by the Electrum node server. An attacker can build a malicious node. When the node receives a transaction request from a user, a window containing phishing information will pop up in the user's wallet, allowing the user to download a so-called "wallet update".
safety advice
safety advice
To sum up, security incidents occurred frequently in August, and the CertiK security team made the following suggestions:
The security risks of blockchain projects not only need to be observed from the level of code vulnerabilities, but also carefully understand whether the logical implementation of the project is consistent with its logical design.
Blockchain projects need to plan a detailed design and implementation process for the entire deployment process to ensure the atomicity of deployment operations.
In the face of the problem of excessive rights of blockchain project smart contract owners, we should not only rely on external coercive mechanisms to restrict, but also integrate from multiple perspectives such as smart contract code implementation and community governance, so as to ensure that the project will not be used by any party. abuse.
The popularity of DeFi continues to rise. Blockchain, as the disruptive core technology of the era, has also been widely used in various fields. The security risks hidden under the benefits and benefits should not be ignored.
CertiK is committed to building a blockchain health and safety ecosystem, using industry-leading technology to solve the security pain points of blockchain and smart contracts.



