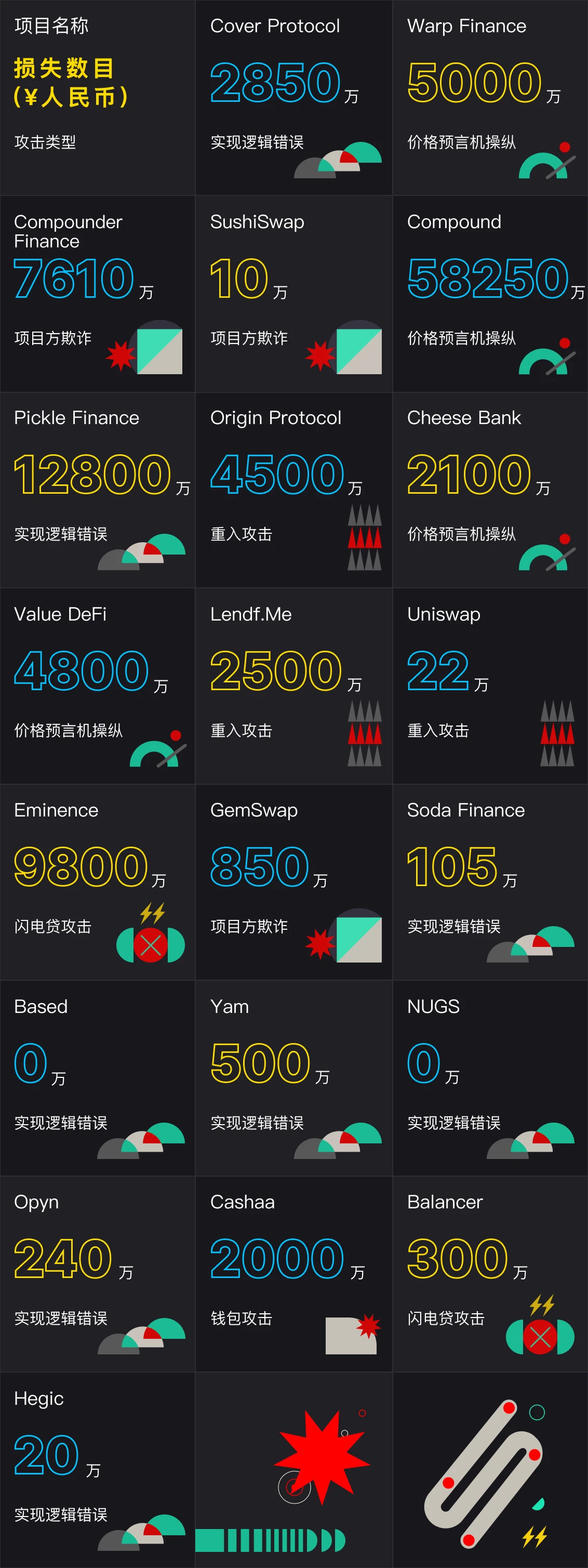
Table 1: List of major blockchain accident projects in 2020
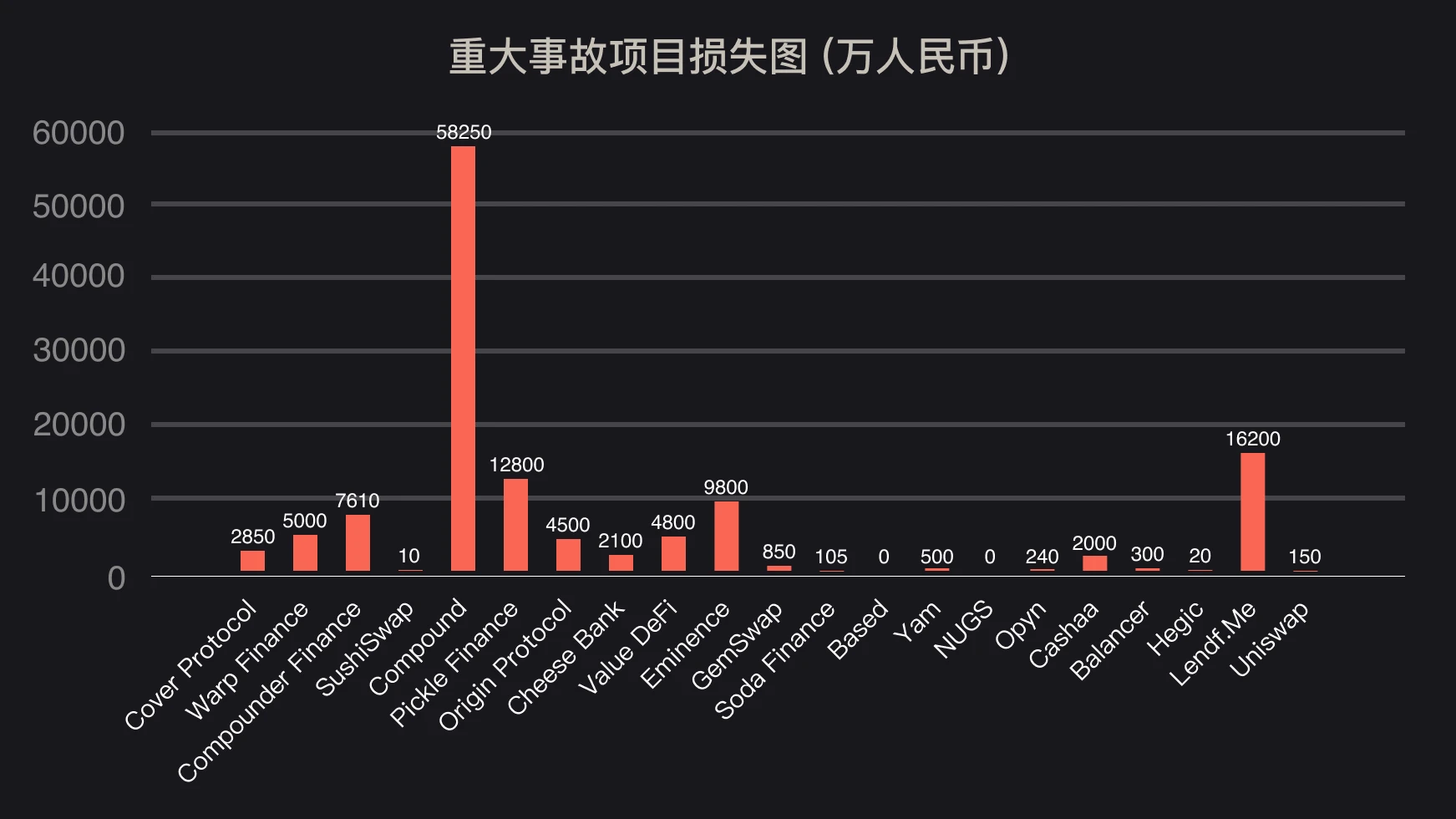
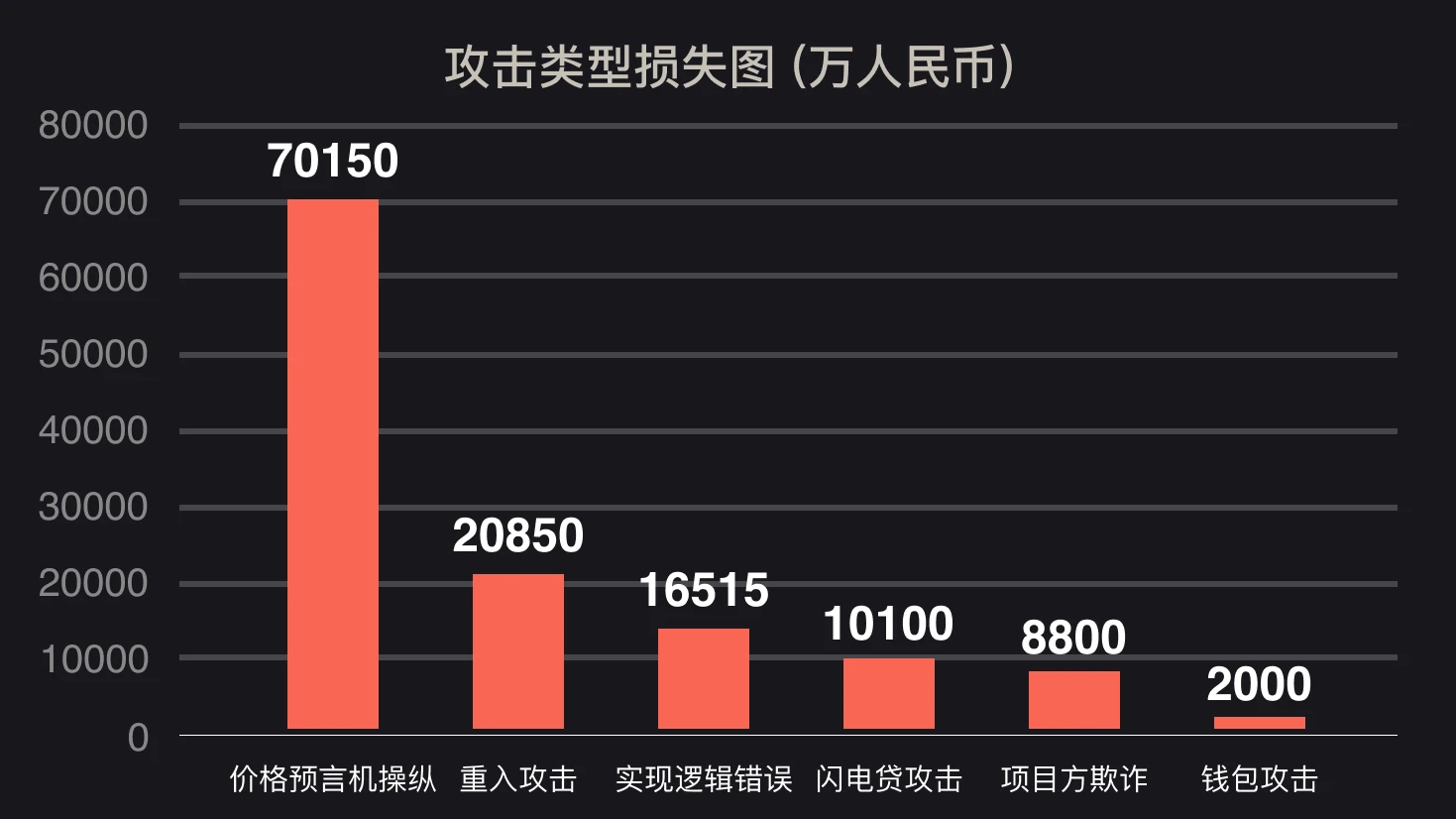
first level title

Table 1: List of major blockchain accident projects in 2020


first level title
Original article, author:CertiK。Reprint/Content Collaboration/For Reporting, Please Contact report@odaily.email;Illegal reprinting must be punished by law.
ODAILY reminds readers to establish correct monetary and investment concepts, rationally view blockchain, and effectively improve risk awareness; We can actively report and report any illegal or criminal clues discovered to relevant departments.