The U.S. Department of Justice (DOJ) announced on Tuesday (February 8) that it has seized $3.6 billion worth of bitcoins related to the 2016 hack of cryptocurrency exchange Bitfinex. Ilya Lichtenstein, 34, and his wife, Heather Morgan, 31, were arrested in New York and charged with conspiracy to commit money laundering and fraud.
event background
event background
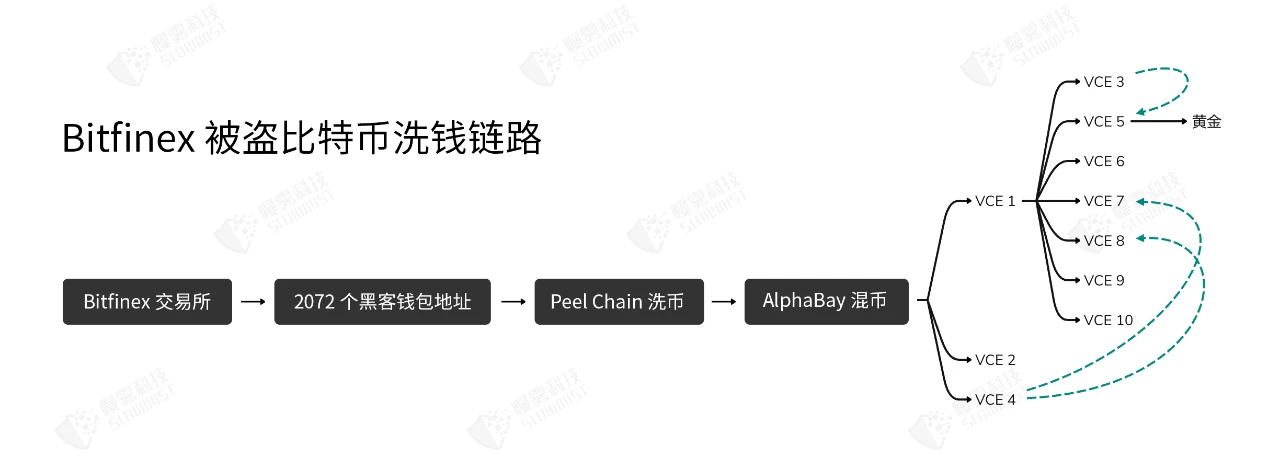
According to the intelligence data analysis held by SlowMist AML, Bitfinex suffered a cyber attack in August 2016.There were 2072 bitcoin transactions transferred out without authorization by Bitfinex, and then the funds were scattered and stored in 2072 wallet addresses. Statistics show that Bitfinex lost a total of 119,754.8121 BTC.It was worth about $60 million at the time of the incident, a total stolen of about $4.5 billion in todays prices.
SlowMist AML once detected a large amount of change in Bitfinex’s stolen funds on February 1, and it was later confirmed that the change was exactly 94,643.2984 BTC seized by the Ministry of Justice, accounting for about 79% of the total amount stolen. Currently, these funds are in custody Wallet address in the US government
first level title
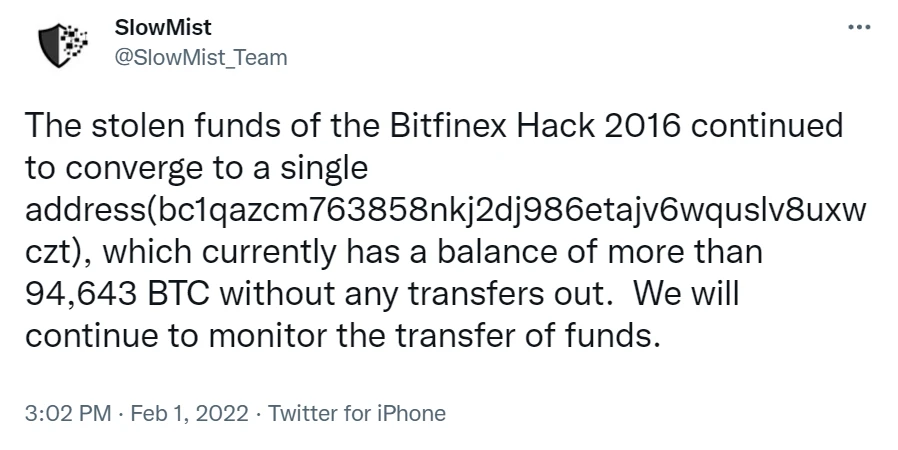
event sorting
SlowMist AML sorted out the statement_of_facts.pdf document published by the US Department of Justice, and shared the key points and details of the case as follows:
1. U.S. law enforcement agencies obtained a document containing more than 2,000 wallet addresses and corresponding private keys by controlling Lichtensteins cloud disk account.The addresses in this document should be the 2072 wallet addresses of the stolen coins mentioned above, and then the US Department of Justice will be able to seize and transfer bitcoins to
bc1qazcm763858nkj2dj986etajv6wquslv8uxwczt.
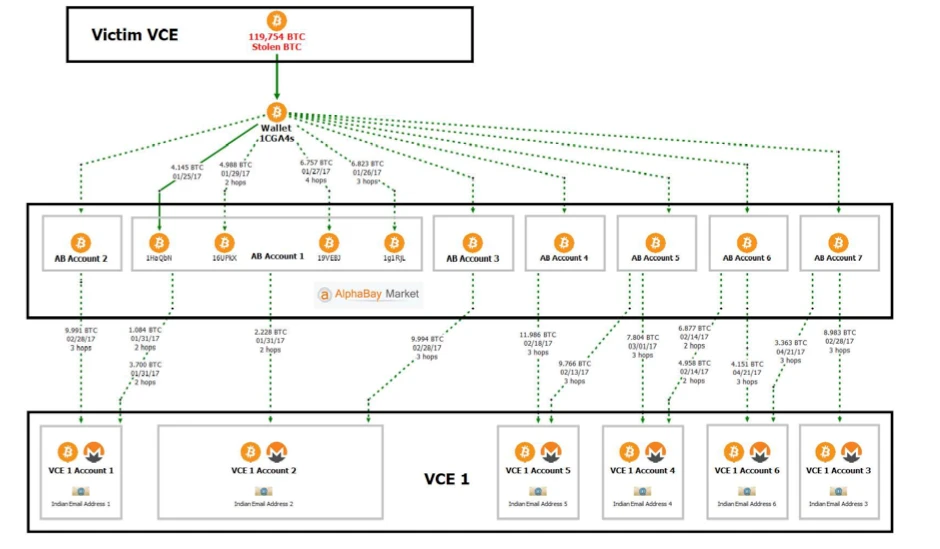
2. From January 2017, the stolen funds began to be transferred. Through peel chain technology, the stolen funds were continuously split and dispersed, and then entered into 7 independent AlphaBay(Dark web trading market, seized and closed by law enforcement agencies in July 2017)The platform account mixes coins, so that BTC cannot be easily tracked. From the results, the bitcoin mixed with AlphaBay is about 25,000 BTC.
3. After mixing the coins, most of the funds were transferred to 8 accounts registered on the exchange-1 (VCE 1), and the mailboxes of these accounts all used the same Indian mailbox service provider. In addition, these 8 accounts have used the same login IP, and they were all registered around August 2016.Whats more deadly is that there is an Excel sheet in Lichtensteins cloud disk, which records various information of these 8 accounts.And 6 of them were marked as FROZEN by him. Statistics from the U.S. Department of Justice found that 8 accounts in Exchange-1 (VCE 1) had frozen assets worth $186,000.
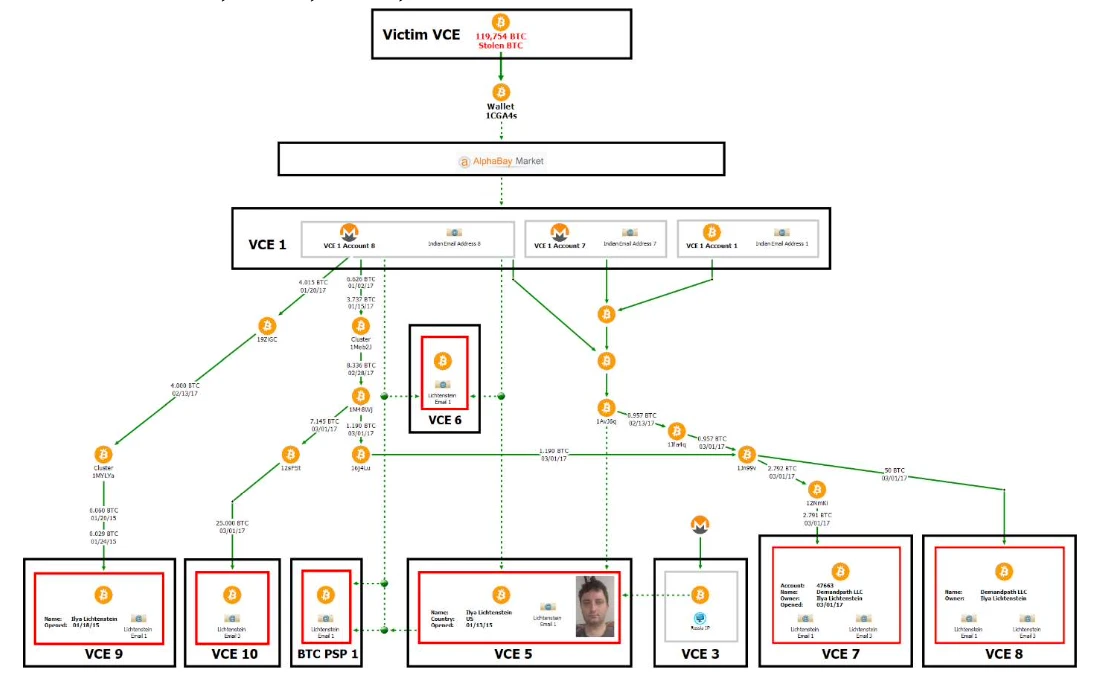
4. Some of the funds were transferred to Exchange-2 (VCE 2) and an American exchange (VCE 4) after the currency was mixed. Some of the accounts registered on these two exchanges also used the above mentioned The Indian mailbox service provider I visited. This information was also found in the Excel spreadsheet in Lichtensteins cloud disk mentioned above. Through VCE 2 and VCE 4, the Lichtensteins successfully exchanged the stolen BTC from Bitfinex into legal currency and pocketed it. However, they have 2 accounts registered with Russian mailboxes on VCE 4. Because they frequently recharge XMR (Monero) and cannot explain the source of funds, the accounts were banned by the platform. Statistics from the U.S. Department of Justice found that assets worth about $155,000 were frozen above.
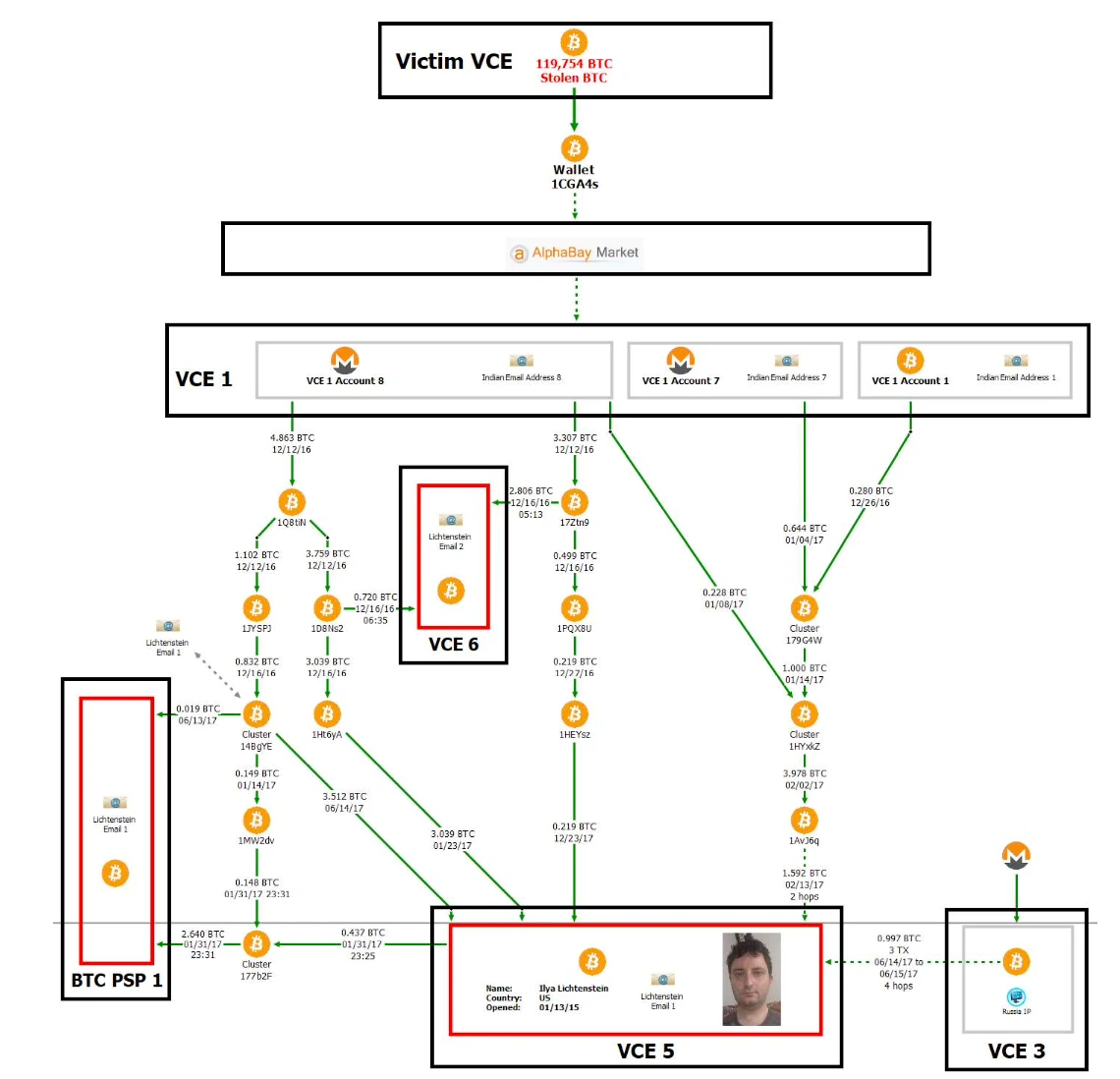
5. Before the account was frozen, most of the funds withdrawn from Exchange-1 (VCE 1) went to another US exchange (VCE 5).Before Bitfinex was stolen, on January 13, 2015, Lichtenstein registered an account on the VCE 5 exchange with his real identity and private email address and performed KYC authentication (real-name authentication).On the VCE 5 exchange, Lichtenstein bought gold with BTC and merchants on the platform, and it was delivered to his real home address.
first level title
first level title
Event doubts
About 6 years have passed since Bitfinex was stolen in August 2016. During this period, we don’t know how the US law enforcement agencies conducted in-depth investigations. From the content of the published statement_of_facts.pdf file, we can find that Lichtenstein’s cloud disk stores a large number of money laundering accounts and details, which is equivalent to a perfect “ledger” and provides strong support for law enforcement agencies to determine the facts of the crime.
But looking back at the big picture, how did law enforcement identify Lichtenstein as a suspect?
Another detail is that the U.S. Department of Justice did not charge the Lichtensteins with allegedly illegally attacking Bitfinex and stealing funds.
References:
References:
https://www.justice.gov/opa/press-release/file/1470186/download
[signed] 22-mj-22 - Statement of Facts.pdf










