basic knowledge
basic knowledge
first level title
case analysis
Hacker address:
Hacker address:
secondary title
0x489...1F4(Ethereum/BSC/Polygon)
0x24f...bB1(BSC)
Ethereum part
With the help of the SlowMist MistTrack anti-money laundering tracking system, we first conduct a general feature analysis of the address.
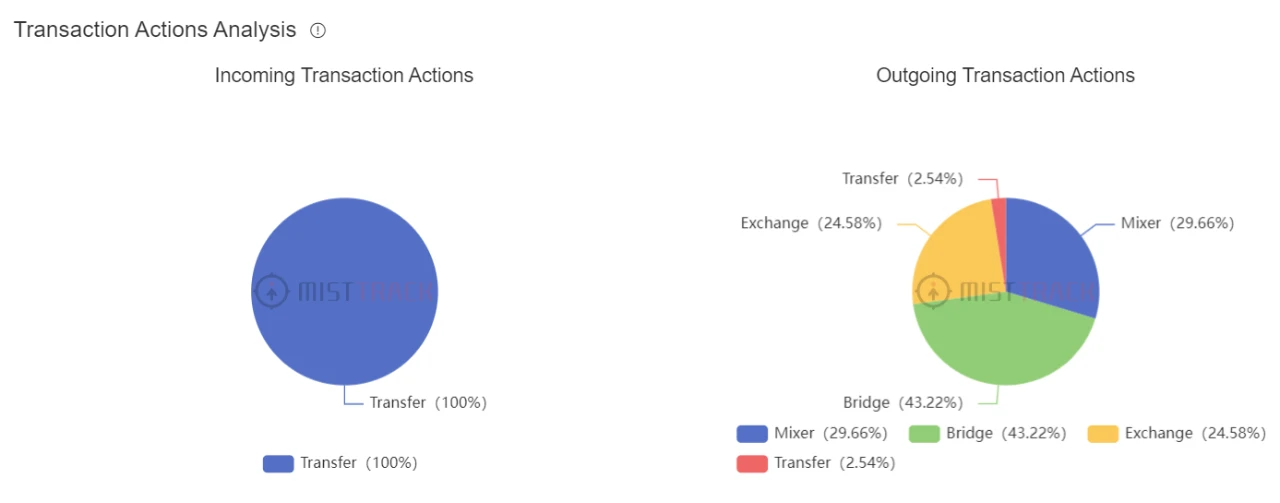
From some of the display results, it can be seen that hackers use more bridges and mixers in transactions, which are very important for us to analyze hacker portraits.
Next, we conducted an in-depth analysis of the funds and behaviors on Ethereum: According to the analysis of the SlowMist MistTrack anti-money laundering tracking system, the hacker transferred 2450 ETH to Tornado.Cash in batches in the form of 5x10 ETH+24x100 ETH, and transferred 198 ETH to FixedFloat, which allows us to keep track of the Tornado.Cash part to keep an eye out.
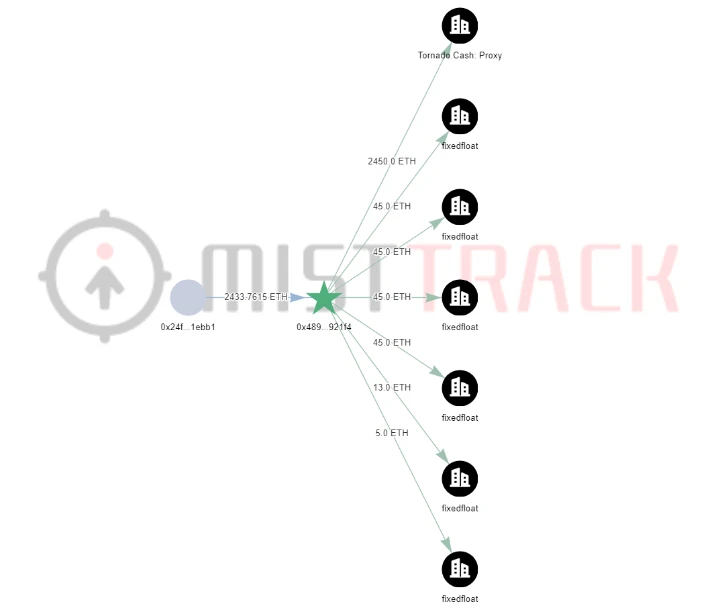
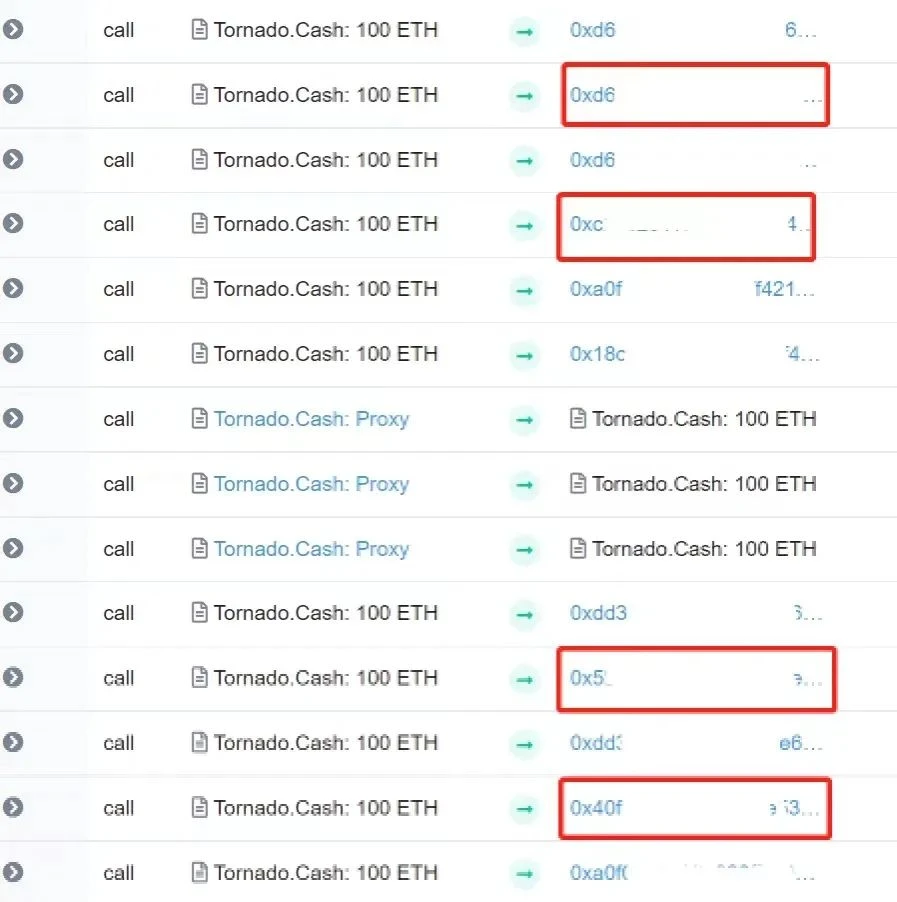
Since we want to try to trace the address that the hacker transfers from Tornado.Cash, we have to start from the time when the first transfer of funds on Ethereum to Tornado.Cash, we found that the time between the first 10 ETH and the second 10 ETH The time span is relatively large, so let’s start the analysis with the small span of 100 ETH.
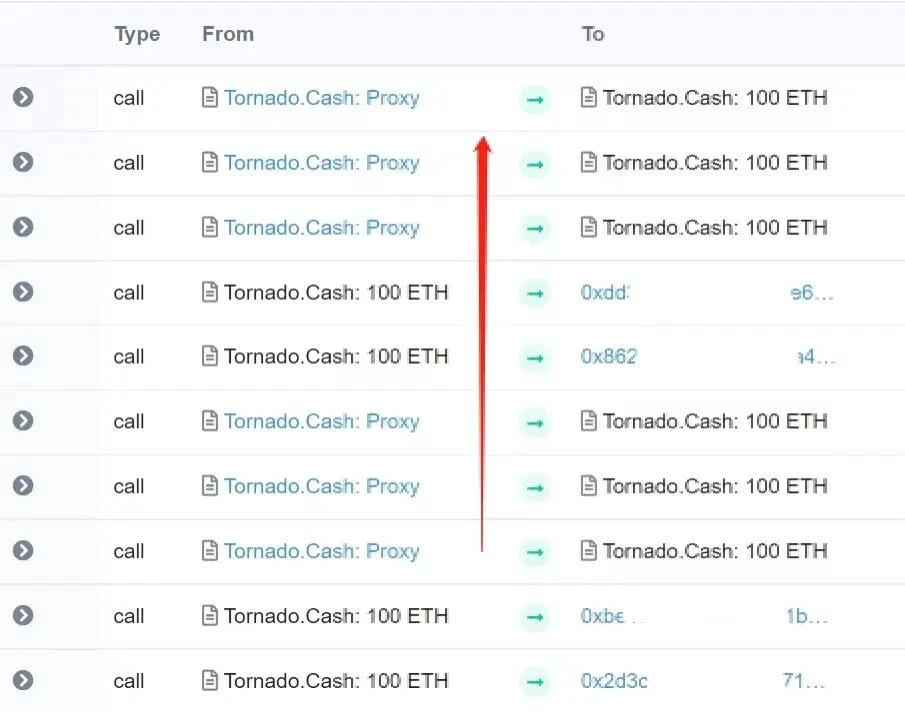
Locate the transaction corresponding to the Tornado.Cash:100 ETH contract, and found that there are many addresses transferred from Tornado.Cash. After the analysis of SlowMist MistTrack, we screened out the addresses that match the timeline and transaction characteristics. Of course, there are still many addresses, which requires us to continue to analyze. But it didnt take long for the first address (0x40F...952) that made us suspicious.
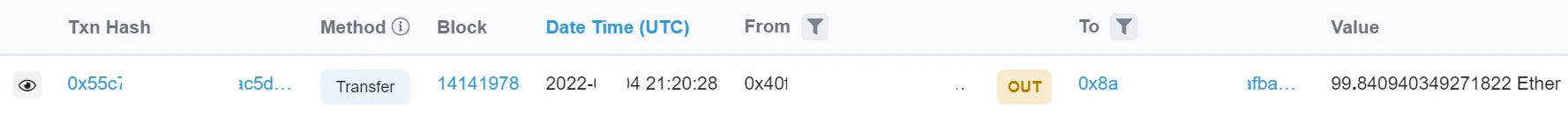
According to MistTracks analysis, the address (0x40F...952) transfers the ETH transferred from Tornado.Cash to the address (0x8a1...Ca7), and then divides the ETH into three transfers to FixedFloat.
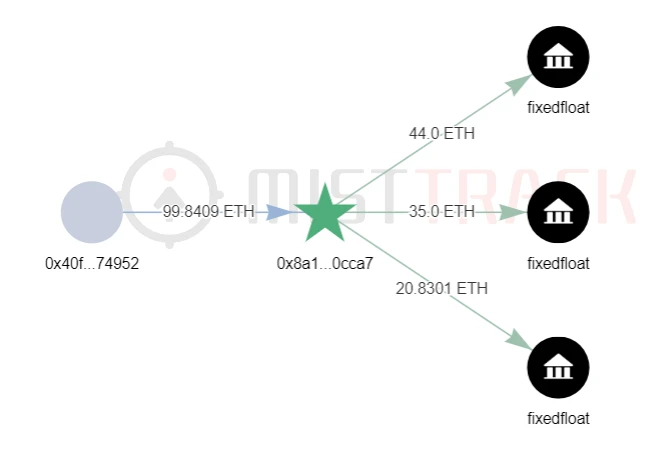
Of course, this may also be a coincidence, we need to continue to verify.
Continuing the analysis, it was found that three addresses have the same characteristics:
A→B→(multiple) FixedFloat
A → (multiple) FixedFloat
secondary title
Polygon section
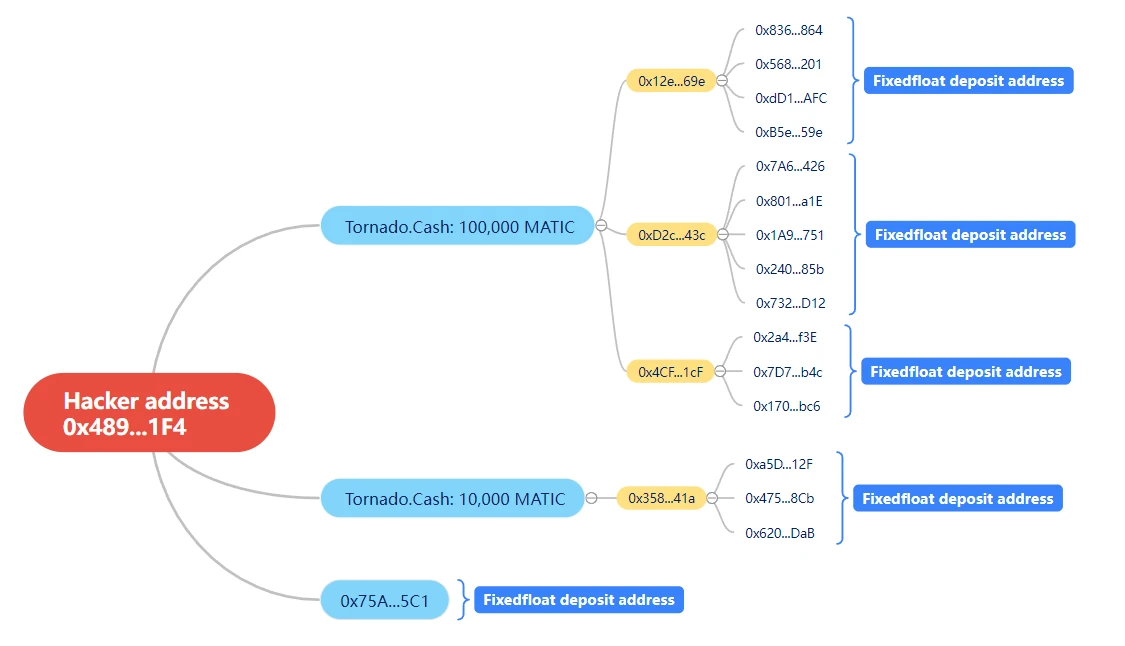
As shown in the figure below, the hacker transfers part of the 365,247 MATIC that he earned to Tornado.Cash in 7 times.
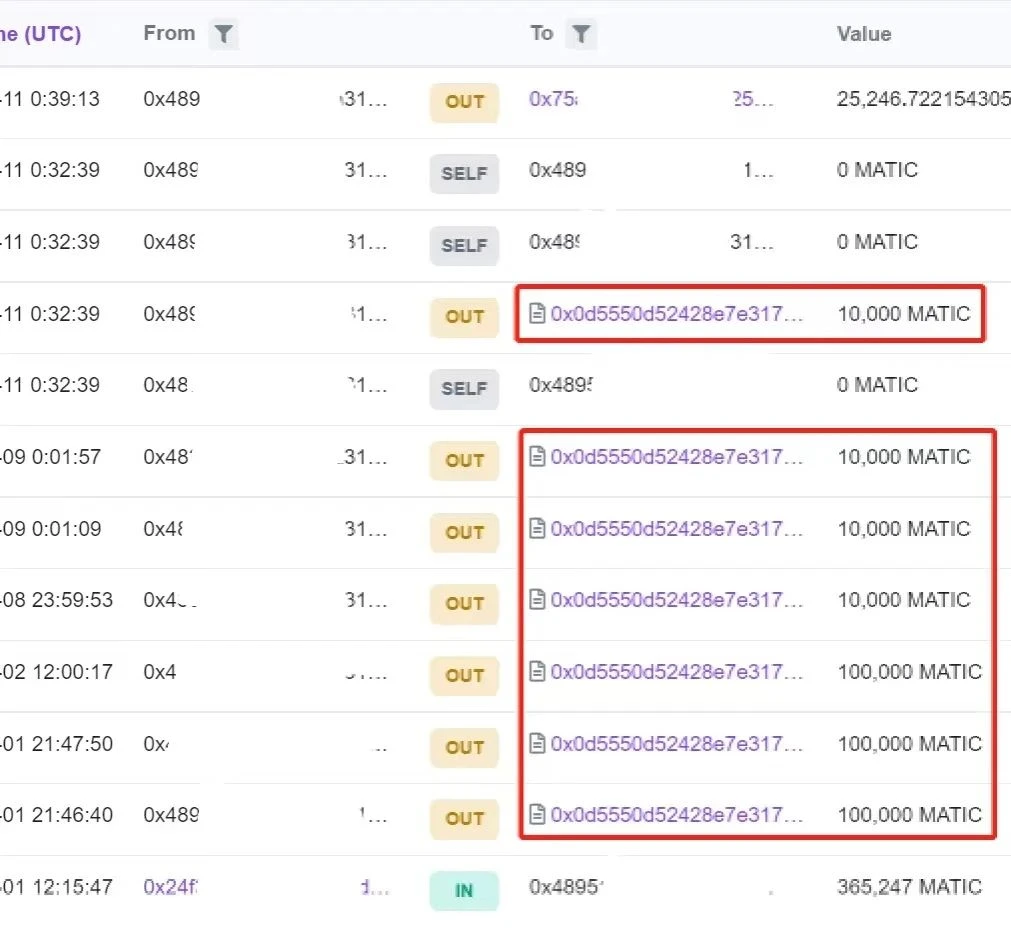
The remaining 25,246.722 MATIC was transferred to the address (0x75a...5c1), and then traced this part of the funds, we found that the hacker transferred 25,246.721 MATIC to FixedFloat, which made us wonder whether the hacker would use the same method to launder coins on Polygon.
We first located the Tornado:100,000 MATIC contract corresponding to the last three transactions in the above figure, and found that there were not many addresses transferred from the Tornado.Cash contract, so we can analyze them one by one.
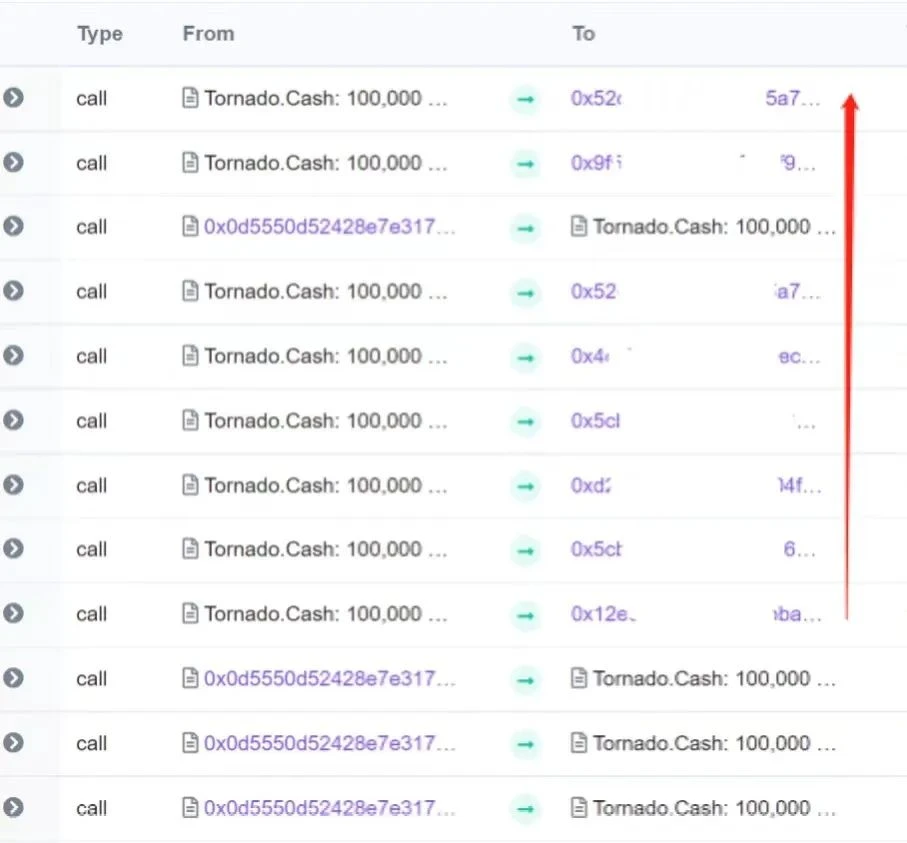
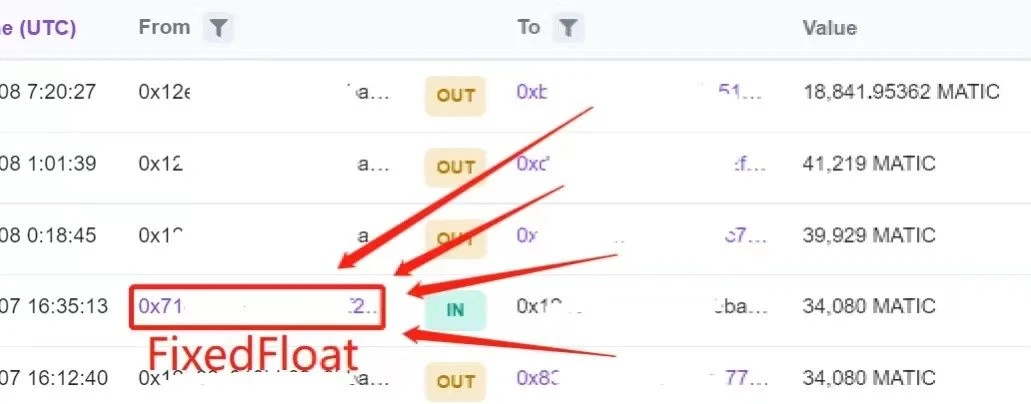
Soon, we found the first address (0x12e...69e) that we thought was problematic. We saw the familiar FixedFloat address, not only the fixedFloat transferred MATIC to the address (0x12e...69e), but also the receiving address of the funds transferred from the address (0x12e...69e) also transferred MATIC to FixedFloat.
secondary title
BSC part
Lets analyze the BSC part below. There are two hacker addresses on BSC, let’s look at the addresses first (0x489…1F4):
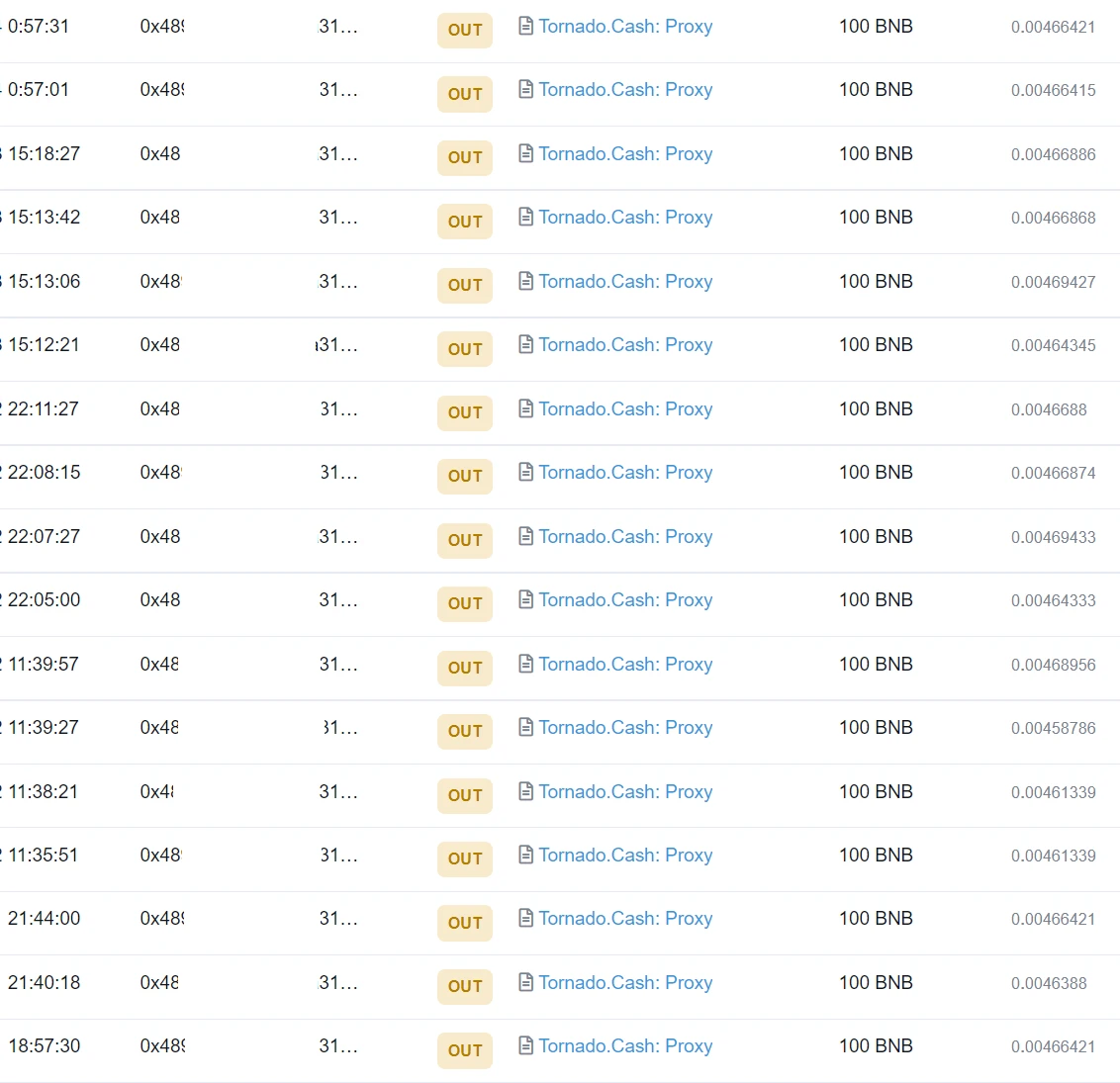
The hacker address transferred 1700 ETH to Tornado.Cash in 17 times, and the time range was relatively consistent. Just when we thought that hackers would repeat their tricks, we found that this is not the case. Similarly, after the analysis and screening of SlowMist MistTrack, we screened out addresses that conform to the timeline and transaction characteristics, and then made breakthroughs one by one.
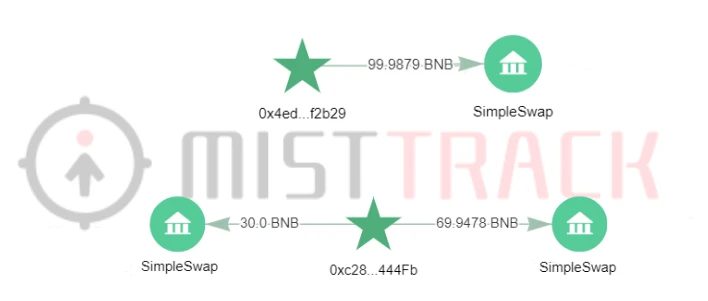
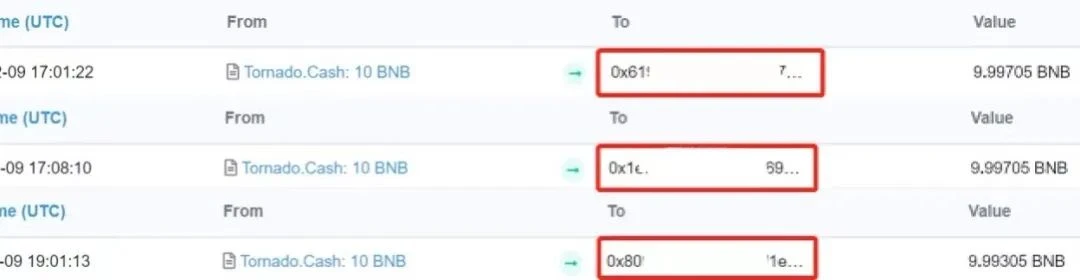
During analysis, the address (0x152…fB2) caught our attention. As shown in the picture, according to SlowMist MistTrack, this address transferred the ETH transferred from Tornado.Cash to SimpleSwap.

After continuing to analyze, it is found that the hacker has changed the platform, but the characteristics of the method are still similar:
A→SimpleSwap
A→B→SimpleSwap
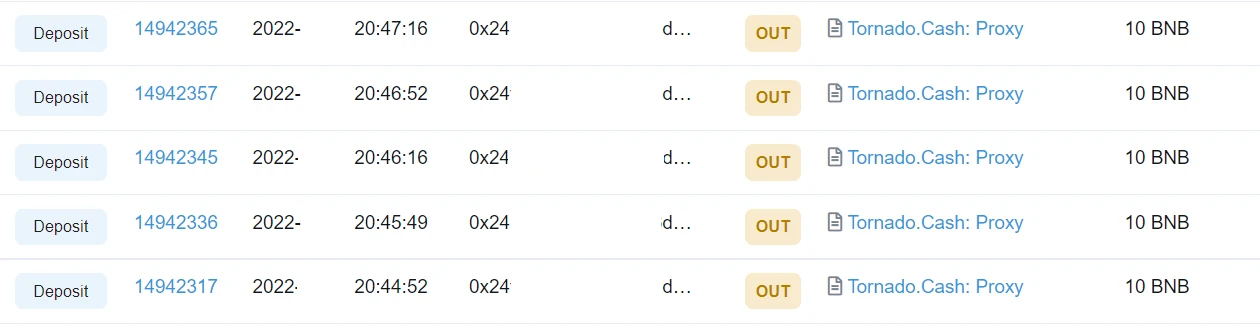
Another hacker address (0x24f…bB1) was transferred to Tornado.Cash in units of 10 BNB.
Summarize
Summarize
This article mainly starts with a real case, analyzes and concludes how hackers try to use Tornado.Cash to clean the stolen funds on different chains. This coin laundering method is very similar, and the main feature is After the currency is transferred to the commonly used mixed currency platform (FixedFloat/SimpleSwap/Sideshift.ai) either directly or through an intermediate address. Of course, this is just one of the methods of laundering coins through Tornado.Cash, and more methods are still waiting for us to discover.
To analyze the results more efficiently and accurately, you must use tools. With more than 200 million wallet address tags, SlowMist MistTrack anti-money laundering tracking system can identify various wallet addresses of global mainstream trading platforms, such as user recharge addresses, warm wallet addresses, hot wallet addresses, cold wallet addresses, etc. The MistTrack anti-money laundering tracking system can perform feature analysis and behavioral portraits on any wallet address, which plays a vital role in the analysis and evaluation of anti-money laundering. Strong technical support.










