background overview
On August 3, 2022, a large-scale coin theft incident occurred on the Solana public chain, and a large number of users were transferred SOL and SPL tokens without their knowledge. The SlowMist security team immediately intervened in the analysis, and analyzed the Slope wallet application at the invitation of the Slope team. The analysis showed that: the version of the Slope wallet released on or after June 24, 2022 sent private messages to the third-party application monitoring service. Phenomenon of key or mnemonic information.
However, from the investigation of the Slope wallet application to the present, it is impossible to clearly prove that the root cause of the incident is the problem of the Slope wallet, so the SlowMist security team began to analyze and collect evidence from the Slope server.
Analysis process
After the incident, all parties focused on investigating the root cause of the incident and the possibility of tracking and saving funds. So the SlowMist security team formulated relevant plans and began to investigate and analyze from the off-chain and on-chain parts.
In the direction of incident root investigation, the SlowMist security team focused on the analysis and forensics of the Slope server. There is a lot of complicated work that needs to be advanced, and more clear evidence is needed to explain the root cause of this large-scale theft.
For the possibility of fund tracking and rescue, the SlowMist security team mainly relies on the tracking and analysis capabilities of MistTrack (https://misttrack.io/), the ability to label data and combine intelligence capabilities to try their best to identify and track hackers. Behavior on the chain. And also communicated with the Slope team about the possibility of rescue. The Slope team is also trying to communicate with hackers, hoping to encourage hackers to return assets by issuing bug bounties, and jointly maintain the healthy development of the Solana ecosystem.
This article only synchronizes phased investigations with community users, and there is still a lot of analysis work in progress, and it is constantly advancing. Not only SlowMist, but also other third-party security teams, and some special forces are also working hard to help with the investigation, hoping that this incident will eventually come to a relatively clear conclusion.
Note: The Sentry service mentioned in this article refers to the Sentry service deployed privately by the Slope team, instead of using the official interface and service provided by Sentry.
some doubts
Before synchronizing the analysis, lets answer some questions in the analysis process of the previous article:
1. Is Sentry’s service collecting mnemonic phrases from users’ wallets a common security issue?
Answer: Sentry is mainly used to collect abnormal or error log information that occurs when related application services are running. In the case of incorrect configuration, unexpected data may be collected, such as private keys or mnemonic words. So not a universal security issue. Developers must remember not to enable Debug mode in the production environment when using third-party application monitoring services.
2. Phantom uses Sentry, so will the Phantom wallet be affected?
Answer: Although Phantom uses a third-party application monitoring service, the SlowMist security team has not found any obvious behavior of uploading private keys/mnemonic words by Sentry through monitoring the historical versions of the Phantom wallet.
3. According to the research data provided by Solana Foundation, nearly 60% of the stolen users used Phantom wallets, about 30% of the addresses used Slope wallets, and the remaining users used Trust Wallet, etc. What is the reason for these 60% stolen users to be hacked? Woolen cloth?
Answer: After comparison, it is found that the addresses (including HD addresses) derived from the private key and mnemonic words on the server intersect with the victims address. There are 5 ETH addresses and 1388 Solana addresses. According to the current investigation, there is no clear evidence to explain why some other users wallets were hacked.
4. As Sentry is a very widely used service, could it be that the official Sentry has been hacked? This has led to targeted attacks on the cryptocurrency ecosystem?
Answer: At present, there is no evidence that the official Sentry has been invaded and attacked. The Sentry used by the Slope wallet is an internally built service, so it has no direct relationship with the official service being invaded.
Off-chain analysis section
The off-chain SlowMist security team mainly focuses on checking the possibility of intrusion on off-chain servers and related backends. The focus of the work is to check the risk of peripheral server assets on the Slope server, check the intrusion traces of the server, and analyze the Sentry (PostgreSQL) database. Server mirroring analysis, DNS hijacking possibility analysis. The investigation and analysis are as follows:
1. Peripheral server asset risk investigation
After the Slope team knew that the Slope wallet returned the mnemonic phrase and private key information, it immediately shut down the services related to the Slope wallet. Therefore, the services related to the Slope wallet can no longer be directly accessed. The SlowMist security team relies on Internet search engines and other tools to collect information on Slope’s peripheral server assets, including the subdomain names and IPs under the slope.finance domain name for simulated penetration test analysis and investigation. From the possible intrusion risk points on the periphery, no risk points that can be directly invaded have been found through analysis and penetration testing.
2. Check the intrusion traces of the server
It mainly conducts internal investigations on third-party application monitoring servers, including server login logs, system historical operation commands, suspicious processes, suspicious network connections, suspicious system scheduled tasks, data deletion and acquisition operations, etc. There are also 5 Docker services inside the server. The same intrusion trace investigation. The investigation found several suspicious login IPs: 113.*.*.*, 114.*.*.*, 153.*.*.*, these IPs had accessed the background of the third-party application monitoring service before 06.24. Although this happened before the time (06.24) when the private key and seed phrase were returned, it is still suspicious.
3. PostgreSQL database analysis
Since the mnemonic and private key are returned to the server by the third-party application monitoring service of Slope Wallet, the SlowMist security team also analyzed the possible locations of the private key or mnemonic in the server, and found that the private key or Mnemonic words are likely to be stored in the following positions:
In Sentrys database table
In the database log of PostgreSQL
Among the deleted data of the mirror disk
In the data file of the Docker runtime
During the analysis, it was found that the third-party application monitoring service used the PostgreSQL database, and the data field of the nodestore_node table contained the private key and mnemonic data collected by the third-party application monitoring service. The following information was obtained after analysis and investigation:
The data content of the private key and mnemonic phrase is recorded in the database of the nodestore_node table from 2022.7.28 to 2022.8.5.
Through decrypting and analyzing the data, the SlowMist security team found that the earliest data recorded in the private key or mnemonic data was the data uploaded on June 29, 2022, which means that the data collected by Sentry on June 29 was delayed by one month It was only stored in the nodestore_node table of the PostgreSQL database on 2022.7.28, but this part of the delayed data accounted for less, and most of the private key and mnemonic collection time was concentrated on 2022.07.28 - 2022.08.05.
After further investigation of the database operation log, it was found that before 7.28, there was a record of SQL statement execution failure in the nodestore_node table. The reason was a key-value conflict. After in-depth investigation and communication, it was found that the data was not written due to an error in the Kafka service.
Since part of the data cannot be recovered temporarily during log recording and data recovery, the data needs to be further repaired, so the data that can be fully recovered is prioritized for decryption. The number of decrypted addresses is 189 ETH addresses and 4914 Solana Address, there are 5073 sets of mnemonic words, and the wallet address of the hacking incident on the chain has 42 ETH addresses and 9231 Solana addresses. After comparison, it is found that the private key on the server and the mnemonic words are derived from the address (including HD address) The addresses intersecting with victims are 5 ETH addresses and 1388 Solana addresses. (This does not contain a small number of data that needs to be repaired before decryption)
In the database operation log, it was also found that com.slope.game, another internal test application, also had private key and mnemonic report data in March, but this internal test application has not been released to the public.
4. Server image analysis
The SlowMist security team analyzed the image of Sentrys cloud server and recovered the deleted data on the server disk, and found private key and mnemonic information in the recovered data.
5. Possibility Analysis of DNS Hijacking
The SlowMist security team has used the capabilities of all parties and global intelligence resources, including the query and analysis of DNS resolution data. At present, there is no clear evidence to prove that the domain name o7e.slope.finance has ever had a DNS hijacking incident.
Staged conclusions of off-chain investigation and analysis:
As far as the current investigation and analysis are concerned, no risk points where peripheral servers can be directly invaded have been found; no traces of server intrusion have been found, but suspicious IPs (113.*.*.*,114.*.*.* ,153.*.*.*) Still need to continue the investigation; DNS hijacking is less likely; private key and mnemonic information have been found in database tables, database log files, and recovered data from disk deleted files.
On-chain analysis section
The part on the chain mainly focuses on risk fund assessment, stolen fund transfer and hacker trace analysis, focusing on the following points:
1. Venture capital assessment
According to the stolen funds of the Solana chain, ETH chain, and BSC chain, the SlowMist security team divides the risk funds into the following two categories:
Risky Funds: Funds where the hacker has address authority.
Suspected Risk Funds: Funds where hackers may have address authority.
Venture capital assessment based on the following list of addresses (mainly Solana chain, ETH chain):
Stolen address mnemonic maps to addresses of other chains
The address derived from the stolen address mnemonic through the derivation path
Exclude the list of venture capital addresses, and conduct suspected venture capital assessments based on the following address lists (mainly Solana chain, ETH chain):
The address where the mnemonic/private key record exists on the Slope server
The mnemonic phrase existing on the Slope server is mapped to the address of other chains
The address derived from the mnemonic phrase existing on the Slope server through the derivation path
No large amounts of funds that could be transferred at risk and funds that may be at risk were found.
2. Stolen funds statistics
In order to avoid the impact of some junk coins on stolen funds, we only count the stolen funds of mainstream currencies in the statistical process:
Solana chains: SOL, USDC, USDT, BTC, and ETH.
ETH chains: ETH, USDT, USDC, and PAXG.
The value of the stolen currency is the price on the day of the theft (00:00 AM on August 3, UTC time).
1 SOL = $38.54
1 BTC = $22,846.51
1ETH = $1,618.87
1 PAXG = $1,759.64
1 BNB = $298.36
Analyze the addresses (including HD addresses) derived from the decrypted private key and mnemonic on the Slope server and the victim addresses on the chain, and the intersection addresses include 5 ETH addresses and 1388 Solana addresses. The statistics of the stolen funds for these overlapping addresses are as follows. The stolen funds account for 31.42% of the total stolen funds.
3. Fund transfer analysis
Solana chain:
The funds have not been further transferred as of the time of publication.
ETH chain:
21,801 USDT was transferred to the personal wallet address (according to the behavior characteristics on the chain and MistTracks labeling ability, this address is suspected of being an OTC transaction address). The SlowMist security team is communicating and cooperating with all parties to trace the identity of the hacker.
Most of the remaining funds are converted to ETH and transferred to Tornado.Cash.
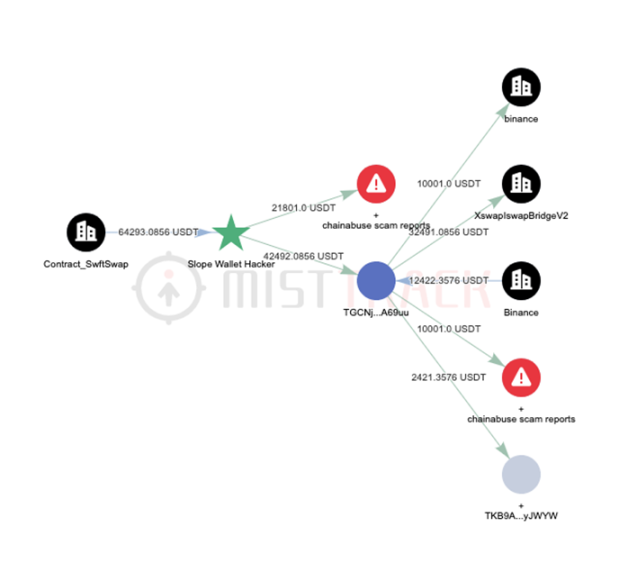
BSC chain:
The funds have not been further transferred as of the time of publication.
4. Timeline analysis on the hacker chain
According to the behavior of hackers on the chain, the timeline is sorted out as follows:
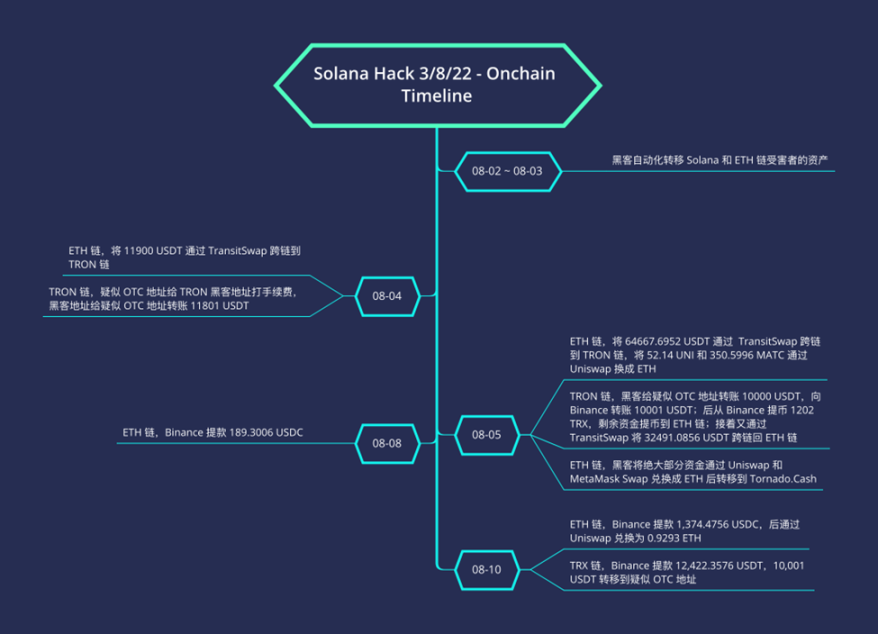
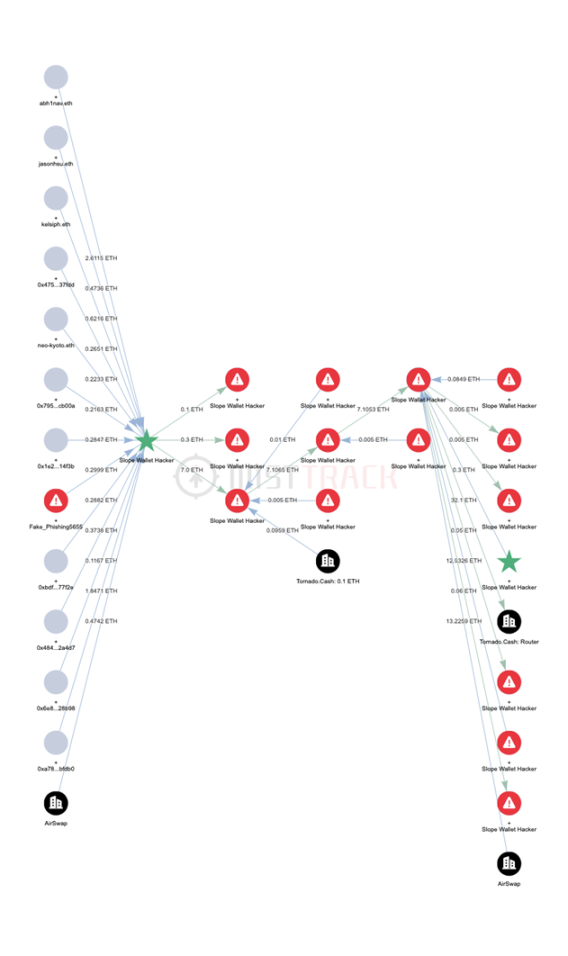
5. Hacker trace analysis
The list of hacker addresses is as follows:
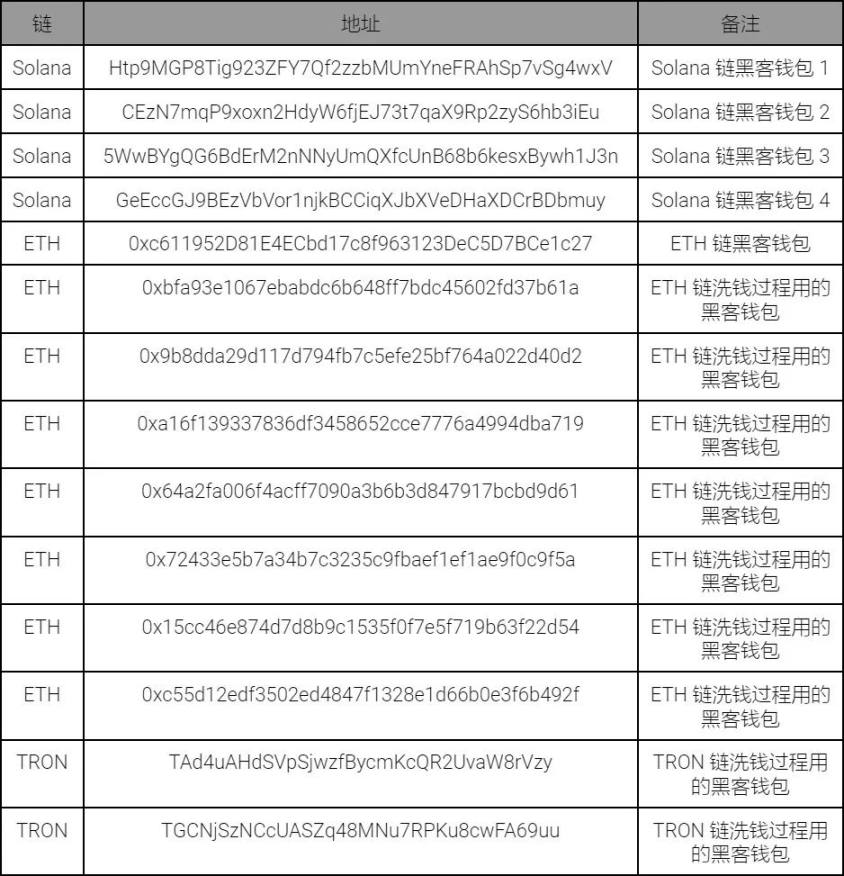
The list of suspected hacker addresses is as follows:
first transfer in
The first transfer transactions on the chain of Solana chain hacker wallets 1, 2, 3, and 4 are all transfers of 0.1 SOL from Solana chain suspected hacker wallets. According to the analysis of traces on the chain, it is estimated that the suspected hacker wallet on the Solana chain may be the hackers address, and it is more likely to be the victims address.
Hackers use tools in the money laundering process
TransitSwap
Uniswap
MetaMask Swap
How hackers launder money
Transfer to suspected OTC personal wallet address (mentioned above).
Transfer to Tornado.Cash.
Correlation between hacker address and exchange/platform
directly related to:
TRON chain, hackers deposit USDT to Binance on August 5
Deposit address: TE4bkS2PYqWxijgh5eqEz9A5jLn7HcS6fn
Deposit transaction: b6615bf10b2e619edc9315a08f89732664adc9d385c980f77caa6e82872fe376
TRON chain, hackers withdraw TRX from Binance on August 5
Withdrawal transaction: 0e012643a7db1b8c5d1f27447b16e313d4b3f89efaa22b3661188fe399cd2d0e
ETH chain, hackers withdraw ETH from Binance on August 5
Withdrawal transaction: 0xd035e009173e968d8f72de783f02655009d6f85ef906121e5b99b496a10283dd
ETH chain, hackers withdraw USDC from Binance on August 8
Withdrawal transaction: 0xff60f24f8ebd874a1e5da8eae44583af554af9a109a9bd7420da048f12c83cdc
ETH chain, hackers withdraw USDC from Binance on August 10
Withdrawal transaction: 0xc861c40c0e53f7e28a6f78ec9584bfb7722cec51843ddf714b9c10fc0f311806
TRON chain, hackers withdraw USDT from Binance on August 10
Withdrawal transaction: 10c4186e4d95fb2e4a1a31a18f750a39c0f803d7f5768108d6f219d3c2a02d26
Indirect connection:
Solana chain suspected hacker wallet withdraws SOL from Binance on January 8
Withdrawal transaction: 668jpJec7hiiuzGDzj4VQKSsMWpSnbzt7BLMGWQmrGvHVQQbNGc3i1g8dCj2F5EAxFT8oDG5xWPAeQUMEMBTjhZs
The Solana chain is suspected to have traces of hacker wallets interacting with the Solrazr IDO program
Transaction: 2LxLhL7oAiTyHGrAXCZEJyazQQLM7veaKvqUZL6iPkonL4wPLHcwV66MFX3ERyWvJtdd2wFdKfgKUuT1oAv2XepK
image description
Intelligence association of suspected OTC personal wallet addresses
According to the relevant information obtained by SlowMist, the suspected OTC personal wallet address (TGBrAiVArhs5Cqp2CGMYUpSmkseznv1Ng7) is related to multiple cases of money laundering in China, including phone fraud, USDT theft and TRC20 theft.
Attachment - Analysis data source on the chainHacking Solana chain transaction record summary tableOriginal link










