
Exit scam, what we commonly call project runaway. Also known vividly as Rug Pull, it is a criminal fraud method in the Web 3.0 field.
The common practice of Rug Pull is to create false transaction volume and user numbers after creating a seemingly legitimate DeFi project to improve the reputation of the project and attract more investors into the project. After reaching a certain scale, the fraudster or team will suddenly withdraw a large amount of funds in the project and close the project, eventually causing the tokens held by investors to lose value.
While there are plenty of statistics showing the prevalence and impact of exit scams over the years, there are fewer data and reports examining their characteristics and perpetrators. And research like this could improve anti-money laundering (AML) efforts, boost consumer protection, and the integrity of the Web 3.0 marketplace as a whole.
By studying the full cycle of exit scams from start to finish, we can better dissect the structure of the scams and understand the underlying risk factors and commonalities that lead them to exist. By identifying these signals and indicators, we can adopt smarter security approaches and strategies to more effectively protect the Web 3.0 world.
first level title
concept definition
For the purpose of this research, we define a Rug Pull as: a project with criminal plan and purpose that actively uses marketing and hype to defraud investors and then has team member(s) siphoning their funds.
first level title
methodology
first level title
crime analysis
Hard Rug Pull must occur along with internal problems within the project team. It is not difficult to understand that if the team is responsible and there are no signs of running away, the incident will be considered a hacking incident.
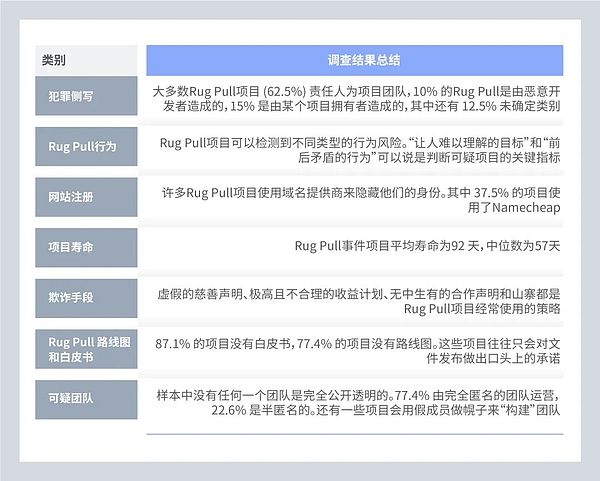
In our research on Rug Pull, runaway projects are divided into four categories: project team runaway, malicious developer sabotage, project owner committing crimes, and unknown personnel or teams committing crimes. Definitions and conclusions for each category are further detailed below:
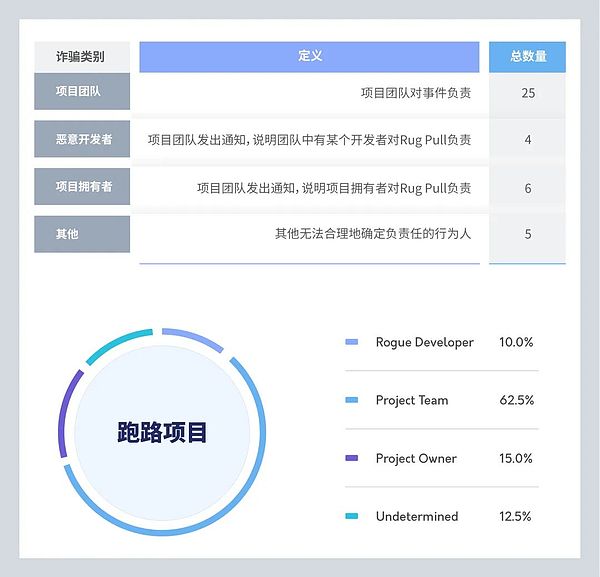
This research highlights the importance of background checks when evaluating new projects and their associated risks. Since the majority of rug pulls are made by project teams, it is critical to consider the teams motivations and their track record before investing in a project.
Rug Pull was active for an average of 93 days before the ultimate runaway scam occurred. We need to be wary of newly deployed projects where developers are intentionally anonymous or completely unknown, with no commitment to transparency or decentralization.
To combat such scams, reduce risk, and help users make informed decisions, CertiK has developedKYC Badge Programfirst level title
secondary title
Case Project ①: Team Scam
CertiK investigators interviewed the project leader of an anonymous project (we will refer to this project simply as project ① in the following). During the interview with the program leader, we found several noteworthy points, including the applicants hesitancy and difficulty recalling the names of other members of the program team. They also claim to have little knowledge of the project and its structure.
In addition, the project lead and team members had no previous experience with Web 3.0 and could not provide any explanation for the purpose of the project. They state that the goal of the project is to donate to specific charities, but they have no plans to support charitable initiatives and cannot name specific charities. The charitable statement appears to be merely a marketing ploy or even a bait to attract investors.
secondary title
Item ②: Malicious developer scam
Unlike project ① where the whole team is a scam participant, the person responsible for the scam in project ② is an anonymous developer who stole all project funds alone. The conversation between CertiK and the person in charge of the project ② happened just a few days before the Rug Pull.
Except for the developer, all other members of the project ② have a public relationship with the project. With the in-depth understanding of the project leader, the names and identities of all members of the team were revealed, but even the project leader himself knew nothing about the developers.
The developer is completely anonymous and uses a pseudonym, has never participated in any team-to-team voice or video calls, and has never disclosed any personal information. Because the developer claimed to have rich experience in Web 3.0 and spoke about the projects he had done before, the person in charge believed the anonymous developers rhetoric: most developers are anonymous in the project team, which is not A risk and a problem.
first level title
secondary title
Red Light Signal One: Website Registration
Of the 40 projects analyzed in this article, 37.5% (15) used Namecheap as their domain registrar. Namecheap is a domain privacy provider that lets you register domain names without any personal information. These services may use private service information and randomly generated emails in place of actual contact information associated with the domain name. Its practice of not asking for personal or identifying information to register with the site could be extremely attractive to would-be Rug Pull scammers.
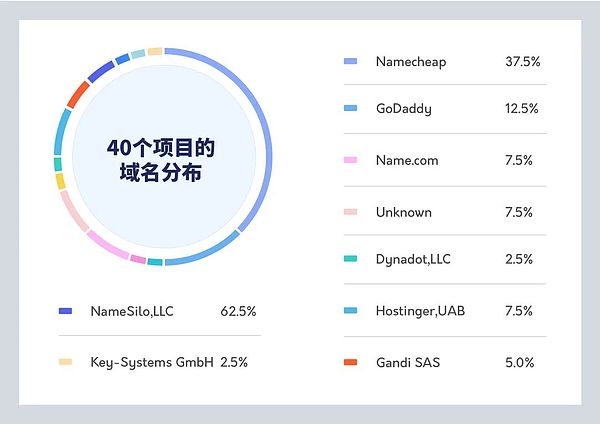
It is worth noting that 4 of the 40 projects did not have an explicit website domain name or no data on the relevant website domain name. Projects registered through Namecheap and unknown projects combined accounted for 45% of the entire sample.
secondary title
Red Light Signal Two: Project Lifespan
Another important variable to consider when researching Rug Pulls is project longevity. In the context of this study, project life is defined as the number of days from the project start date to the Rug Pull (i.e. run time) date. The start date of the project is calculated from social media creation date, on-chain wallet creation date and website date (generally taking the average of available dates).
In our study of these 40 projects, launch dates were identified for 36 of them. The start date and Rug Pull time were collected to calculate the average and median lifespan of the projects: the projects had an average lifespan of 92 days and a median of 57 days.
secondary title
Red Light Signal #3: Deceptive Tactics
secondary title
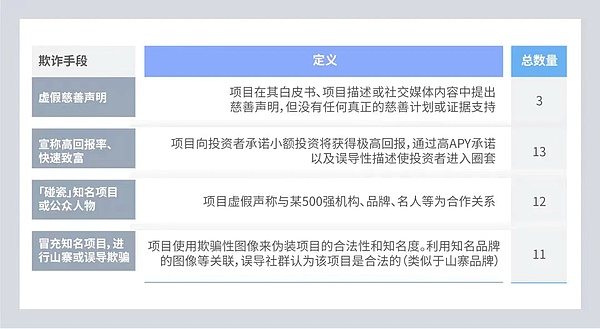
Red Light Signal Four: Roadmap and White Paper
Of the 31 projects that could log onto the website and collect project information data, CertiK found that most of them did not provide roadmaps or white papers on an ongoing basis. Even where roadmaps or white papers exist, the quality can be poor (many grammatical errors, missing information) and often fraudulent information is used in these materials. Projects that are relatively mature with roadmaps and white papers focus on marketing materials that promote false legitimacy.
secondary title
Red Light Five: Suspicious Team Introductions
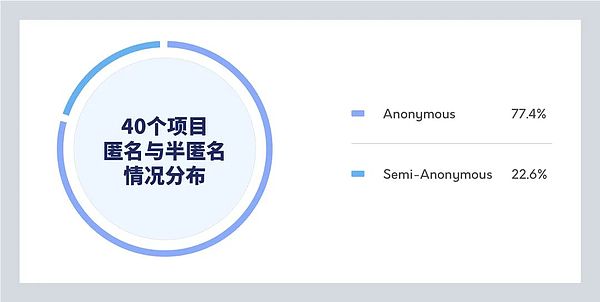
Another important variable in this study was the introduction of the team in the project, and whether the team was anonymous, semi-anonymous or publicly identifiable. In our sample, we collected team profiles for 31 projects, but none of the teams were fully disclosed.
Most projects are completely anonymous, accounting for 24 out of 31 projects (77.4%). The remaining 7 projects were identified as semi-anonymous (22.6% of the sample)—with no other identifiable information other than listing the names of project team members. Photos and names used by other teams were identified as false material after confirmation by our investigators.
first level title
Utilize crime signature analysis, detection and prevention
CertiK identified and analyzed 7 important variables related to the characteristics and trends of Rug Pull projects. These variables share a large number of commonalities, indicating that Rug Pulls operate roughly in the same way.
However, although it has many commonalities, the Rug Pull project is also constantly updating its technology and strategies to adapt to the market and advance with the times in the changing environment.
Here is a summary of the above research results: Most Rug Pull projects have a short lifespan, most of them are carried out by the project team as a whole, and most of them use domain name registrars that do not retain personal information of registrants during the establishment process. Of course, some exceptions were also found in the survey, so the above characteristics can be used as a reference, but not as an absolute standard for evaluation.
Project scammers employ as many tactics as possible to lure potential investors, so its important to do your own due diligence and refer to authoritative information from experts with Web 3.0 security expertise before investing.
Using a third-party security auditor to conduct background checks can increase the efficiency and effectiveness of security measures. CertiKs KYC team is made up of investigative experts. In addition to thorough background checks and risk assessments, CertiK maintains a unique database of Web 3.0 fraudsters and qualitative and quantitative tools through risk indicators to help detect fraud.
Rug pulls are a constant threat to the Web 3.0 ecosystem. Although we identified some high-risk factors from the 40 samples, and our KYC will help high-quality projects stand out, these threats cannot be completely eliminated.
By raising the bar for safety and transparency, CertiK hopes to provide credible proof to those projects that really have ideals, and at the same time, it hopes to help users make informed and correct decisions, and prevent more people from becoming victims of Rug Pull.










