Introduction
Ethereum, as an open and programmable blockchain platform, is not only the infrastructure for digital currency but also provides developers with an environment to build decentralized applications (DApps) and smart contracts. Due to its flexibility and scalability, Ethereum has become a key player in the cryptocurrency ecosystem and has attracted developers and users from around the world.
In the previous issue of Cregis Research, we discussed the value of Account Abstraction (AA), which led to a complex topic. In June, Vitalik Buterin, the founder of Ethereum, pointed out in his blog that Ethereum is currently facing some important challenges and issues that need to be addressed in order to further its development. Otherwise, Ethereum will be doomed to failure. These three directions of transformation are: smart contract wallets, privacy protection, and Layer 2 scalability. After a successful transformation, Ethereum will improve in terms of performance, user experience, and privacy protection.
Of course, these transformations will also bring new challenges. The issues and significance of smart contract (CA) wallets have been analyzed in the previous article. Cregis Research summarizes the remaining problems and selects several key points that are closely related to everyone's daily experience, so that we can review Vitalik's views from half a month ago.
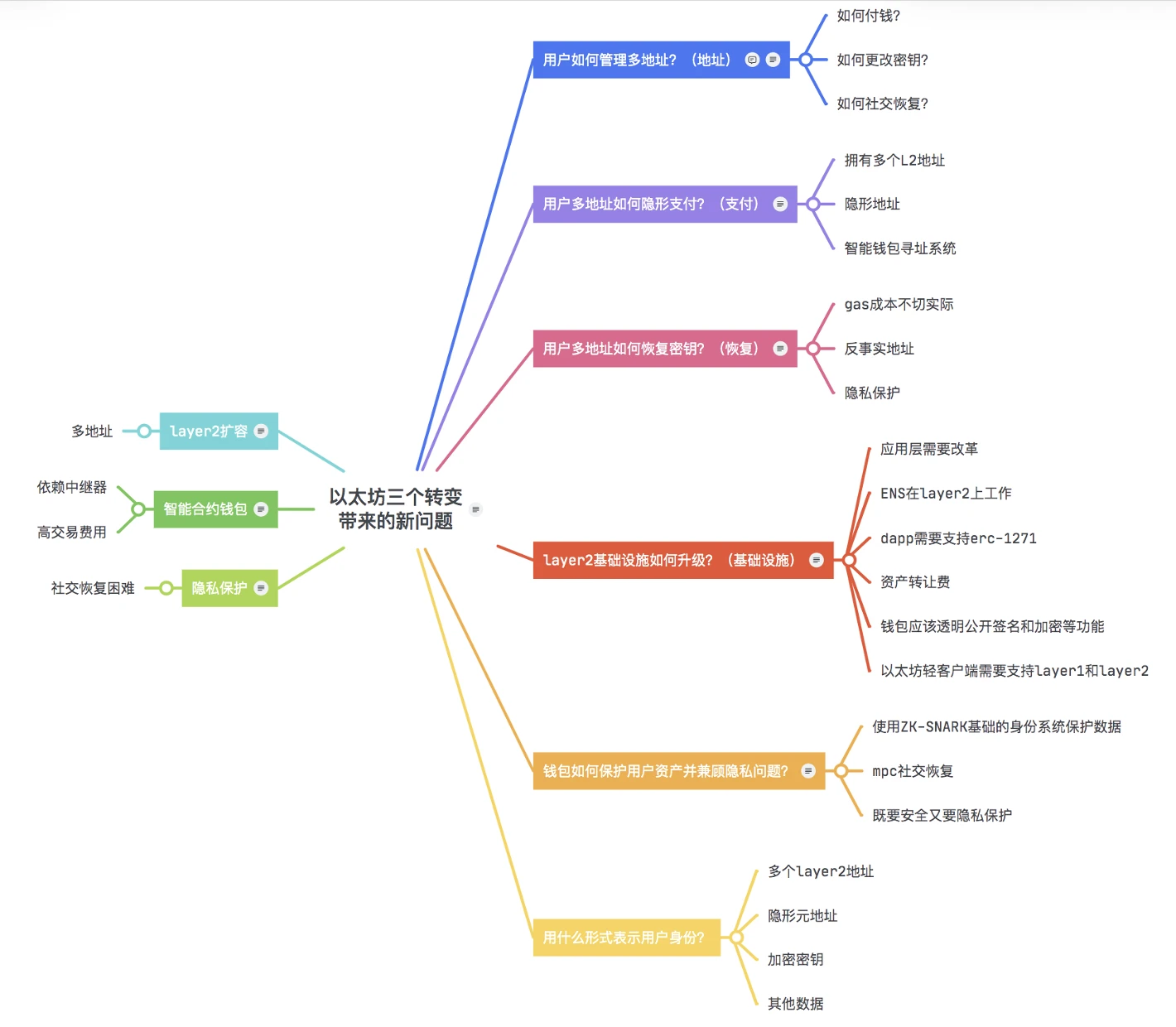
New problems brought by the three transformations of Ethereum
Why does Ethereum need to transform?
The main reasons for Ethereum's need for transformation are scalability, security, and privacy protection challenges.
First, let's review the discussion in the previous issue of Cregis Research: Cregis Research: Ethereum Account Structure Archaeology and the Value of Account Abstraction. It mentions that Ethereum, running in a decentralized environment, still faces the biggest pain point: the linear environment cannot execute high-concurrency transactions and complex code compilation, which is the scalability challenge.
Due to the limited transaction processing capacity of Ethereum, when network traffic increases, transaction costs become high. These high transaction costs hinder Ethereum's adoption in the mainstream market, so Ethereum needs to improve its processing capacity and reduce transaction costs through L2 scaling solutions such as rollups.
Second, wallet security is also an important issue. EOA wallets (represented by various plugin wallets) that simply generate public-private key pairs through a seed phrase have been constantly hacked, from the ARB airdrop address leakage to Twitter KOL complaining about wallets being emptied by hackers. Individual users' demands for asset security are increasing while they are unwilling to sacrifice user experience (enterprise users may choose fully self-managed MPC solutions for asset security and are willing to sacrifice convenience of on-chain interactions). Therefore, Ethereum needs to transform wallet security and promote industry security standards for smart contract wallets (such as EIP-4337), providing individual users with stronger security and convenience.
Lastly, privacy protection is another key challenge. All transactions on Ethereum L1 are public because of the link between EOA and assets. Whether it's ordinary individual users, whales, or corporate institutions, all may suffer from the frustration of having their asset addresses marked and tracked. Therefore, Ethereum needs further improvement to implement non-malicious privacy computation, ensuring that not only on-chain assets but also on-chain identities, credit systems, and DID information can be protected. At the same time, it needs to ensure that when malicious events occur, there are mechanisms in place to prevent wrongdoers from evading traceability and smoothly liquidating.
Three Most Important Questions (Cregis Research Summary with Added Opinions)
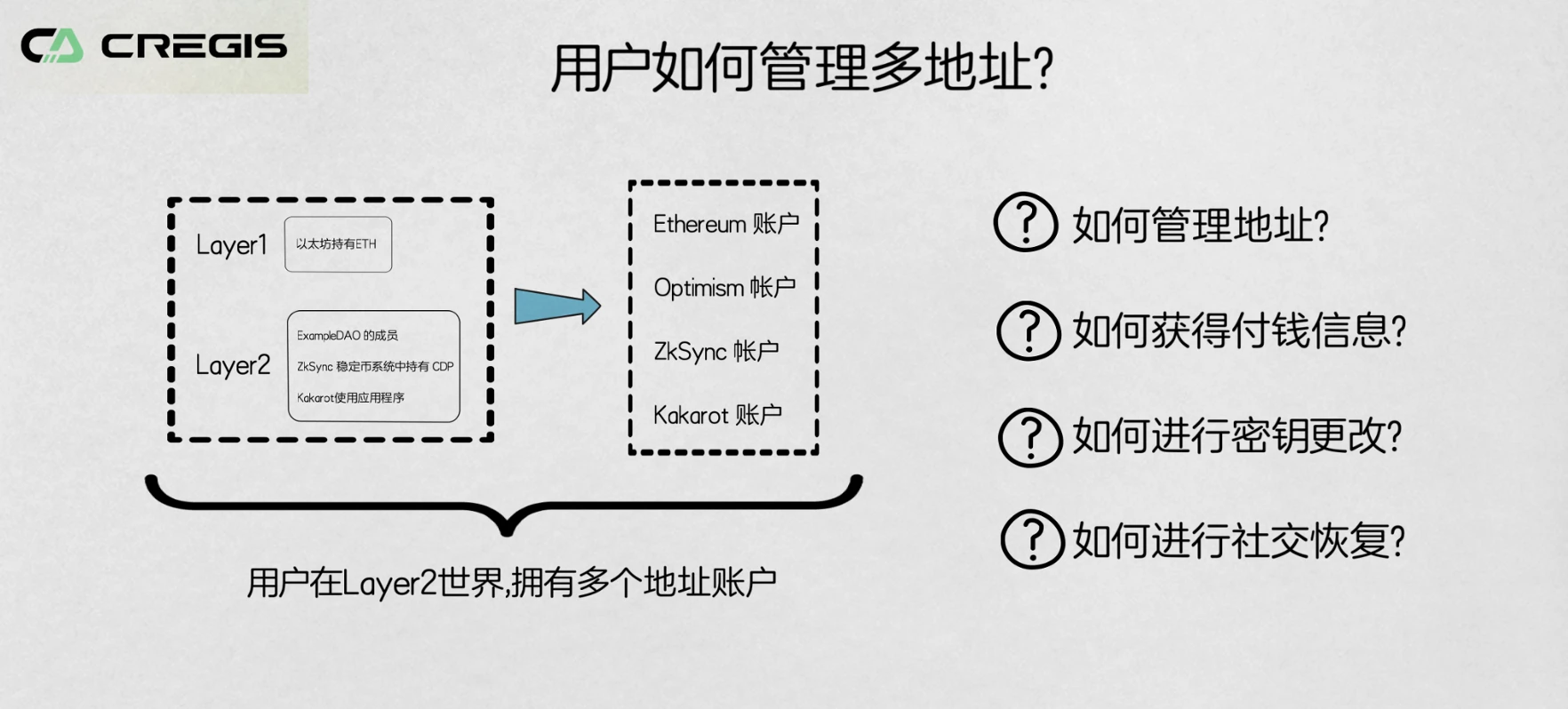
How Users Manage Multiple Wallet Addresses
Web 2.0 compared to Web 3.0, there is still one advantage that remains: users can create different application accounts with a social feature (email, phone number, etc.). Although in the Web 3.0 world, public chain addresses with the same consensus mechanism can be universal (e.g. BSC, ERC-20, TRC-20), with the advent of L2 scaling solutions, users will have multiple completely different L2 addresses. Different Layer 1 and Layer 2 networks may use different programming languages and middleware, which leads to issues in address preservation. Moreover, in the multi-chain bridging environment represented by Polkadot or the multi-chain universal L2 environment mentioned in Cregis' future vision, users may need to manage addresses from several heterogeneous chains, which increases the complexity of address management.
Finally, in terms of privacy protection, if the proposal of stealth addresses is widely used, it will result in users having more addresses to enhance their privacy protection. Therefore, preserving a single address becomes more difficult.
How can users achieve stealth payments? (Especially in a multi-address environment)
If the future L2s in the Ethereum ecosystem develop as expected, even if most native assets are ERC-20 tokens, users may have multiple L2 addresses, making it more complex to choose the correct address to send assets or make payments. Traditionally, users only needed to know the recipient's address to send payments, but now they need to know the recipient's accepted Layer 2 network and the corresponding address, and additional steps are required to ensure that funds are sent to the correct destination.
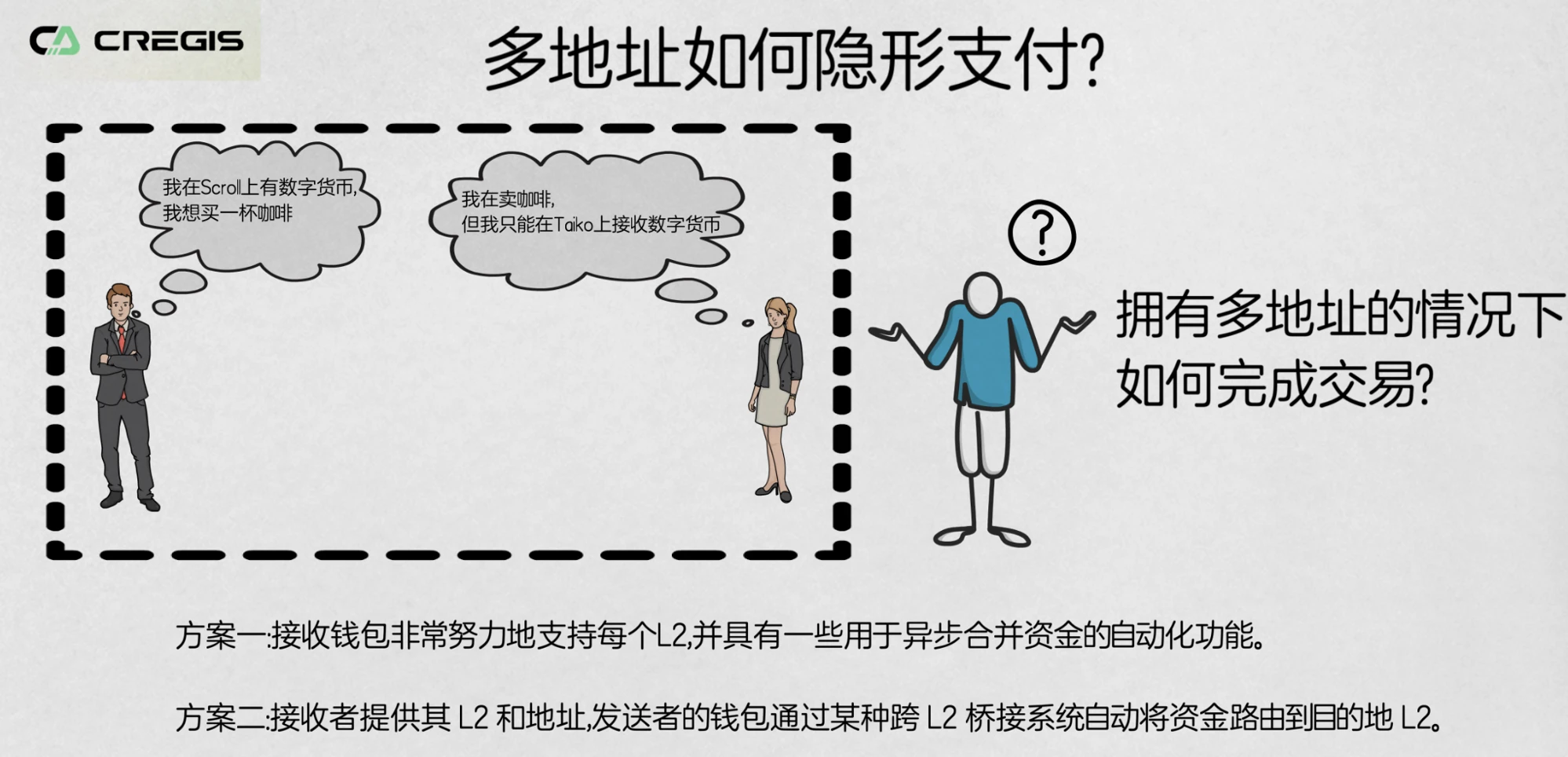
Issue of stealth payments with multiple accounts in L2 environment
Although contract accounts (CA) built using smart contracts can easily solve addressing issues, they cannot directly provide privacy protection.
Vitalik Buterin proposed a privacy protection solution called Stealth Addresses in the early days of Ethereum. Stealth Addresses can help you maintain privacy when conducting digital currency transactions without being traced by others. Here, Cregis will share some steps to address the privacy issue:
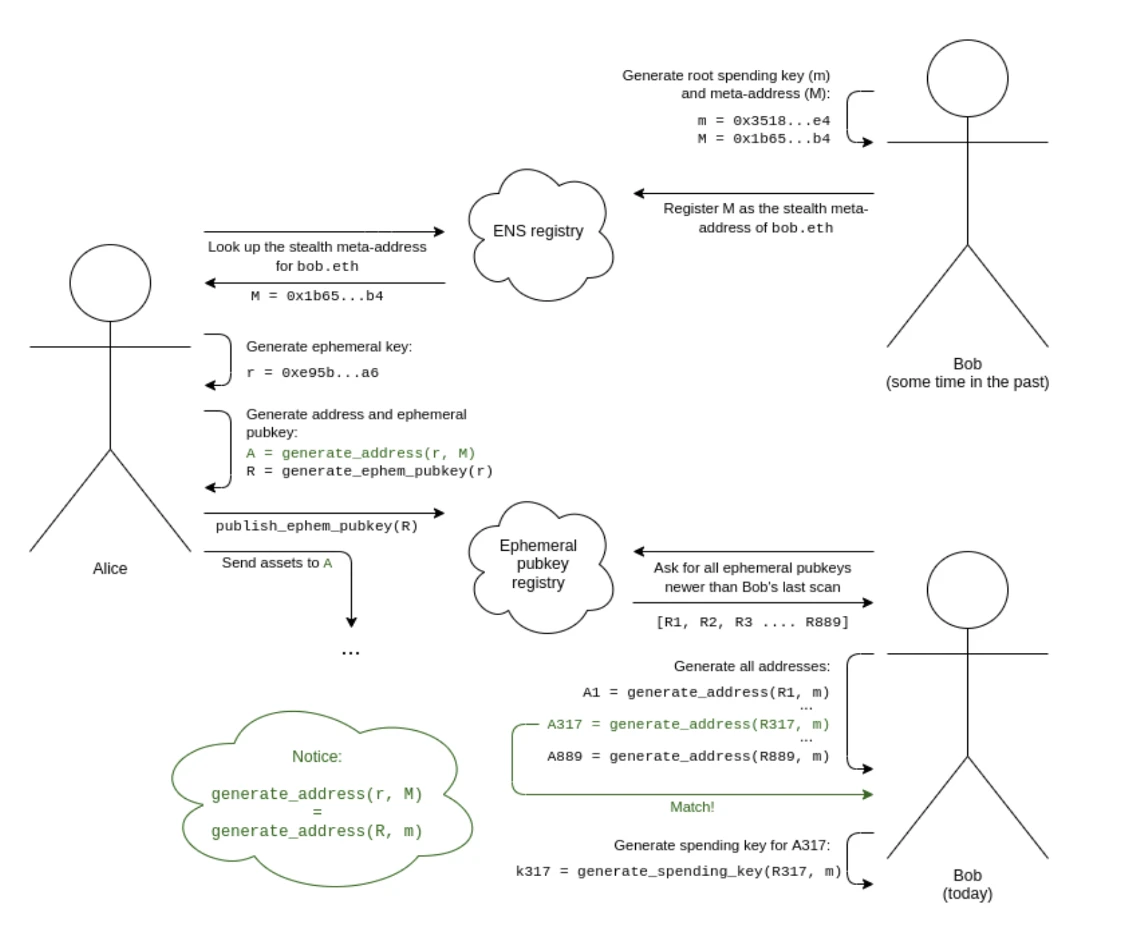
(Complete workflow of Stealth Addresses)
A Stealth Address is an address that can be generated by the payer or payee, but can only be controlled by the payee. This type of address can enhance the privacy of Ethereum in various scenarios. In this mode, Bob (the payee) generates a spending key and uses this key to generate a stealth master address: B, h = hash(x). He passes this master address to Alice (the payer). Alice can perform a computation on this master address to generate a stealth address belonging to Alice to Bob: b-1. She can then send any assets she wants to this address, and Bob will have full control over them.
The generation process of Stealth Addresses involves elliptic curve functions: Bob generates a key m and calculates M = G * m, where G is a publicly known generator point of the elliptic curve. Alice generates a temporary key r and publishes a temporary public key R = G * r. Alice can calculate a shared secret S = M * r, and Bob can also calculate the same shared secret S = m * R.
Bob's invisible address: b-1, after the generation, when trading with Alice, Alice generates a value: c, and publishes an encryption data of c that only Bob can decrypt; during the transaction execution, zero-knowledge proofs are used to verify: the values x provided by Bob and the value c provided by Alice can make k=hash(hash(x), c), once the verification is successful, the transaction is completed. In this process, Bob's original address is not exposed, only an encrypted value x is provided. Zero-knowledge proofs only verify the content of k and do not reveal the association between B and b-1.
How to protect both users' assets and privacy in wallet products?
In traditional on-chain environments, wallets mainly focus on protecting private keys. However, in the world of ZKP (zero-knowledge proofs), wallets need to protect both identity verification credentials and user data. An example is the ZKpass identity system based on ZK-SNARK and MPC, which allows users to generate basic proofs for identity verification without revealing any real information through MPC.
However, the management of encrypted data labels (key shards) itself as a substitute for EOA's private key complicates the custody issue, as users need to weigh between storing the data locally or relying on third parties to hold encrypted copies. At the same time, wallets that support social recovery need to manage asset recovery and encrypted key recovery to ensure a balance between security and availability. Therefore, in the near future, the security strategies for enterprise wallets and personal wallets will take completely different directions. Taking enterprise wallets as an example, due to the need for the most stringent security environment to protect funds, users of enterprise wallets are likely to abandon: 1) contract wallets that may have human vulnerabilities; 2) hybrid custodial MPC wallets with third-party risks, and choose MPC wallets that are deployed in a private manner with the same level of security as hardware wallets. On the other hand, in scenarios other than asset custody, personal users, who always strive for the best user experience, may choose products with partially centralized operations.
In addition, blockchain addresses indeed fail to meet the identity verification needs in the ecosystem. That is why solutions such as ENS (Blockchain Domain Name) and SBT (Soul-Binding Token) are gradually being accepted by the public. However, there are still unresolved issues: the former struggles to solve the problem of homonyms brought by the traditional world, while the latter, although free from the problem of homonyms, has not yet had enough ecosystem applications to fully utilize the DID functionality it carries, and even the current application scenarios can be considered very limited.
The original article has a lot more content, and if you're interested, you can go to "The Three Transitions" by Vitalik Buterin.
4. Summary
I believe you already understand that in this nearly 3-month-long "Ethereum Transition" topic that has caused a stir in the global cryptocurrency community, the wallet is just one important component. V God's ambition is not only to achieve the aspiration of "Ethereum filling the gaps of Bitcoin defects," but also to make Ethereum truly create a world that everyone can enter, closely integrated with the real world while retaining the concept of decentralization.
As both spectators and actual participants in this transformation, Cregis Research has been providing crypto-native enterprise-level payment solutions for Web 3.0 companies and startup teams since 2016, just like Alipay, PayPal, and Shouqianbao provide payment services for traditional businesses and e-commerce organizations. At the same time, Cregis also provides internal fund management and approval flow tools for teams, allowing Web 3.0 companies and startup teams to experience unique comprehensive services.
Next issue preview: Cregis Research will return to cryptography and analyze the differences between the ECDSA elliptic curve function algorithm and the BLS algorithm.
End: About Cregis Research
Cregis is an asset management collaboration platform for the Web 3.0 era, providing enterprise-level wallet+financial SaaS tools. It has been operating safely for 6 years and has created 5.87 million active blockchain addresses for customers. In the past 12 months, it has processed an average of $33 million worth of on-chain assets every day.
Cregis Research is a knowledge sharing platform that aims to provide informative content about blockchain and cryptographic underlying technologies for enthusiasts of Web 3.0. We strive for zero fluff, zero misleading information, and zero commercial bias.










