On May 15, 2024, Sonne Finance was attacked and the project lost more than 20 million US dollars.

SharkTeam conducted a technical analysis of the incident and summarized security precautions at the first opportunity. We hope that subsequent projects can learn from this incident and jointly build a security line of defense for the blockchain industry.
1. Analysis of attack transactions
Attacker: 0xae4a7cde7c99fb98b0d5fa414aa40f0300531f43
Attack contract: 0x02fa2625825917e9b1f8346a465de1bbc150c5b9
Target contract: 0xe3b81318b1b6776f0877c3770afddff97b9f5fe5
Attack transaction: 0x9312ae377d7ebdf3c7c3a86f80514878deb5df51aad38b6191d55db53e42b7f0
The attack process is as follows:
1. Flash loan 35,569,150 VELO and transfer these VELO Tokens to the soVELO contract
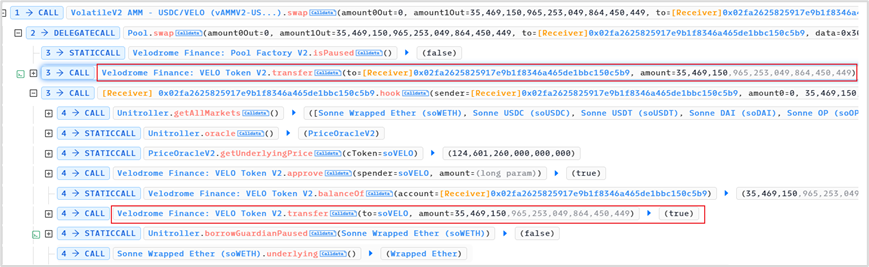
Because it is a direct transfer (donation), no soVELO Token is minted. Therefore, in the soVELO contract, totalCash increases by 35,569,150 VELO, and totalSupply of soVELO remains unchanged.
2. The attacker creates a new contract 0xa16388a6210545b27f669d5189648c1722300b8b and launches an attack on the target contract in the new contract. The attack process is as follows:
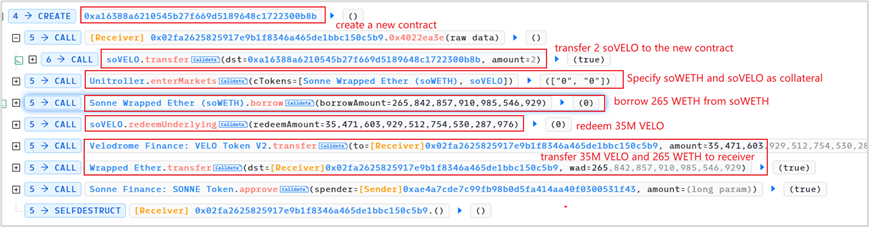
(1) Transfer 2 soVELO to the new contract
(2) Declare soWETH and soVELO as collateral
(3) Borrowed 265, 842, 857, 910, 985, 546, 929 WETH from soWETH
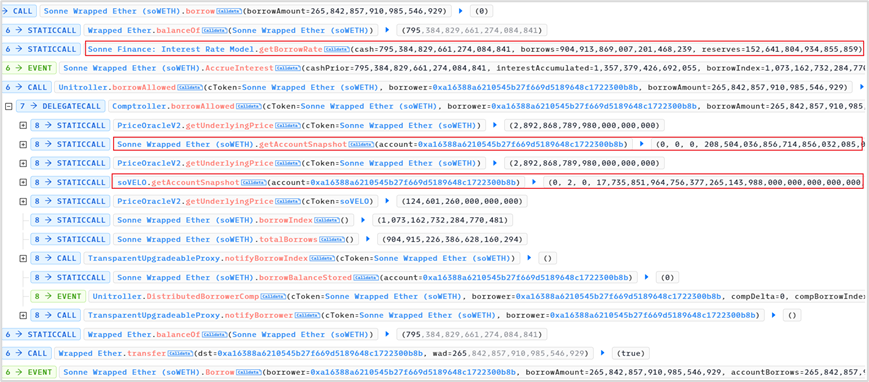
From the execution process of the above borrow function, according to the return value of the getAccountSnapshot function, we find that:
For the soWETH contract, the new contract balance is 0, the loan amount is 0, and the exchange rate is 208, 504, 036, 856, 714, 856, 032, 085, 073
For the soVELO contract, the new contract balance is 2, which means 2 wei of soVELO is pledged, the loan amount is 0, and the exchange rate is 17, 735, 851, 964, 756, 377, 265, 143, 988, 000, 000, 000, 000, 000, 000
exchangeRate is calculated as follows:
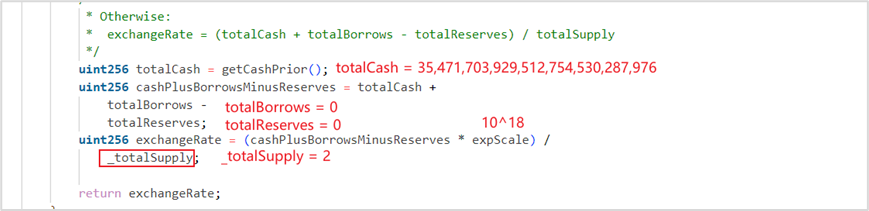
With 1 wei of soVELO as collateral, you can borrow no more than 17, 735, 851, 964, 756, 377, 265, 143, 988 VELO. To borrow 265, 842, 857, 910, 985, 546, 929 WETH, you need to pledge at least 265, 842, 857, 910, 985, 546, 929 soWETH,
soWETHPrice = 2,892,868,789,980,000,000,000,
soVELOPrice = 124,601,260,000,000,000
The amount of WETH that can be borrowed by pledging 1 wei of soVELO is as follows:
1 * exchangeRate * soVELOPrice / soWETHPrice = 763, 916, 258, 364, 900, 996, 923
About 763 WETH. Only 1 wei of soVELO collateral is enough to support this loan.
Borrow 265, 842, 857, 910, 985, 546, 929 WETH (about 265 WETH) and convert it into collateral soVELO. The minimum amount of soVELO required for collateral is:
265, 842, 857, 910, 985, 546, 929 * soWETHPrice / soVELOPrice / exchangeRate = 0.348
That is, 1 wei of soVELO collateral will suffice.
In fact, only 1 wei of the 2 wei soVELO collateral was used for lending.
(4) Redemption of underlying assets, i.e. 35, 471, 603, 929, 512, 754, 530, 287, 976 VELO
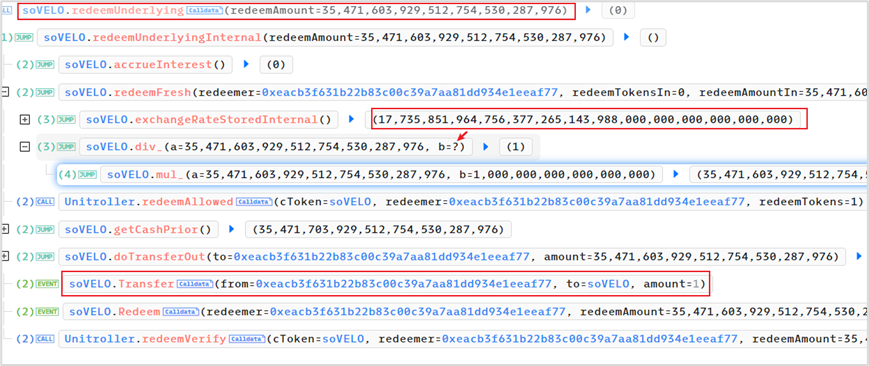
exchangeRate = 17, 735, 851, 964, 756, 377, 265, 143, 988, 000, 000, 000, 000, 000, 000
The amount of collateral soVELO required to redeem 35, 471, 603, 929, 512, 754, 530, 287, 976 VELO is
35, 471, 603, 929, 512, 754, 530, 287, 976 * 1 e 18 / exchangeRate = 1.99999436
When calculating, because the calculation uses truncation instead of rounding, the actual required collateral is 1 wei of soVELO.
The actual collateral is 2 wei of soVELO, of which 1 wei is used to borrow 265 WETH above, and the remaining 1 wei is used to redeem 35M VELO
(5) Transfer the borrowed 265 WETH and redeemed 35M VELO to the attack contract
3. Create a new contract 3 times (4 times in total) and repeat the attack.
4. Finally, repay the flash loan.
2. Vulnerability Analysis
The above attack exploits two vulnerabilities:
(1) Donation attack: Directly transfer (donate) VELO Token to the soVELO contract, changing the exchangeRate, allowing the attacker to borrow approximately 265 WETH with only 1 wei soVELO as collateral.
(2) Calculation accuracy problem: By taking advantage of the accuracy loss in the calculation process and the modified exchangeRate, 35M VELO can be redeemed with only 1 wei soVELO pledged.
3. Safety Recommendations
In response to this attack, we should follow the following precautions during development:
(1) During the design and development process of the project, the integrity and rigor of the logic must be maintained, especially in the areas of deposits, pledges, updating of status variables, and the trade-offs of multiplication and division results during calculations. As many situations as possible should be considered to ensure that the logic is complete and has no loopholes.
(2) Before the project goes online, a smart contract audit is required by a third-party professional auditing company.
About Us
SharkTeams vision is to protect the security of the Web3 world. The team is composed of experienced security professionals and senior researchers from all over the world, who are proficient in the underlying theories of blockchain and smart contracts. It provides services including risk identification and blocking, smart contract auditing, KYT/AML, on-chain analysis, and has created an on-chain intelligent risk identification and blocking platform ChainAegis, which can effectively combat the advanced persistent threats (APT) in the Web3 world. It has established long-term cooperative relationships with key players in various fields of the Web3 ecosystem, such as Polkadot, Moonbeam, polygon, Sui, OKX, imToken, Collab.Land, TinTinLand, etc.
Official website: https://www.sharkteam.org
Twitter: https://twitter.com/sharkteamorg
Telegram: https://t.me/sharkteamorg
Discord: https://discord.gg/jGH9xXCjDZ










