On June 10, 2024, UwU Lend was attacked and the project lost approximately US$19.3 million.

SharkTeam conducted a technical analysis of the incident and summarized security precautions at the first opportunity. We hope that subsequent projects can learn from this incident and jointly build a security line of defense for the blockchain industry.
1. Analysis of attack transactions
Attacker: 0x841dDf093f5188989fA1524e7B893de64B421f47
The attacker initiated a total of 3 attack transactions:
Attack Transaction 1:
0x242a0fb4fde9de0dc2fd42e8db743cbc197ffa2bf6a036ba0bba303df296408b
Attack Transaction 2:
0xb3f067618ce54bc26a960b660cfc28f9ea0315e2e9a1a855ede1508eb4017376
Attack Transaction 3:
0xca1bbf3b320662c89232006f1ec6624b56242850f07e0f1dadbe4f69ba0d6ac3
Take attack transaction 1 as an example for analysis:
Attack contract: 0x21c58d8f816578b1193aef4683e8c64405a4312e
Target contract: UwU Lend Treasury contract, including:
uSUSDE: 0xf1293141fc6ab23b2a0143acc196e3429e0b67a6
uDAI: 0xb95bd0793bcc5524af358ffaae3e38c3903c7626
uUSDT: 0x24959f75d7bda1884f1ec9861f644821ce233c7d
The attack process is as follows:
1. Flash loan multiple tokens from different platforms, including WETH, WBTC, sUSDe, USDe, DAI, FRAX, USDC, GHO
The token receiving address is 0x4fea76b66db8b548842349dc01c85278da3925da

The tokens and quantities of flash loans are as follows:
Flash loan 159,053.16 WETH and 14,800 WBTC from Aave V3
Flash loan 40,000 WETH from Aave V2
Flash loan 91,075.70 WETH and 4,979.79 WBTC from Spark
Flash loan 301,738,880.01 sUSDe, 236,934,023.17 USDe and 100,786,052.15 DAI from Morpho
Flash loan 60,000,000 FRAX and 15,000,000 USDC from Uniswap V3: FRAX-USDC
Flash loan 4,627,557.47 GHO and 38,413.34 WETH from Balancer
Flash loan 500,000,000 DAI from Maker
A total of approximately 328,542.2 WETH, 19779.79 WBTC, 600786052.15 DAI, 301,738,880.01 sUSDe, 236,934,023.17 USDe, 4,627,557.47 GHO, 60,000,000 FRAX, 15,000,000 USDC
2. Transfer the flash loan token to the contract 0xf19d66e82ffe8e203b30df9e81359f8a201517ad (abbreviated as 0xf19d) in preparation for launching the attack.

3. Control the price of sUSDe (lower the price) by exchanging tokens

(1) USDecrvUSD.exchange
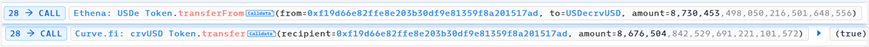
Convert 8,676,504.84 USDe to 8,730,453.49 crvUSD. The amount of USDe in USDecrvUSD increases, the price decreases, and the amount of crvUSD decreases, the price increases.
(2) USDeDAI.exchange

Convert 46,452,158.05 USDe to 14,389,460.59 DAI. The amount of USDe in USDeDAI increases, the price decreases, and the amount of DAI decreases, the price increases.
(3) FRAXUSDe.exchange
Convert 14,477,791.69 USDe to 46,309,490.86 FRAX. The amount of USDe in USDDeDAI increases, the price decreases, and the amount of FRAX decreases, the price increases.
(4) GHOUSDe.exchange
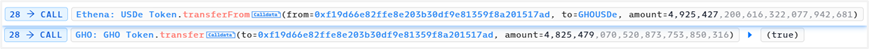
Convert 4,925,427.20 USDe to 4,825,479.07 GHO. The amount of USDe in USDDeDAI increases, the price decreases, and the amount of GHO decreases, the price increases.
(5) USDeUSDC.exchange
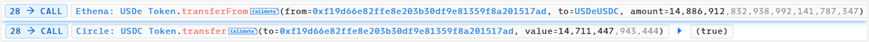
Convert 14,886,912.83 USDe to 14,711,447.94 USDC. The amount of USDe in USDDeDAI increases, the price decreases, and the amount of USDC decreases, the price increases.
After the above exchange, the USDe prices in the five funding pools decreased, which eventually led to a sharp drop in the sUSDe price.
4. Continue to create lending positions, that is, deposit other assets (WETH, WBTC and DAI) into the LendingPool contract, and then borrow sUSDe. Because the price of sUSDe has plummeted, the amount of sUSDe borrowed is much more than before the price plummeted.

5. Similar to step 3, the reverse operation pushes up the price of sUSDe.
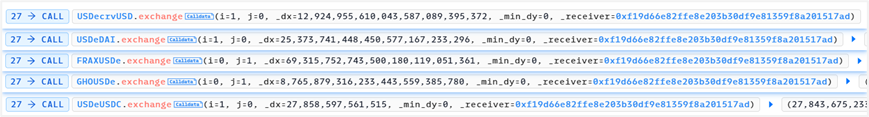
As sUSDe was pulled up, the loan position value in step 4 exceeded the collateral value and reached the liquidation standard.
6. Liquidate loan positions in batches and receive liquidation rewards uWETH

7. Repay the loan and withdraw the underlying assets WETH, WBTC, DAI and sUSDe.
 8. Deposit sUSDe into LendingPool again. At this time, the price of sUSDe is raised, so more other assets can be borrowed, including DAI and USDT.
8. Deposit sUSDe into LendingPool again. At this time, the price of sUSDe is raised, so more other assets can be borrowed, including DAI and USDT.
9. Exchange tokens and repay flash loans. Final profit: 1,946.89 ETH

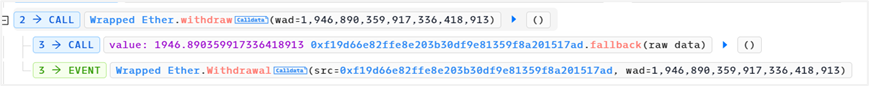
2. Vulnerability Analysis
Through the above analysis, it is found that there are a large number of flash loans and multiple manipulations of the sUSDe price during the entire attack process. When sUSDe is pledged, the amount of borrowed assets will be affected; when sUSDe is borrowed, the borrowing rate will be affected, and then the liquidation coefficient (health factor) will be affected.
The attacker took advantage of this and used flash loans to drive down the price of sUSDe, mortgaged other assets, borrowed a large amount of sUSDe, and then raised the price of sUSDe, liquidated the mortgaged assets for profit, and mortgaged the remaining sUSDe to borrow other assets. Finally, he repaid the flash loan and the attack was completed.
From step 3 above, we found that the attacker manipulated the price of sUSDe by controlling the price of USDe in Curve Finances USDe/rvUSD, USDe/AI, FRAX/SDe, GHO/SDe and USDe/SDC trading pools. The price reading function is as follows: 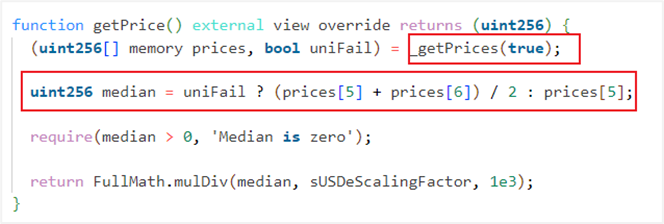

Among them, the sUSDe price is calculated from 11 prices, the first 10 of which are read from CurveFinance, and the last one is provided by Uniswap V3.
The prices read from CurveFinance are provided by five trading pools: USDe/rvUSD, USDe/AI, FRAX/SDe, GHO/SDe and USD/SDC, which are also the five trading pools manipulated by the attacker in the attack transaction.
The returned price is calculated by the price read by uwuOracle, price_oracle(0) and get_p(0) in the CurveFinance trading pool contract.
(1) The price is provided by Chainlink and cannot be manipulated;

(2) Trading pool parameters
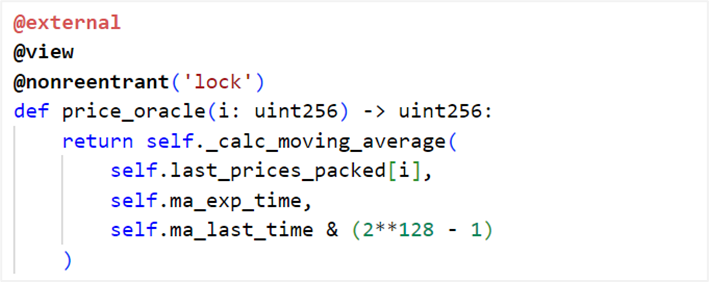

The attacker manipulates the return value of get_p(0) by manipulating the number of tokens in the transaction pool, thereby manipulating the price.
3. Safety Recommendations
In response to this attack, the following precautions should be followed during development:
(1) To address the price manipulation vulnerability, an off-chain price oracle can be used to prevent price manipulation.
(2) Before the project goes online, a third-party professional auditing company needs to conduct a smart contract audit.
About Us
SharkTeams vision is to protect the security of the Web3 world. The team is composed of experienced security professionals and senior researchers from all over the world, who are proficient in the underlying theories of blockchain and smart contracts. It provides services including risk identification and blocking, smart contract auditing, KYT/AML, on-chain analysis, and has created an on-chain intelligent risk identification and blocking platform ChainAegis, which can effectively combat the advanced persistent threats (APT) in the Web3 world. It has established long-term cooperative relationships with key players in various fields of the Web3 ecosystem, such as Polkadot, Moonbeam, polygon, Sui, OKX, imToken, Collab.Land, TinTinLand, etc.
Official website: https://www.sharkteam.org
Twitter: https://twitter.com/sharkteamorg
Telegram: https://t.me/sharkteamorg
Discord: https://discord.gg/jGH9xXCjDZ










