Hash of this article (SHA 1): ca13a25f6b3e6d952ef55932b136b75b074015af
No.: Lianyuan Security Knowledge No.014
Analysis of the security aspects and market dynamics of ETF launches
With the launch of the Ethereum spot ETF in the United States on July 23, the market is paying close attention to its potential impact. Bitwise’s chief investment officer predicts that the ETF will push the price of Ethereum to a record high of more than $5,000. , the evolution and security of Ethereum have also become the focus. This article combines ETF and the second-layer expansion plan to analyze their impact and potential on the Ethereum ecosystem.
Security and market impact of Ethereum ETF
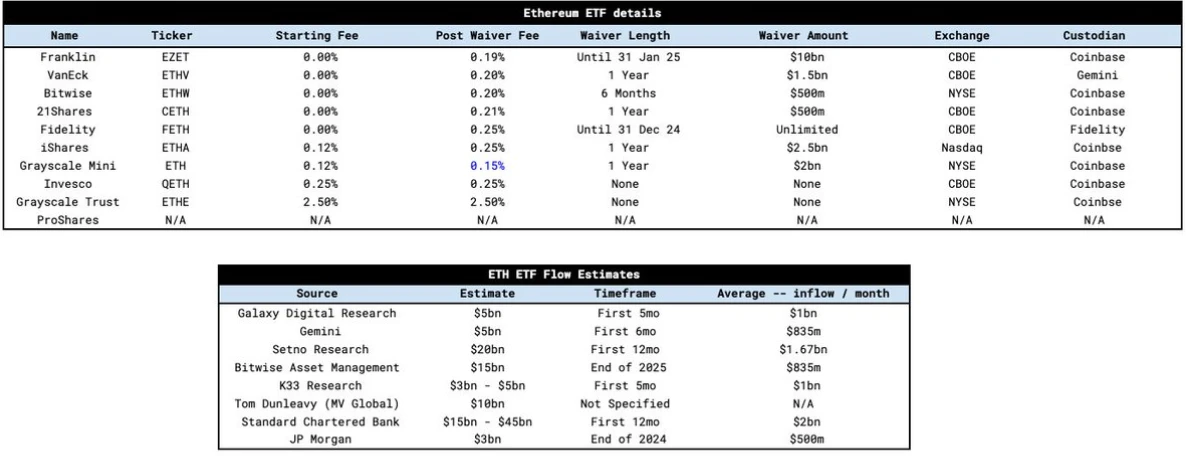
The launch of the Ethereum ETF brings new sources of demand to the market, but also brings security challenges and opportunities. At this stage, Ethereums low inflation rate, staking mechanism and locked supply will amplify the price increase brought by ETF inflows. Effect.
The security of Ethereum staking
Ethereums staking mechanism is different from Bitcoins, and does not force stakers to sell the ETH they have obtained. The staking mechanism not only reduces short-term selling pressure, but also enhances the security and stability of the network.
Locking in the security of supply
Currently, 28% of ETH has been staked, 13% is locked in DeFi smart contracts, and about 40% of ETH has withdrawn from market circulation. This locked supply mechanism provides additional security for Ethereum.
Layer 2 Extensions: Solving the Security Challenges of Bridges
In cross-chain asset transfers, differences in blockchain architecture and consensus mechanisms lead to complex and expensive verification processes, limiting asset mobility. Existing third-party bridges face trust and security challenges, while centralized bridges need to maintain Liquidity, cost transfer to users. One-click chain launch is like solving the triangle problem, which is a compromise asset bridging solution. The following are several second-layer expansion solutions and their security analysis:
ZKsync 3.0: Elastic Chain
Elastic Chain is an infinitely scalable network composed of ZK Chains (rollups, validiums, and volitions), which is secured by mathematical verification methods. The design of ZK Router, ZK Gateway, and ZK Chains ensures efficient and secure interaction between different chains. Operability.
Polygon 2.0: AggLayer
AggLayer achieves atomic cross-chain interoperability between different Rollups through a shared sorter, a unified bridge, and a pessimistic proof mechanism. The unified bridge ensures seamless communication between different chains through standardized interoperability protocols and cross-chain communication protocols. and data transmission, improving security.
Optimism: Superchain Explainer
Optimisms Superchain establishes a unified network standard through OP Stack to achieve coordination and communication between chains. Its five-layer structure consisting of data availability layer, sorting layer, derivative layer, execution layer and settlement layer ensures the security and reliability.
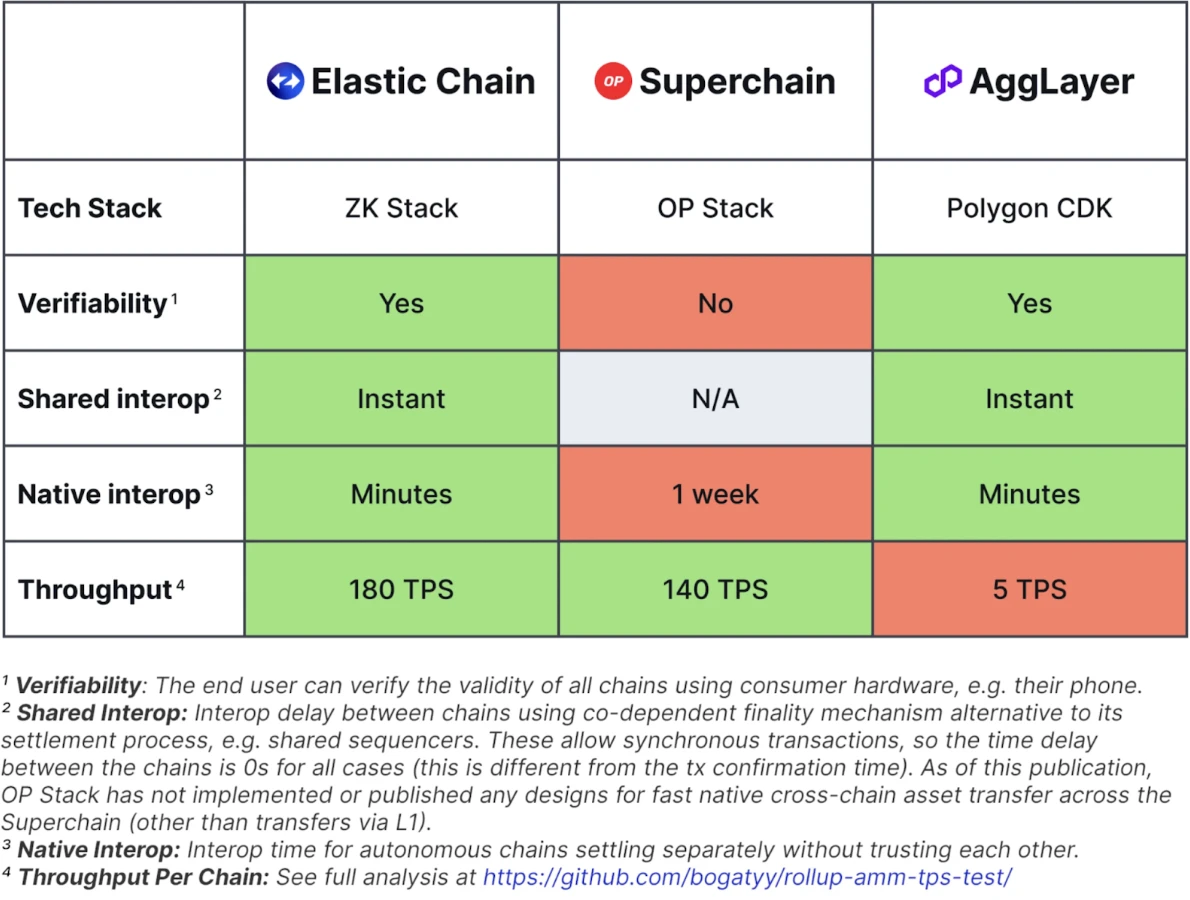
Connecting islands between chains: the security issues of bridges
The main problem with cross-chain asset transfers is that different blockchains have different architectures and consensus mechanisms, lacking a unified standard, leading to a complex and expensive verification process. This limitation has led to a surge in authentication networks that use multi-signature committees to prove the state of the other chain. There is currently no universal decentralized standard or protocol that enables interoperability between all blockchains, which limits the free flow of assets between different blockchains.
To facilitate cross-chain asset transfers, a large number of third-party bridges have emerged, but these bridges face huge network security challenges in operation. Centralized bridges need to maintain sufficient liquidity on each integrated chain, and the cost is transferred. To users. Currently, there are problems that cannot meet the requirements of native decentralized asset bridging and it is difficult to trust third-party bridges.
Security and future development of one-click chain issuance
The evolution of Ethereum and the launch of one-click chain launch have brought more security and scalability solutions to the blockchain ecosystem. ZKsync 3.0, Polygon 2.0 and Optimisms different expansion solutions have achieved inter-chain interoperability. and improving system security.
Summarize
In the future, with the launch of ETFs and the continuous optimization of the second-layer expansion plan, the price and security of Ethereum will continue to improve. The innovation and development of DeFi protocols and other applications on Rollup will also inject new vitality into the Ethereum ecosystem. Vitality and security. Through continuous optimization and upgrading, Ethereum is expected to achieve wider applications and higher market value while ensuring security.
Lianyuan Technology is a company focusing on blockchain security. Our core work includes blockchain security research, on-chain data analysis, and asset and contract vulnerability rescue. We have successfully recovered many stolen digital assets for individuals and institutions. At the same time, we are committed to providing industry organizations with project security analysis reports, on-chain traceability and technical consulting/support services.
Thank you for your reading. We will continue to focus on and share blockchain security content.










