Moderator: So... how did you get into the Crypto industry?
Andre Cronje: My gay friend went on honeymoon.
Im alone in the office, You left Cape Town and no one talks to me anymore》。
I am bored.
Im boring.
This is where all stories begin.
ACs Early Years
Great people are usually great early on.
Many people think that AC is a typical Silicon Valley engineer, but he is not.
AC is a white South African, and Elon Musk is an out-and-out fellow. From Cape Town, the port city where AC lives, to Pretoria, where Musk was born, it is about 1,500 kilometers, roughly equivalent to Shanghai to Beijing.
The things these two people do are also very similar, establishing multiple businesses continuously and at the same time,and the rest is history.

AC studied law as Elon studied physics.
In the field of pan-IT, there are usually two types of people who really achieve great things—OI party who started to learn programming in junior high school in their teens, such as Wang Xiaochuan; or half-way monks, interest-driven programmers, such as Wang Xing.
The former kind of people write more than ten thousand lines of codes than their peers when they are working as workers; the latter kind of people are often motivated by interest, are more diligent than the students of the majors, and have experience in other fields.
Apparently, both teenage geniuses, both born to do it。
AC and Elon clearly fall into the latter category as well.
After finishing his law degree, AC always drove his gay friends to class, and went to school to flirt with pretty girls.
Jiyou learned CS, but unfortunately he is not good at learning skills, he can only cheat and divide samples, and miracles can be done violently, he can only memorize templates in graph theory, and he can only know GCD in number theory.
AC has a look at the textbooks of friends, so easy, isnt it CRUD addition, deletion, modification and query, it takes three years to learn.
It took 6 months for AC to graduate from the 3-year course.
When I graduated, a lecturer in the school just left, and the principal asked AC if he would give it a try.
As a result, a law student in AC completed the CS course in half a year, and taught the course for two years by the way.
AC = Accepted.
The ordinary life obviously couldnt restrain ACs tossing heart. AC quit his school job and went to work for Vodacom, Africas largest operator, for two years.
This year, Mr. Qiao released the iPhone, and AC went to play with mobile terminal development again, making some anti-virus software at the bottom of the mobile terminal.
Then, AC tried FinTech, finance, big data, distributed computing, unmanned driving, high-frequency consensus...
In short, AC has played everything from machine forgetting to artificial mental retardation to data filling and mode confusion.
Unlike ordinary geeks, AC also has a deep research on finance.
And they all did a good job.
Similar to Wang Yin in the early years, a simple reply from a young genius can awaken the thinking of ordinary people and change the lives of a small group of ordinary people.
Why Hong Kong, many things have deep dark lines.
Born to do it, again.
access to cryptocurrency
The southern hemisphere summer in 2017 was slightly cooler than the northern hemisphere winter.
AC is walking the streets of Cape Town, kicking pebbles and not knowing where.
Usually at this time, you should discuss with your good friends the ten ways of writing the dynamic cactus or the backtest effect of an arbitrage model yesterday, and D to each other.
Its a pity that my good friend just got married and went on honeymoon.
There are only empty offices, and ACs empty heart.
At that time, BTC was about to hit $20,000, and my stud brother who couldnt help but wait for three years to get out of the trap.
This of course attracted AC, who was very excited when he discovered cryptocurrencies such as Bitcoin and Ethereum.
Because the crypto world has everything he has learned in the past, just as the global optimal solution does not necessarily consist of local optimal solutions.
Nothing is done for nothing.
The Crypto world requires both programming knowledge and financial knowledge. As for the original law?
Well, have you ever heard of Code is Law?
Yes, Chosen One, born to do it.
So what will the Chosen One do?
Certainly not at the high point of the bull market I cant help it, AC started code reviewing the blockchain to teach himself and better understand the technology. After a period of commentary in the media, one of his posts went viral. This is how his popularity started to rise. From there, he caught the attention of the CEO of Crypto Briefing, and the CEO classmate decided to make AC the chief Code Reviewer of Crypto Briefing.
PS: Crypto Briefing is currently working on an oracle product called Umbrella, which may be publicly raised in January.
We appreciate an AC code review report on the recently launched NuCypher project on Coinbase:
NuCypher Code Review by Andre Cronje

NuCypher is a project that introduces a key management system (KMS) to the blockchain, making decentralized systems and applications more secure. For the NuCypher code review, we will take the technical way of working as an example.
Alice has sensitive data that she wishes to be able to proxy access to;
Alice encrypts the data with her own public key and stores it in the cloud or in decentralized storage;
Alice grants access to Bob. The data is re-keyed to Bobs storage key;
Bob downloads the data and decrypts it with his private key;
The data is re-keyed to Bobs storage key. The original signature cannot be done using only the private key, otherwise the key cannot be re-entered. So lets quickly get into the exposition of private and public keys.
Lets say I get a NuCypher code review message and encrypt it with a private key. i will get
0xca92b9be89c0506044cacd947f1630f271aa8c2cb97916b65487f3944245b67b5f2166ff995c605a5ae1c8ac9bd77760f1e90837545fd5be9c87c4f9bf3c71f11b
Someone with knowledge of the above cannot reverse engineer it. So, what is the value of this? Given 3 inputs (public key, hash, and original message), it can be proven that the above was indeed signed by the private key of the corresponding public key. You can confirm this by verifying the signature.
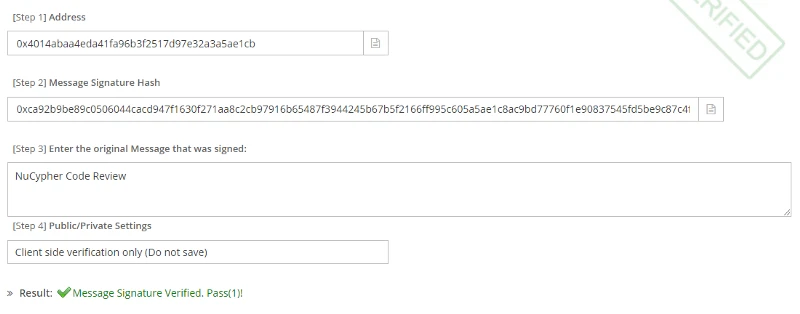
So now you know that I have the private key to the corresponding public key that was provided. This is how I can prove ownership.
The point is, with only the original hash and not the original data, there is no way you can rekey this information. This is what allows multiple key ownership into other key systems. So my assumption is that NuCypher must have similar measures, so lets get started.
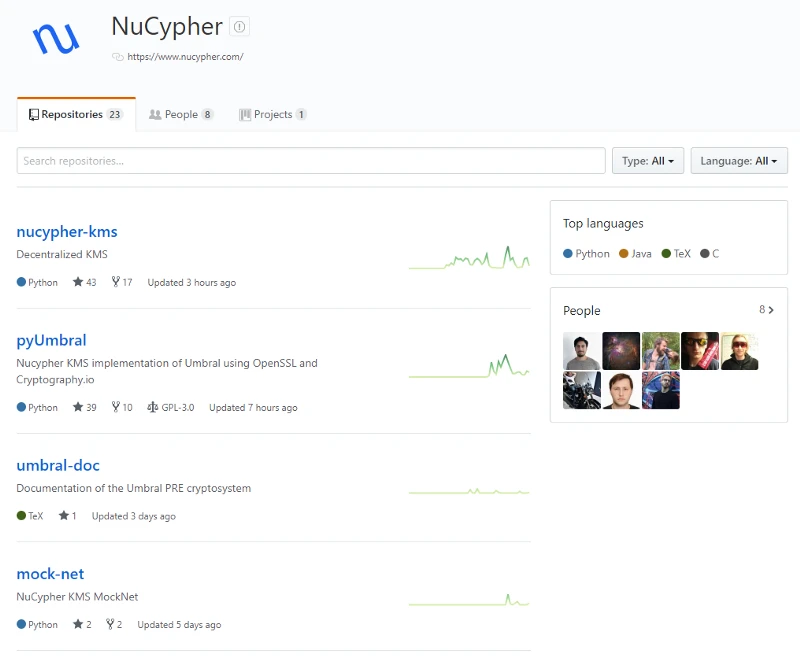
nucypher-kms and mock-net are the two Im interested in, so lets go over nucypher-kms first.
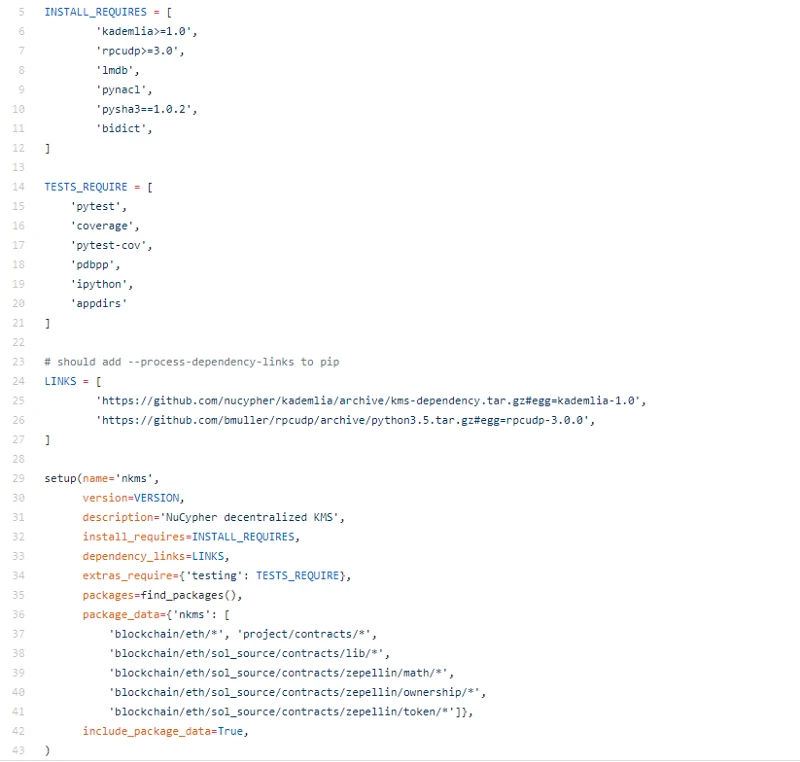
We have standard players, kademlia, rpcudp, lmdb (this is new) and ethereum VM contracts in the tech stack game.
At this point I realized that Umbral is actually core so we changed to pyUmbral
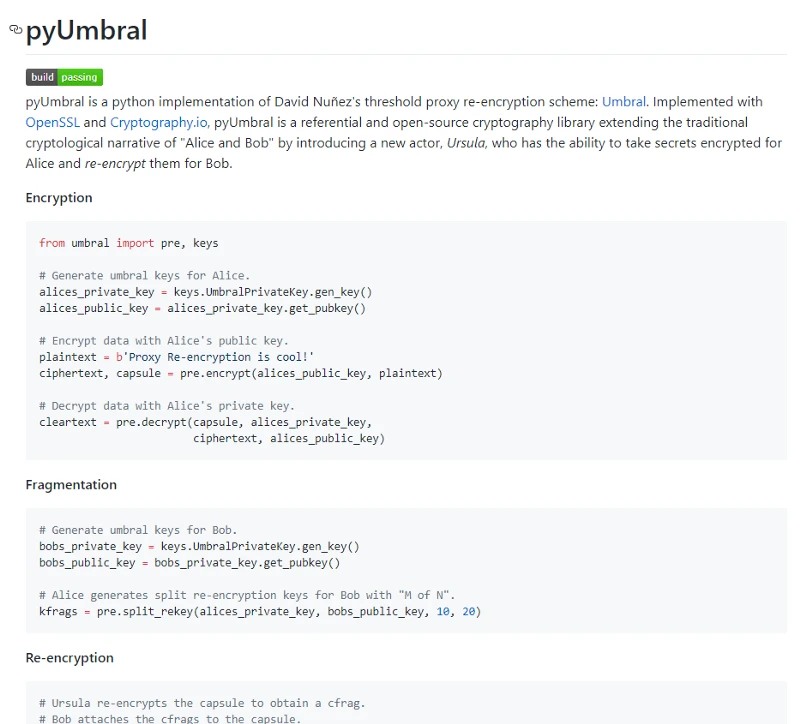
Cool, so Alice can generate a rekey for Bob by creating a new shared secret using Alices private key and Bobs public key. Bob can then re-encrypt based on this.
Then the process is as follows:
Alice signs the data and stores the data publicly. Bob wants access, and uses his public key to request access from Alice. Alice creates a new pair (not technically, but keeping it that way for simplicity), and Bob can then decrypt the data with his private key.
Data in transit is never publicly disclosed unless disclosed by a party from its end point. I like it and move on.
return nucypher-kms:
Good structure, good annotations, good encapsulation. So far, I like its layout and content.
This is great, they kept the Alice and Bob theme in all the code, added user stories before each function, and kept function calls specific, like from_alice above, and used bob as a parameter to in between Create a strategy. This is code written in consideration of other readers, which I havent seen much.
The REST server has some basic endpoints, nothing fancy.
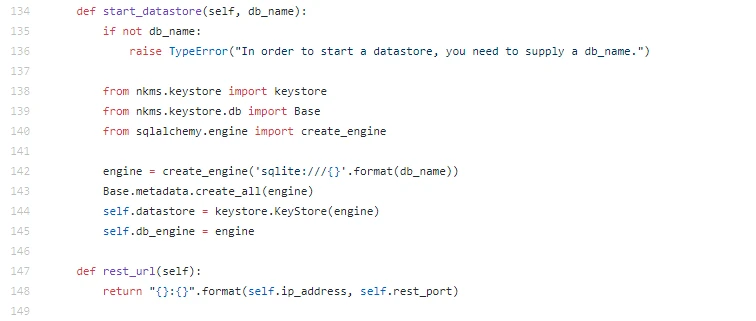
Use sqlites local storage. The REST functionality is stable, reliable, and constantly evolving.
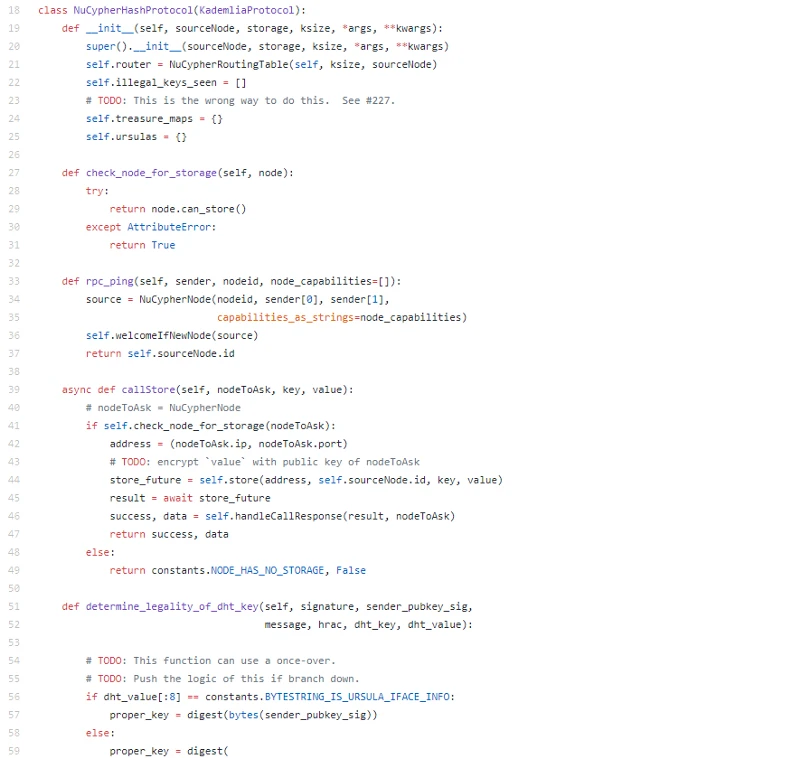
Another nice implementation is a p2p node swarm. Nodes can join and be required to store encrypted data.
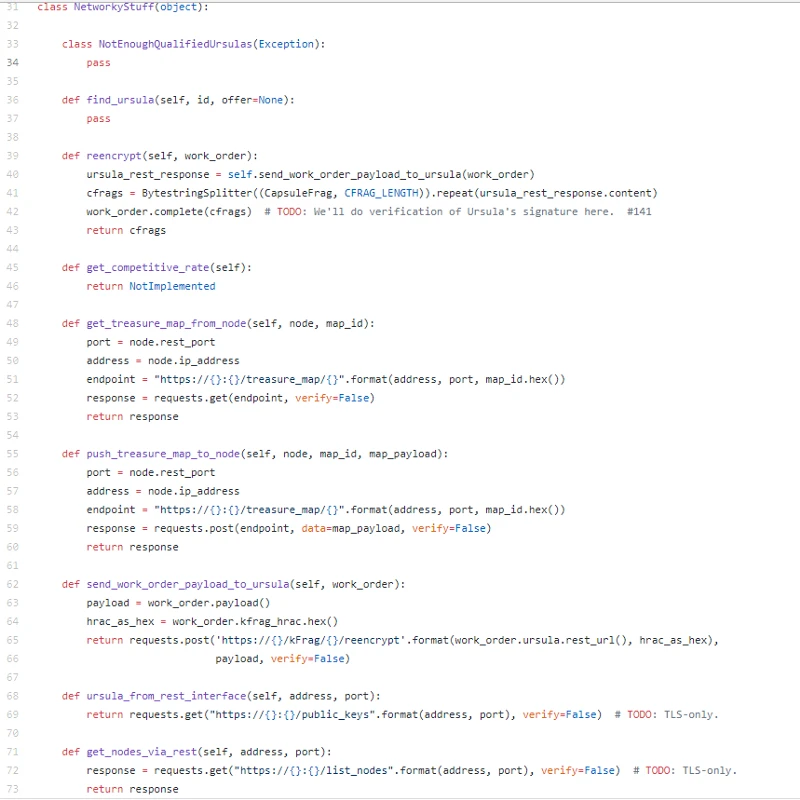
Its nicely implemented directly on Node.
So far, we have the Umbra implementation to allow rejoining, have implemented the basic policy to allow contracts between two participants, and provide the basis for requesting storage between nodes.
Lets look at the blockchain side of things:
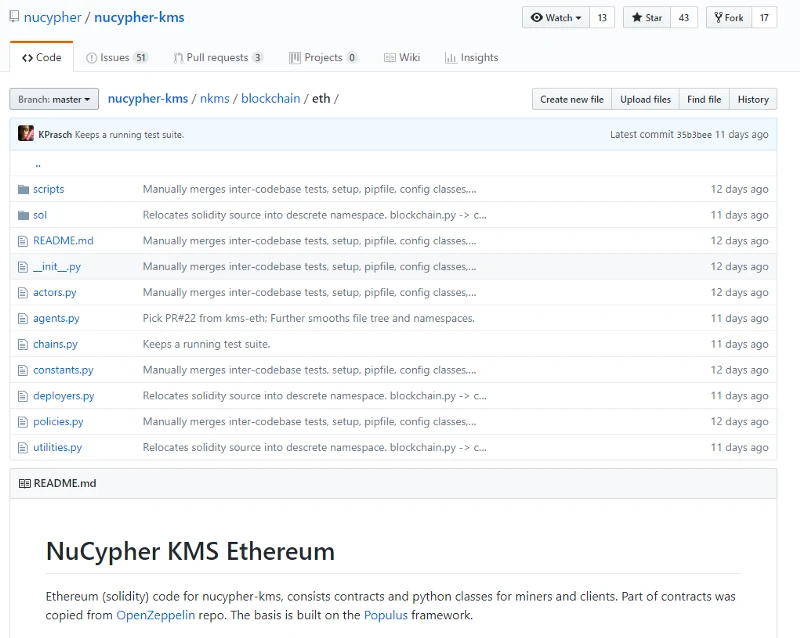
Time to add some smart contract goodies. Escrow contract.
First you need to understand PolicyManager, take a look at it.
Still not sure what the PolicyManager does, its both a storage policy and an equity policy, both. I will refer to the white paper.
MinerEscrow, no big price cuts for misbehavior. This is a vested interest, not a bet, because there is no risk. For miners, this is still a good exercise contract.
So start a node, provide re-encryption cycles, stake the minimum token stock required for a node, and be rewarded for activity. The token economy seems a bit forced, but these days thats the norm for rewarding people like this, so here goes.
NuCypher code review conclusion:
Great code, strong architecture, all core use cases are proven. This is a solid implementation with high quality skills. It uses the standard, incentivize people to provision CPU/storage/network by paying fees in tokens philosophy, staking (vesting) and token economics seem to be pushed onto the solution rather than a natural part of it , but I dont have any fundamental issues with this approach. Decentralization is another matter after all.
Not a blockchain, but a novel idea, is there really a need for a decentralized Dropbox, an encrypted Slack, or a patient-controlled electronic health record? Dont know, but this is good code.
(End of the first section, to be continued, inspired by FTX Podcast)










