Today, we can see that many public chains are using multi-chain structures, such as cross-chain projects Polkadot, COSMOS, such as Ethereum’s sharding (old roadmap) structure. From a technical logic point of view, multi-chain structures exist in many ecology, as long as the process of communication between different layers and different chains (or nodes) is involved, some designs on the multi-chain structure are required.Mutual protection of PoW chains
Plan Bai has seen some security protection solutions in the very early days. At that time, the industry focus was not on the PoS network (Ethereum), and the cryptocurrency industry still highly respected the security brought by PoW. .In the past few years, there have been many attacks on the PoW network. The reason for this is related to the computing power of the PoW network. The computing power is also one of the determining factors in the consensus process of the PoW network, which is what we call a 51% computing power attack. , when the computing power exceeds 51%, an attack chain can be generated to replace the original longest chain.Here, attackers use rented or self-owned computing power to attack the network, which is very common for many networks whose total computing power is not high and the computing power is not dispersed enough. For example, the ETC network with the problem of client change, and the BTG network with insufficient computing power.Therefore, we can think about how a PoW network with a very low computing power can improve the security of its own network without changing the network structure, consensus algorithm, or causing forks?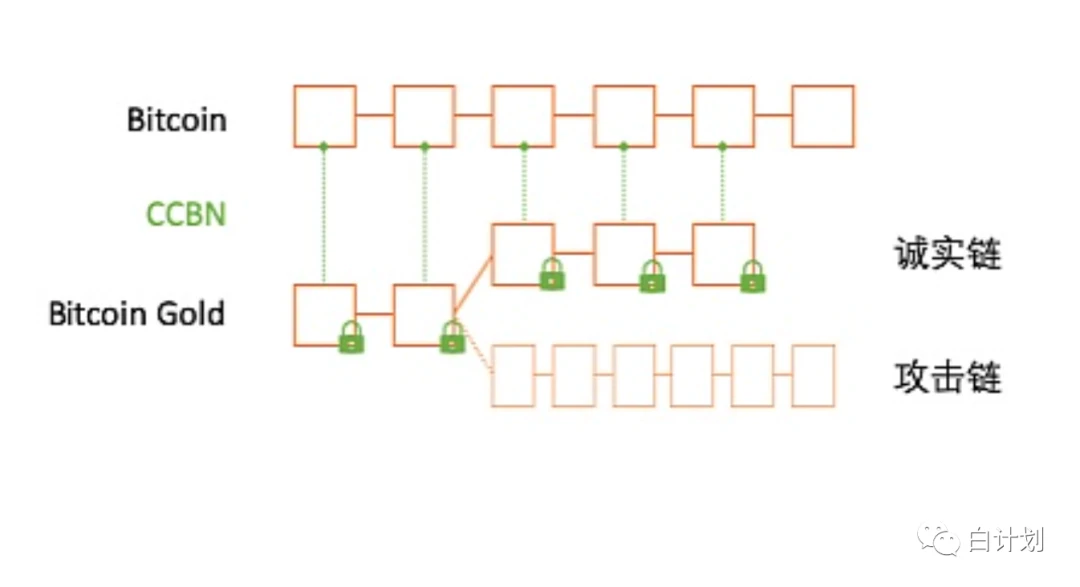
The picture shows a structural design case of using the BTC network to protect the BTG network
The security of the low computing power blockchain is not high because double spending of ledgers is easy to occur, so if the ledger of the low computing power blockchain is packaged into the area of the high computing power blockchain through cryptography and communication protocols In the block, there is a fair proof just outside its own blockchain, which can reversely prove whether the data in the original blockchain is correct.This is the idea that the high computing power blockchain shares its security with the low computing power blockchain, because the blockchain itself is a distributed proof system, as long as it meets the idea that it can be proved safely, it can become a proof. Security, many networks that lack security or require higher security can obtain security through this proof (such as some newly created networks).Those multi-chain structures with protection relationship
Why is there a multi-chain structure? The fundamental reason is still to rely on the multi-chain structure to solve the problems that a blockchain cannot solve, that is, expansion, data sharing, security, etc.In the multi-chain design, security is still the core, because the biggest highlight of the blockchain is to solve the double-spend problem.Many of the cases we have seen are designed as multi-chains, all relying on security.For example, the design we see the most: anchor currency, the anchor currency is a good design for liquid assets on a network with higher performance, and the anchor currency is the result of a single asset being protected by another chain.This design may not be obvious because, for example, Ethereum does not use the security of the Bitcoin network, but Bitcoin uses the Ethereum network to increase the liquidity of assets.
The picture shows the multi-chain structure of Polkadot
For this structure, we can use Polkadots relay chain, COSMOS Zone chain, the bridge and HUB of the cross-chain solution, and also include the design of the Ethereum beacon chain and sharding, and the side chain of plasma.Their common features are all the same: the lower-level chain relies on the upper-level chain to confirm the final account book, and the lower-level chain needs the upper-level chain to prove that the data on the chain is correct.Security protection structure of cross-chain relay
The COSMOS fire in 2019 and the Polkadot fire in 2020 are both cross-chain projects, and the ecology of both projects is a multi-chain structure. In the multi-chain structure, the main network of the two projects ultimately provides security, COSMOS is COSMOS HUB, and Polkadot is the Polkadot main network.For the chains connected in the Polkadot ecology and COSMOS ecology, they all need to rely on the security of the main network, and the embodiment of this security is reflected in the relay part of the chain and the main network. In COSMOS it is Zone, while Polkadot is the relay chain.The role of the Polkadot relay chain and Zone is the same. They are both a transit and security proof part for chain-to-chain communication.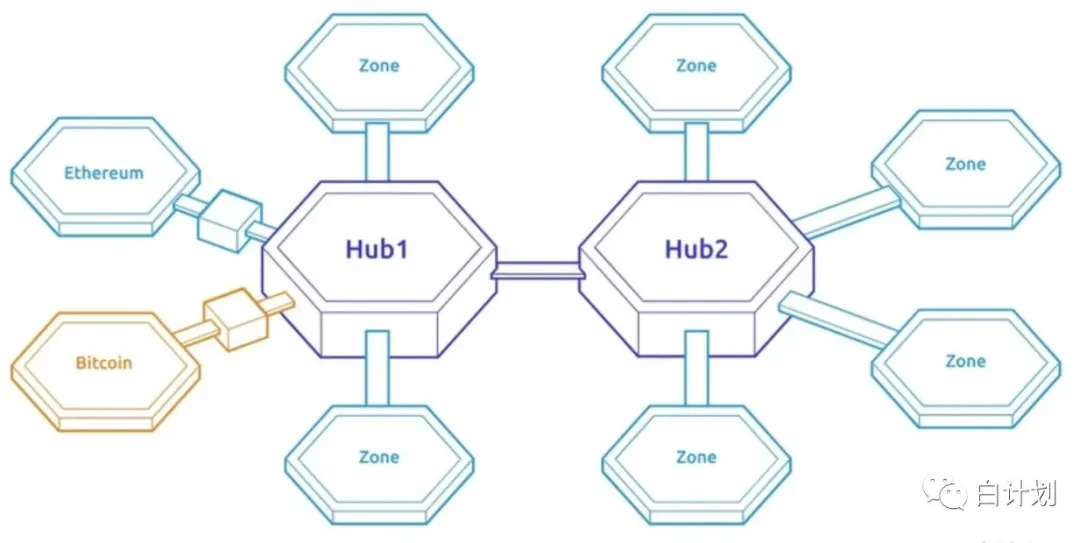
The picture shows the chain structure of COSMOS
secondary title
The specificity of side chain or layer2
The existence of the relay is in the cross-chain structure, which is indeed a multi-chain structure, and in the structure of the only main network in the ecology of Ethereum, all other chains are forked Ethereum, or through a node Synchronize Ethereums data while utilizing the data security of the Ethereum mainnet.This approach is common in sidechains.This structure means that the process of transaction and contract operation is on the side chain, and the structure of the transaction is on the chain. The resulting data is packaged by the Ethereum main network and becomes a proof of security.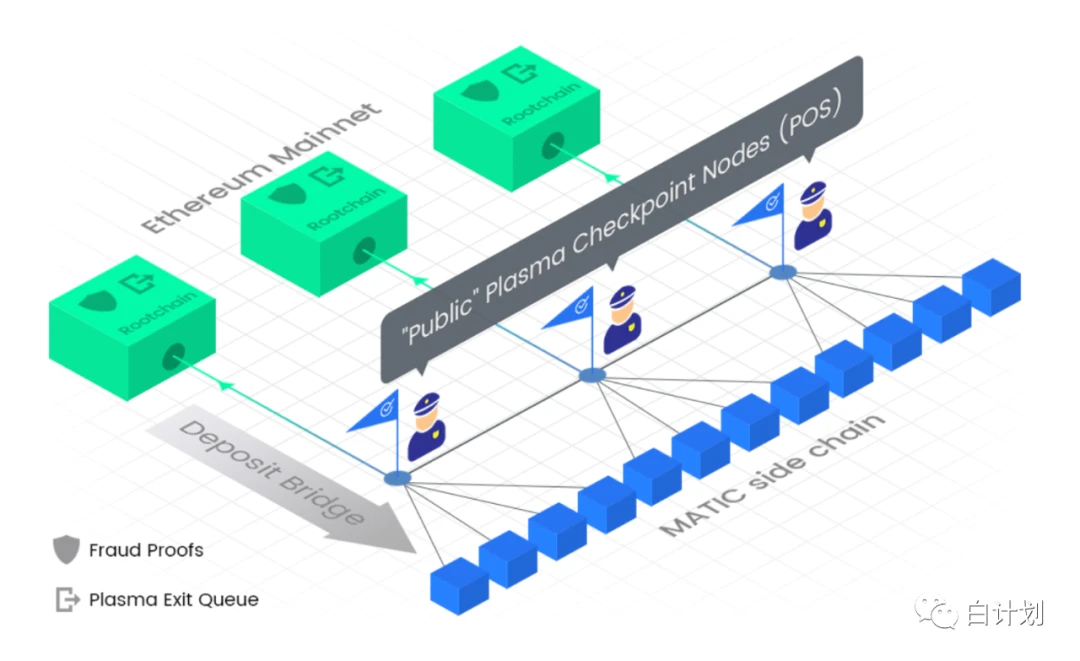
The picture shows the technical structure of Matic, the Ethereum side chain solution
For example, when running Defi on the side chain, the data of ERC20 tokens read and the price of tokens on DEX are all based on the data on the Ethereum chain.
The side chain is a type of Layer 2, and the extensive layer 2 solutions do require the main network to provide security, that is, to provide data confirmation and generate proofs on the chain. There is a logic here that the existence of layer2 is the expansion of the main network. Therefore, whether the layer2 network is an independent network or whether there is consensus is not the main design goal, because many layer2 solutions have no chain, only smart contracts.Sharding and other layered designs in Ethereum
In addition to other designs, the current understanding of the protection between chains, in fact, the sharding structure of Ethereum 2.0 is very obvious.From a structural analysis, sharding is a manifestation of the structure of the main chain and sub-chains. In this structure, the main chain is responsible for the final confirmation, and the security is naturally the responsibility of the main chain.In the future, when the beacon chain is responsible for the block confirmation of the entire Ethereum network, each fragment of Ethereum, that is, a chain divided into independent areas, will have its own small ledger, and then through the communication between fragmented chains In this way, a general ledger is formed, and then the general ledger is packaged by the beacon chain.Here, the function of the shard chain is to calculate, store, and output results, then communicate with the beacon chain, and finally synchronize the general ledger of the beacon chain.Even though Ethereum 2.0 has changed its roadmap now, Ethereum is also using data sharding, which divides the structure of the data generated into independent parts, which is similar to the sharding under the chain, except that it does not divide the nodes of the chain. For individual pieces.The picture shows the layered design idea of Oasis
For example, the consensus layer is designed separately, so that the consensus layer is responsible for the security of the entire network, and those calculations are processed separately in the chain outside the consensus layer. For example, in Oasis Network, the outside of the consensus layer is designed as Paratime, that is, Separate Paratime chains, these chains form their own ledgers and hand them over to the consensus layer, and the security is protected by the consensus layer.For another example, in addition to the consensus layer of Phala, pRuntime is designed, which is a stand-alone chain node running in the TEE, and is also a fragment of each chain. The security of its data is also protected by the data that is confirmed by the consensus layer.The encrypted currency network technology is very mature, because it can be seen from the design of the chain over the years that the project party’s understanding of the solution is enough to create better infrastructure and applications, but what is worth improving is that a chain wants to Success is not determined by technology, but by the operation of the chain. The problem of chain operation is that the project party and entrepreneurs are still groping. 









