first level title
1. Summary of Web3 security situation in the second quarter of 2022
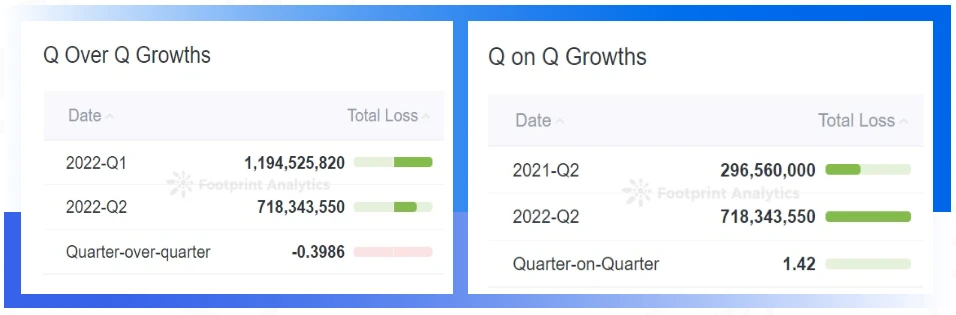
There were more than 48 major attacks, with a total loss of about 718.34 million US dollars
In the second quarter of 2022, the Chengdu Lianan Chain Bing-Blockchain Security Situational Awareness Platform has monitored a total of over 48 major attacks in the Web 3 field, with a total loss of approximately US$718.34 million, compared with US$1.2 billion in the first quarter A drop of about 40%, which is about 2.42 times the loss in the second quarter of 2021 ($296.56 million).
From January to June 2022, the total amount of losses due to attacks in the Web 3 field has reached approximately US$1.91287 billion.In terms of time,
April is the most active month for hacking attacks. In May, the number of attack incidents and the amount of losses both dropped sharply. In June, hacker activity showed a tendency to pick up.From the perspective of the type of project being attacked,
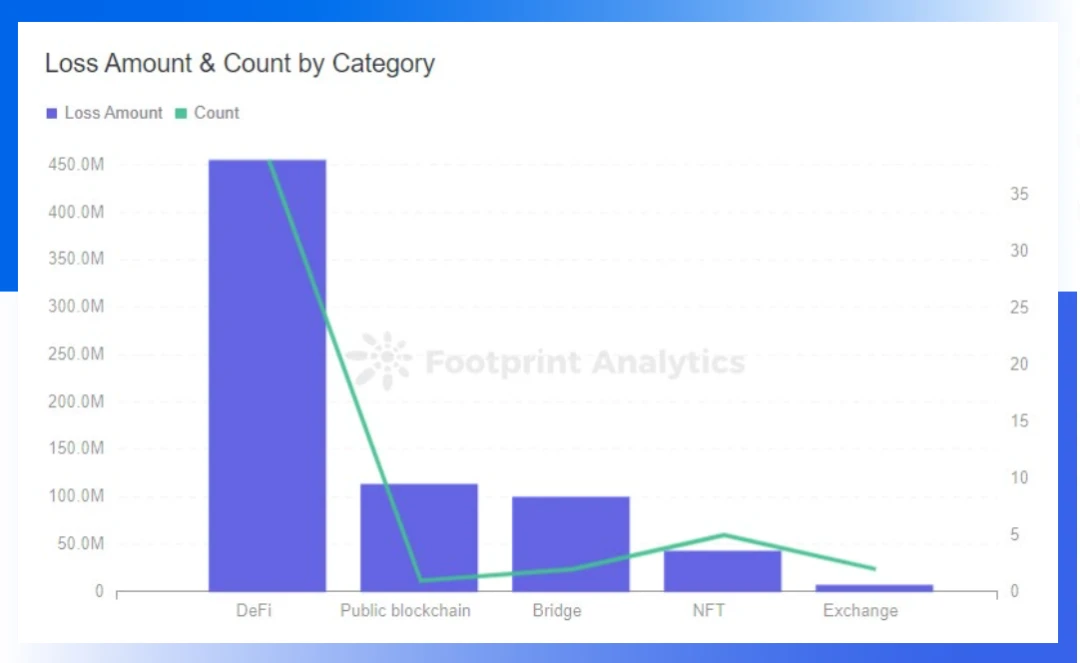
DeFi is still the most attacked project type, and about 79.2% of the attacks occurred in the DeFi field.From the perspective of TVL (Total Locked Value),
The TVL values of all chains and attacked projects have dropped significantly in May. Most projects will experience a sudden drop in TVL after the time point of the attack.From the chain platform point of view,
Ethereum lost the most money this quarter at $381.35 million. The chain with the highest attack frequency is BNB Chain, reaching 26 times.From the point of view of attack methods,
The most common attack methods are still contract exploits and flash loans. About 45.8% of the attacks were contract exploits. The losses caused by flash loans amounted to 233 million US dollars, ranking first in the amount of losses in various attack methods.From the perspective of capital flow,
About $418.89 million in stolen funds was transferred to Tornado.cash by hackers, accounting for 58.3% of the total amount stolen in the quarter.From the audit point of view,
In other respects, a total of more than 43 major Rug pull events on the chain were monitored in this quarter, and the project side took away a total of about US$34,266,402. According to incomplete statistics, there are more than 151 cases of Discord servers being hacked. Rug pull and phishing security incidents occurred frequently in May and June.
first level title
2. Overview of Attack Events
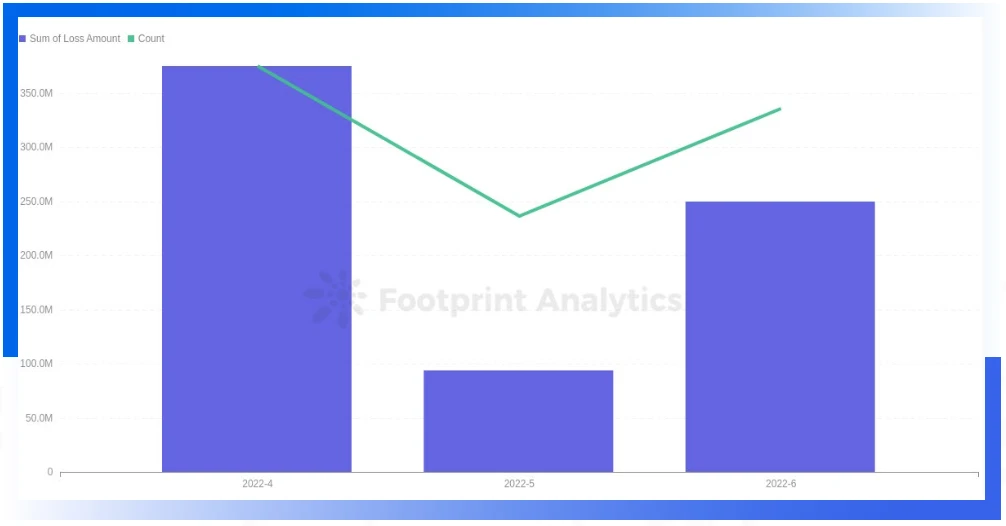
April was the most active month for hacking this quarter
In terms of time, April 2022 is the most active month of hacking attacks in this quarter, with a total of 19 major security incidents and a loss of approximately US$37,489. Both the number of attacks and the amount of losses decreased significantly in May, which may be related to the sharp shrinkage of the entire cryptocurrency market value in May. Although the market did not see a warming trend in June, the frequency of hacking attacks and the amount of project losses increased significantly compared with May.
first level title
3. Types of Attacked Projects
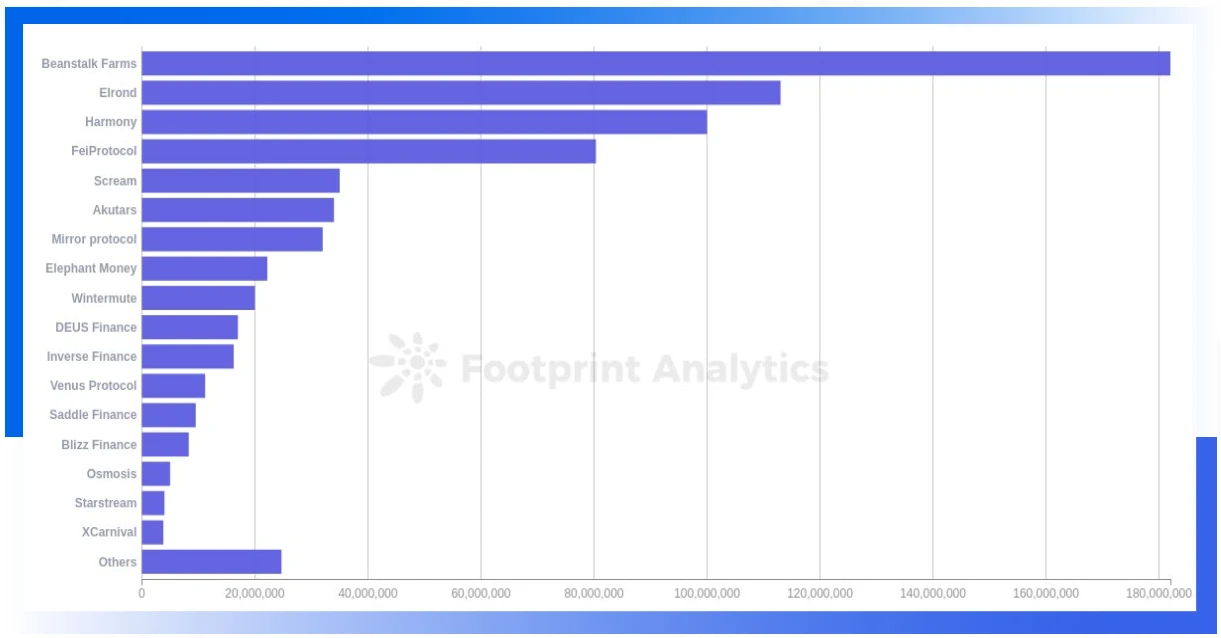
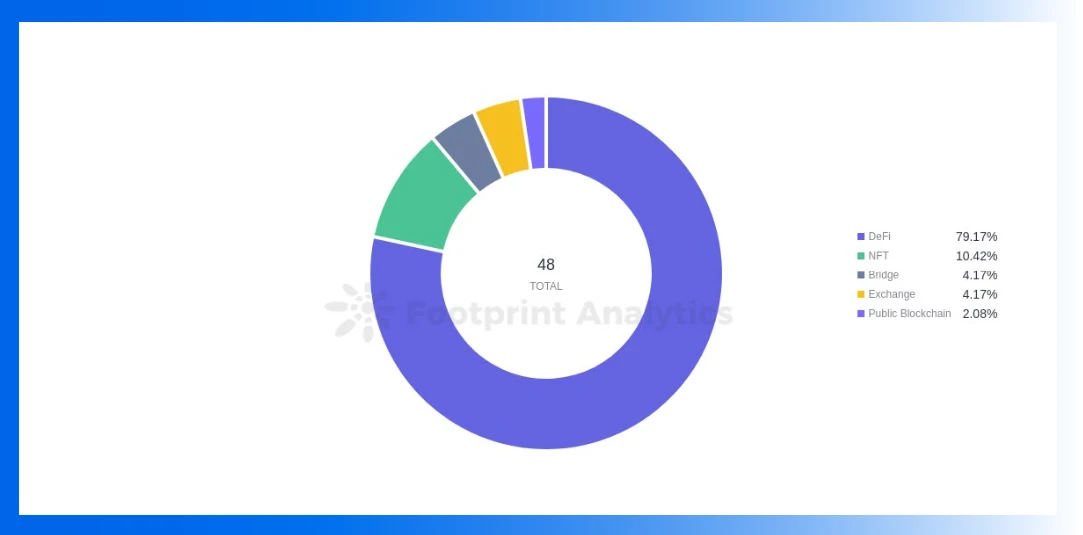
79.2% of attacks occurred in the DeFi fieldSame as the first quarter,DeFi is still the most attacked project type, and about 79.2% of the attacks occurred in the DeFi field.
There were still two cross-chain bridge attacks in this quarter, with a cumulative loss of about $100 million. In the first quarter of 2022, the total loss of 4 cross-chain bridge attacks is 950 million US dollars. So far, the amount of losses caused by cross-chain bridge attacks in the first half of 2022 has reached 1.05 billion US dollars.
first level title
4. TVL analysis of the attacked project
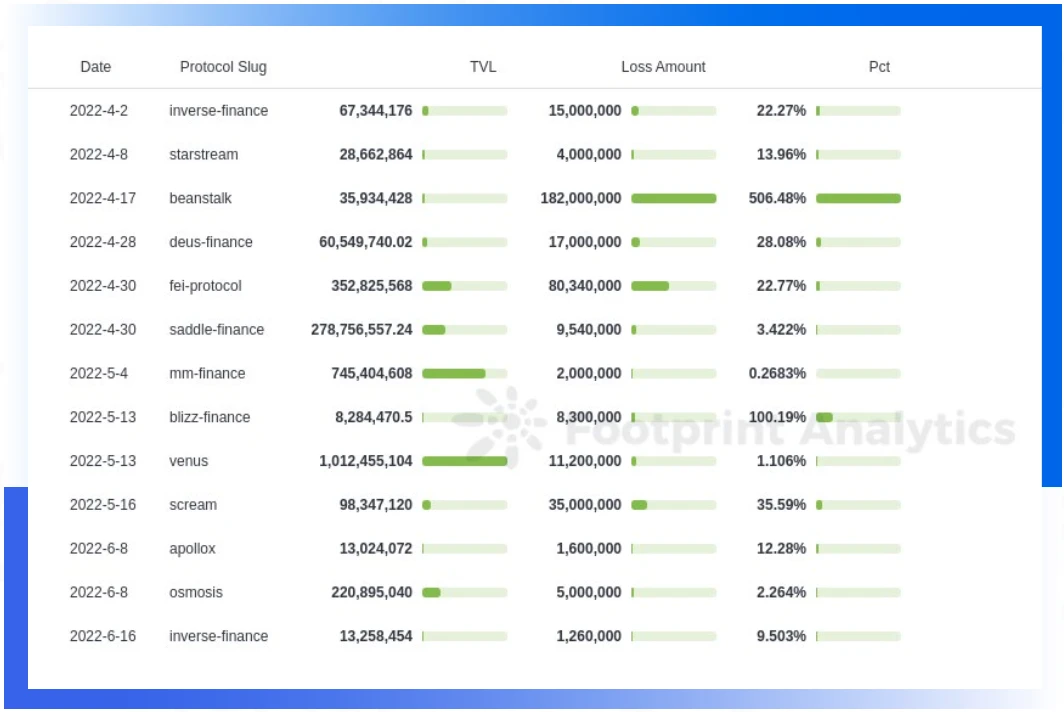
TVL of some projects is directly reset to zero after being attacked
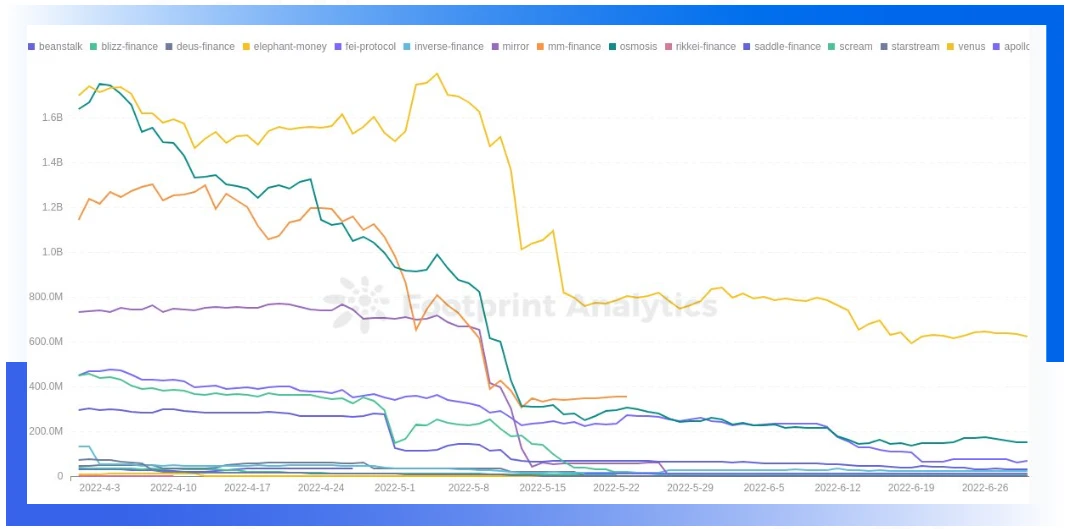
Judging from the ratio of the TVL of the attacked project to the time of the attack, in most cases the amount of loss is less than 30% of the TVL of the project. Among them, there are also individual projects such as Blizz Finance and Beanstalk, whose losses have reached 100% or even 500% of TVL.
first level title
5. The amount of losses on each chain platform
Ethereum has the largest amount of losses, and BNB Chain has the most attack incidents
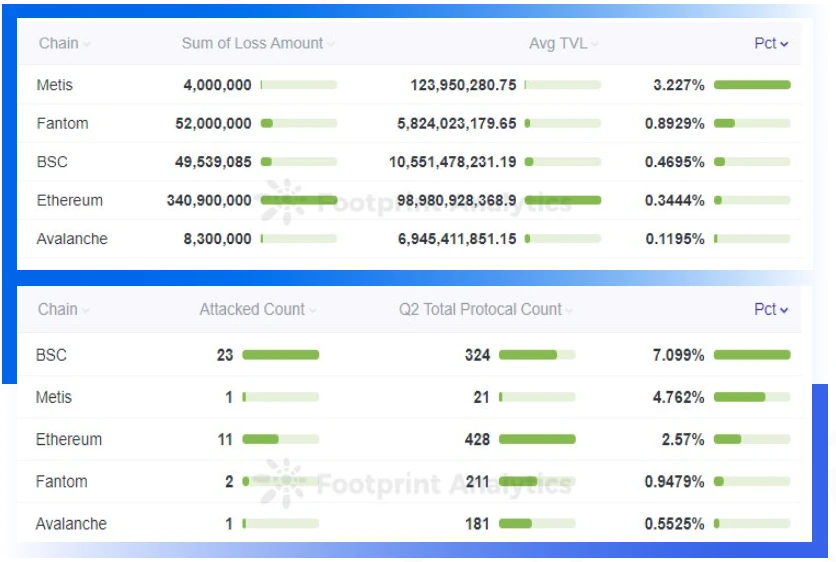
Ethereum lost the most money this quarter at $381.35 million. The chain with the highest attack frequency is BNB Chain, reaching 26 times.
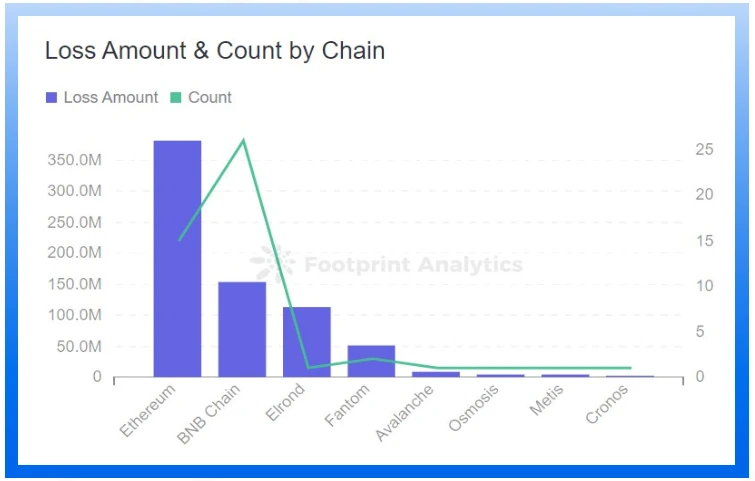
Compared with the previous quarter, the chains that have experienced attacks for two consecutive quarters include Ethereum, BNB, Fantom, and Cronos. The Solana chain, which suffered a loss of $374 million due to two attacks in the first quarter, did not detect any major security incidents in this quarter.
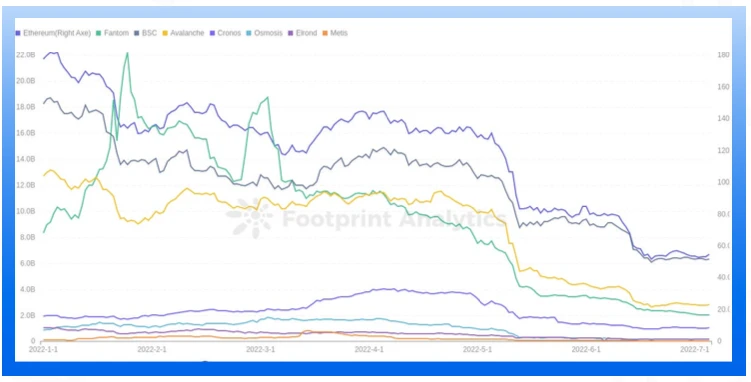
In the second quarter, all chains saw a significant drop in TVL in May. Ethereum and BNB Chain, the top 2 by TVL, are still the main targets of hackers. Attacks this quarter cost a total of $718.34 million, more than the combined TVL of Osmosis, Elrond, and Metis in June.
From the perspective of the number of attacks on DeFi protocols, in the second quarter, the attacked DeFi protocols on BNB Chain accounted for the highest proportion of the total number of protocols, reaching 7%. The DeFi ecology on Metis is not rich enough. Although there is only one attack, it accounts for a relatively high number of transactions and amount.
first level title
6. Analysis of attack methods
The most common attack methods are still contract exploits and flash loans
Exploitation of contract vulnerabilities was the most common attack method in this quarter. 22 attacks were exploits of contract vulnerabilities, accounting for 45.8% of the total. The total loss caused by contract vulnerabilities was about 138 million US dollars. The second most common attack method is flash loan. There were 9 flash loan attacks in this quarter, resulting in a loss of 233 million US dollars, ranking first in the amount of losses of various attack methods.
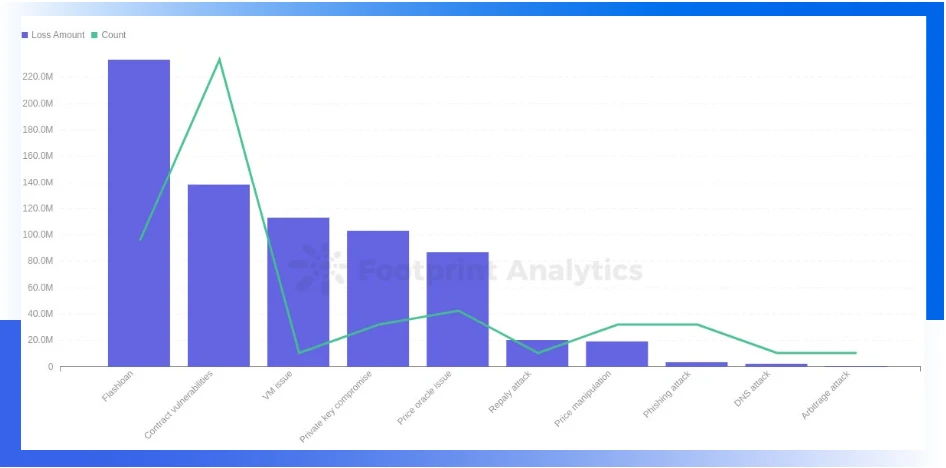
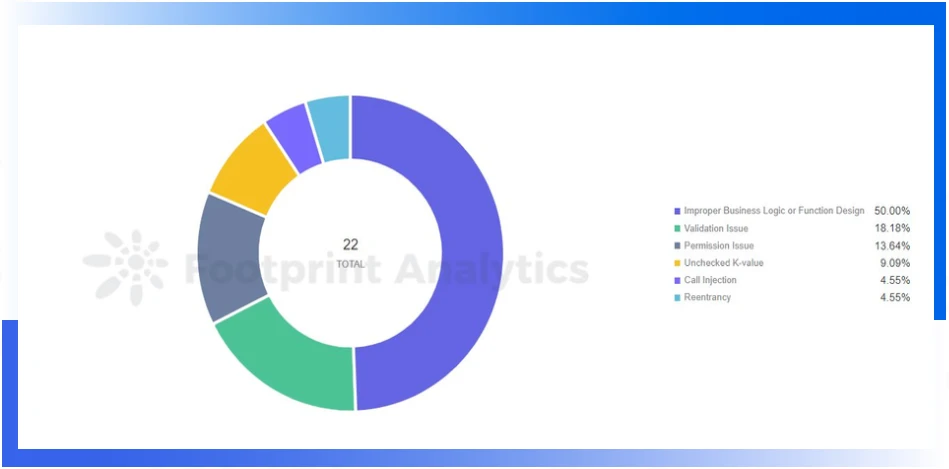
Similar to the first quarter, the most common attack methods in the Web3 field are still contract exploits and flash loans (50% and 24% respectively in the first quarter). In addition, the loss caused by the leakage of the private key still reached 103.15 million US dollars, and the security of the private key is still worthy of attention.Vulnerabilities exploited this quarter mainly include:Among them, the most exploited vulnerability is improper business logic/function design, which is much higher than other vulnerabilities. The re-entrancy vulnerability was exploited once by hackers in this quarter, and the resulting loss reached 80.34 million US dollars.
7. Analysis of attack methods in typical cases
secondary title
7.1 Inverse Finance attacked twice
Event Details:
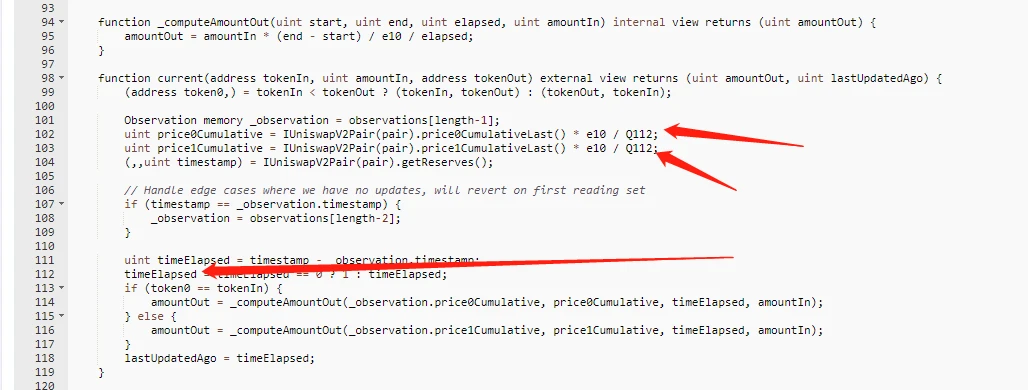
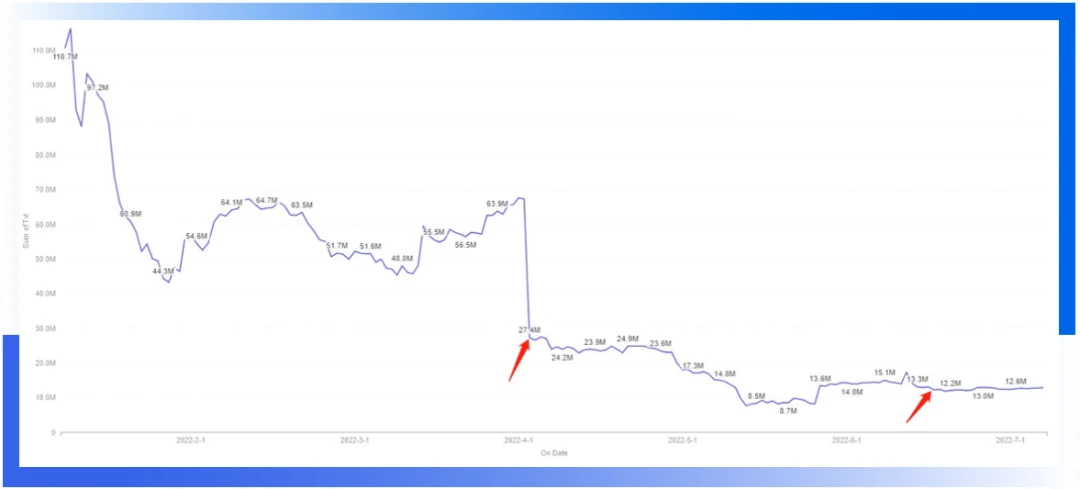
On April 2, 2022, the Inverse Finance project was attacked by price manipulation, and the cumulative loss is estimated to be about 15 million US dollars. The main reason for the attack is that the time window used by the TWAP oracle is too short. When calculating the price of Xinv tokens, rely on the pair of WETH/INV to calculate. Since the pair pool has been manipulated, and the timeElapsed interval is short, the attacker needs to be satisfied that the call is not in the current block to manipulate the value of the xINV token.
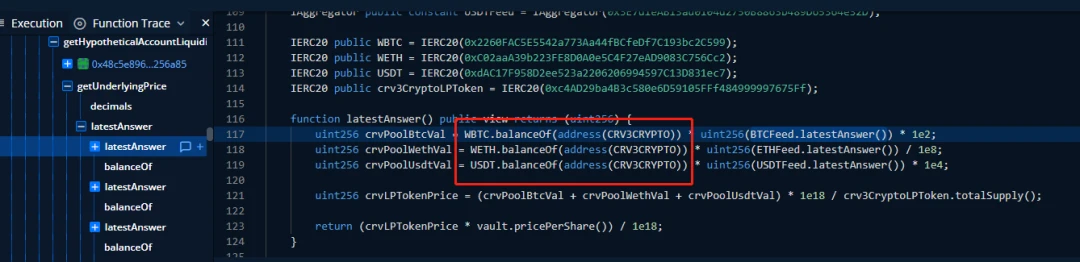
Security advice: Avoid relying on the real-time balance of tokens when obtaining token prices, but use TWAP-type price oracles and set a sufficient time window.
secondary title
7.2 Akutars: $34 million locked and unable to withdraw due to smart contract bug
Event Details:
On April 24, 2022, $34 million in the NFT project Akutars was locked and could not be withdrawn due to a smart contract vulnerability. Notably, the project’s contracts have not been audited by security firms. After analysis, it was found that Akutars contract contained two vulnerabilities.
Vulnerability one:
The first contract vulnerability is in processRefunds, where the designer performs circular refunds based on the refundProgress counter. Here, the call function is used for the refund operation, and the result of the refund is used as the judgment condition of require. Therefore, if an attacker performs a refund operation in the queue at this time, when the call refund is called to the attacker, the attacker performs a malicious revert in the fallback, and everyone behind the queue will not be able to refund. Fortunately, this vulnerability was not actually exploited by attackers.
Vulnerability two:
This vulnerability is the direct cause of approximately $34 million worth of assets being locked in the contract.
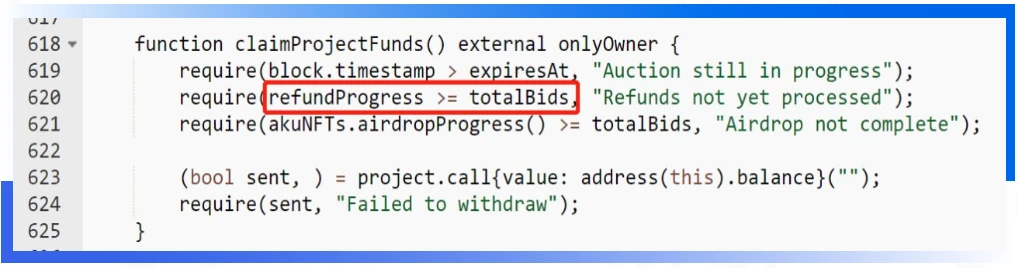
In the claimProjectFunds function, this function is mainly used for withdrawal by the project side. In the function require (refundProgress >= totalBids), where refundProgress indicates how many refunds of users have been processed, and totalBids indicates how many NFTs all users have bid for in total. Since a user can bid for multiple NFTs, refundProgress may be less than totalBids in numerical comparison.
In the refund function processRefunds: require(_refundProgress < _bidIndex); bidIndex means all users participating in the bidding, refundProgress will never be higher than bidIndex. The value of bidIndex is 3669, and the value of totalBids is 5495.Therefore, refundProgress>=5495 and refundProgress
Security suggestion: Professional security audit before the project goes online is very necessary.
secondary title
7.3 Beanstalk Farms: Hackers made nearly $80 million in profits. How to prevent malicious proposals?
On April 17, 2022, Beanstalk Farms, an algorithmic stable currency project, was attacked by a flash loan. The hackers made a profit of nearly US$80 million and the protocol lost US$182 million. This is the item with the highest amount of losses this quarter.
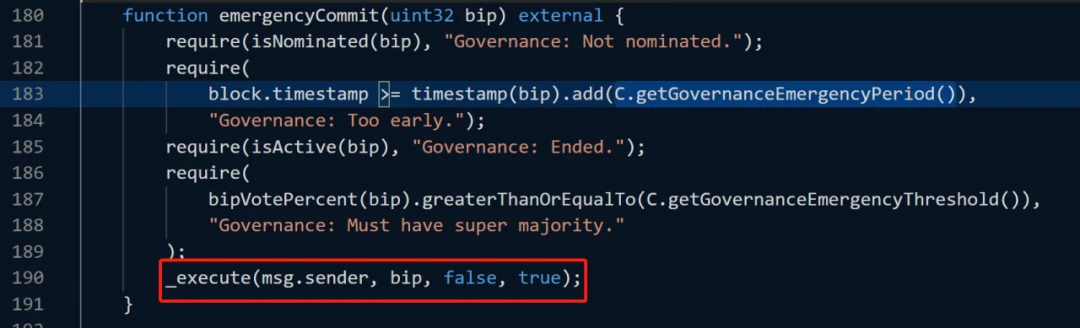
Looking back at this attack, the attacker initiated a proposal to withdraw funds from Beanstalk: Beanstalk Protocol the day before, and then called emergencyCommit for an emergency commit to execute the proposal. This is because the project party stipulates that voting can only start 1 day after the proposal.
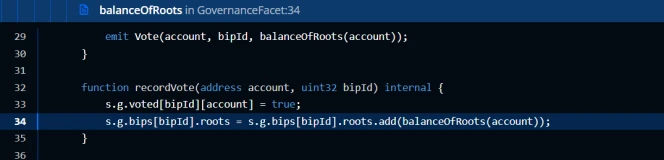
During the attack, the attacker took advantage of the loophole that the number of votes in the voting contract is calculated by the accounts proposal token holdings, lent a huge amount of funds worth 1 billion US dollars through flash loans, exchanged tokens and invested them in the mining pool , temporarily obtain a huge amount of proposal tokens, which ensures that the proposal can be passed without other people voting. Finally, the proposal was passed and executed, and the attacker successfully withdrew the funds of the project party, then exchanged and repaid the flash loan, and left the market with a profit.
Safety advice:
1. The funds used for voting should be locked in the contract for a certain period of time, and avoid using the current fund balance of the account to count the number of votes;
3. Consider prohibiting contract addresses from participating in voting.
first level title
Eight, capital flow analysis
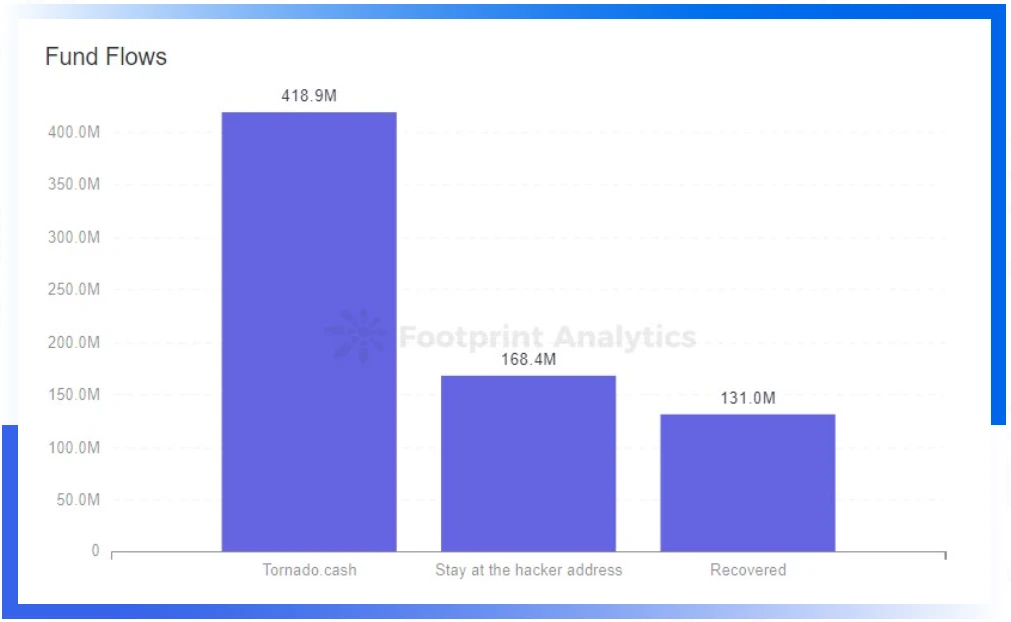
About $418.89 million in stolen funds flowed into Tornado.cash
From the perspective of funds flow, in the second quarter of 2022, about US$418.89 million of stolen funds were transferred to Tornado.cash by hackers, accounting for 58.3% of the total stolen amount in the quarter. In addition, 131 million US dollars of assets were recovered, and 168.45 million US dollars of assets remained in the hackers address and have not yet been mixed or flowed into exchanges.as shown by data,The recovery of funds in this quarter is better than that of the previous quarter. In some cases, the project team will negotiate with hackers through information on the chain, and some hackers will choose to return a certain amount of stolen money to exempt from legal sanctions.
first level title
9. Analysis of Project Audit
Only 52% of projects are audited
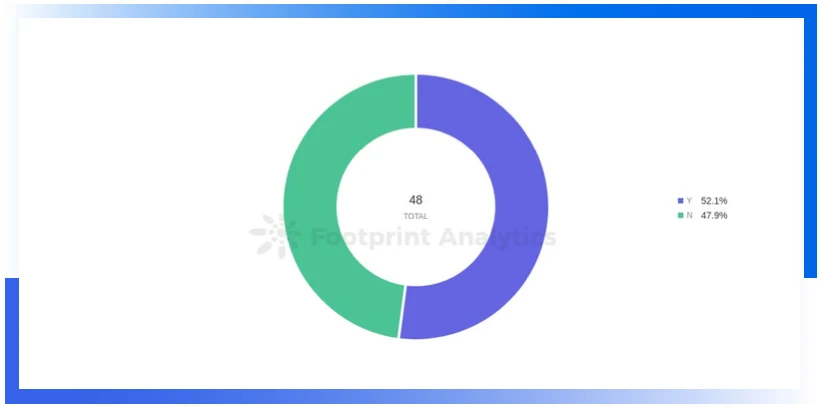
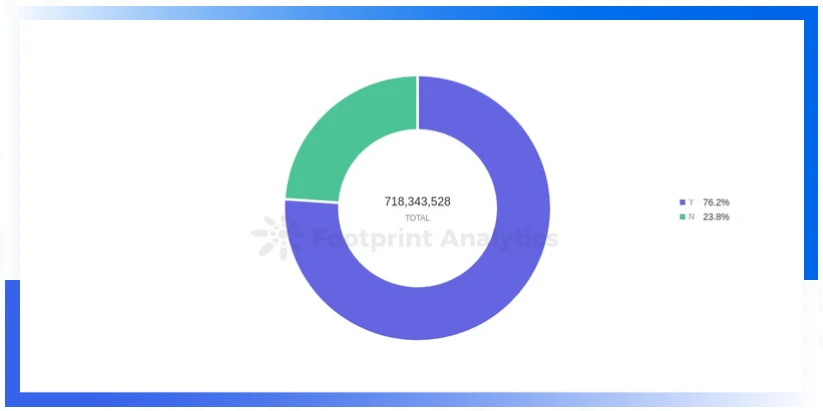
Only 52 percent of the projects attacked were audited, compared to 70 percent in the previous quarter. The audited project losses due to attacks in this quarter amounted to 547.63 million US dollars, accounting for 76.2% of the loss amount, much higher than the previous quarter.
While audited project losses still amounted to $547.63 million, that doesnt mean audits are no longer important.As more and more security companies step into the audit business,The audit market is uneven and mixed. Due to some unprofessional companies, some loopholes in smart contracts that should have been audited were not auditedTherefore, some project parties and investors began to question the necessity and professionalism of the audit, thinking that an audit is also a white audit.Therefore, it is recommended that the project party must find a professional security company to conduct an audit before the project goes live.
first level title
10. Rug pull analysis
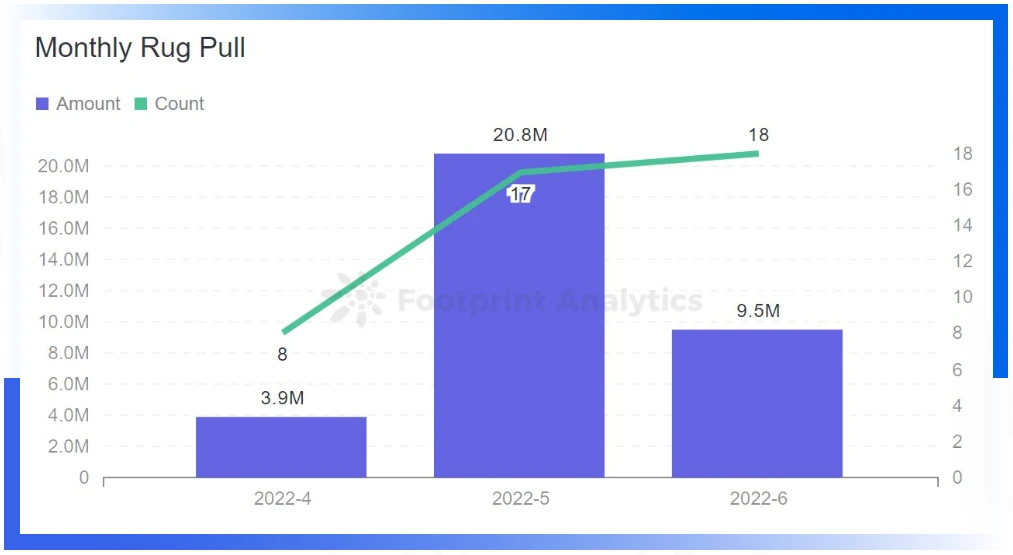
The project party took away a total of about 34.266402 US dollars
Rug pull usually refers to the developer withdrawing from the DEX liquidity pool or suddenly abandoning a project, taking away investors funds without warning, which is commonly known as running away. In the second quarter of 2022, a total of 43 major Rug pull incidents on the chain were monitored, and the project side took away a total of about US$34,266,402.In May, when the TVL of various public chains and projects shrank sharply, some project parties chose Rug pull, which caused a large number of investors to suffer losses. The reason may be that it cannot continue to operate, or it may be that it is better to run away than wait for the TVL to return to zero, or it may be that it is premeditated to run away, but the sharp decline in TVL has accelerated this process.
first level title
11. Discord Phishing Analysis
Discord phishing cases occur frequently this quarter
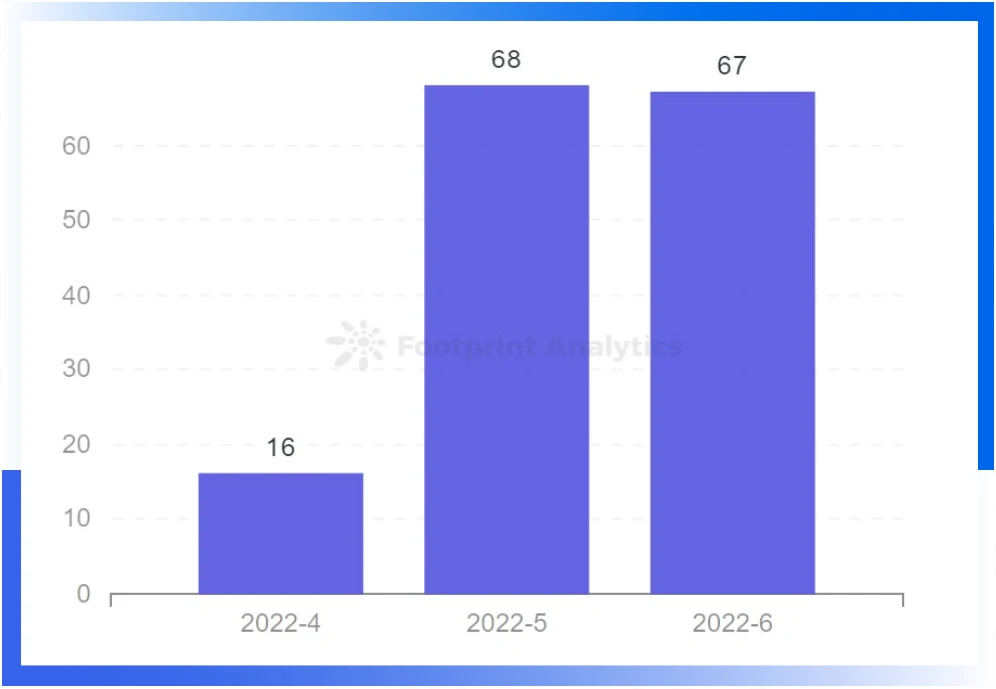
Similar to the Rug pull data, phishing security incidents may actually increase in a downturn in the market. Discord phishing methods appeared in this quarter in various forms, such as robot accounts being hacked, pretending to be administrators or robots sending phishing links in private messages, disseminating high imitation Discord invitation links through social media, and so on. The more bearish the market is, the more users and project parties should raise anti-fraud awareness and protect their assets.
first level title
12. SummaryIn the second quarter of 2022, DeFi security is still the focus of attention, and about 79.2% of attacks occurred in the DeFi field.For two consecutive quarters, DeFi has been the focus of hacker attacks. Although the frequency of NFT, cross-chain bridge, and exchange security incidents is not as high as that of DeFi, the amount involved in individual incidents is also huge.
Therefore, all types of Web 3 project parties should strengthen security awareness and do a good job in security protection.About 45.8% of the attacks this quarter were contract exploits,Most of these vulnerabilities can be found and fixed during the audit phase.
Of the projects attacked this quarter, only 52% were audited. It is recommended that the project find a professional audit company for auditing before going online.During the quarter, approximately $418.89 million in stolen funds were laundered into Tornado.cash by hackers. In addition, about 131 million U.S. dollars in assets were recovered, but most of the recovery methods were negotiated with the hackers on the chain, allowing the hackers to return some of the stolen funds. In fact, it is not impossible for the stolen funds to enter the tornado.
Chengdu Lianan has accumulated many successful cases in assisting in the tracking of stolen funds, including some funds entering the tornado. It is recommended that when the project party is unfortunately hacked, in addition to negotiating with the hacker to return it, it can also seek some professional security companies to track funds.In this quarter, the TVL values of various public chains and projects have fluctuated greatly, and there are also situations where project funds are abnormal or risky transactions occur due to various security incidents. It is recommended that both the project party and investors pay attention to the project operation in a timely manner
. Chengdu Lianan [Chain Bing-Blockchain Security Situation Awareness Platform] allows project parties and users to discover risky transactions in a timely manner, so as to quickly take measures.In the sluggish market this quarter, various security incidents such as Rug pull and phishing have occurred more frequently, and some Web 2 attack methods are still active in the Web 3 field.
All project parties and users should raise their security awareness, keep their private keys safe, do not click on links from unknown sources, and conduct multi-channel verification of various information.
https://chrome.google.com/webstore/detail/beosin-alert/lgbhcpagiobjacpmcgckfgodjeogceji?hl=zh-CN
Web anti-phishing weapon:










