Original - Odaily
Author - Qin Xiaofeng

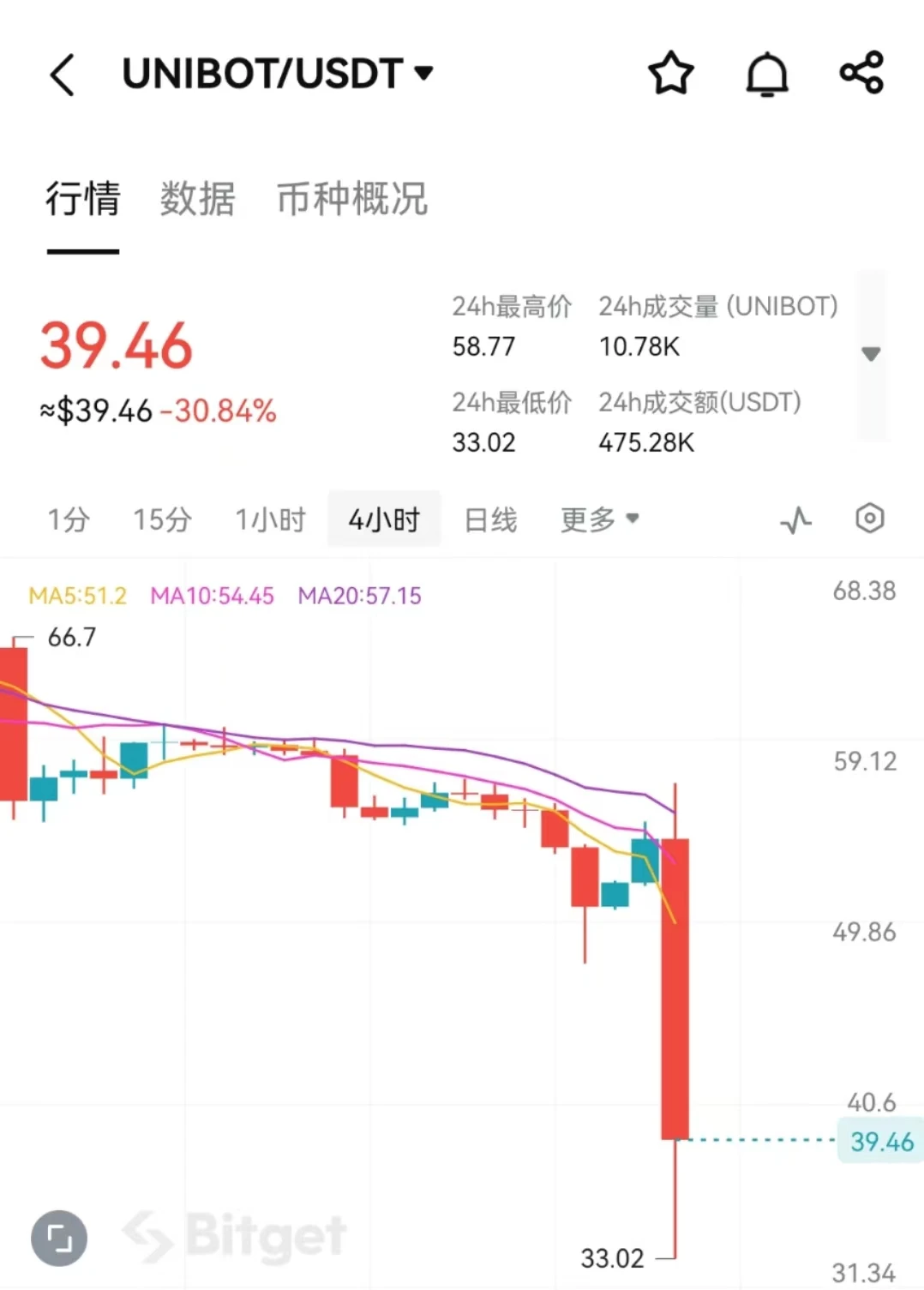
This afternoon, many community members reported that the Telegram Bot project Unibot was attacked. According to Scopescan monitoring, the attacker transferred tokens from Unibot users and was exchanging them for ETH. The current loss has exceeded $600,000.
As soon as the news came out, the token UNIBOT dropped from 55 USDT to 33 USDT, with a maximum drop of 40%. It is currently trading at 39.5 USDT.
Security companies: cancel authorization as soon as possible
Security agency BlockSecTeam analyzed that because the code is not open source, it is suspected that the function 0xb2bd16ab in the 0x126c contract lacks input verification, allowing arbitrary calls. Therefore, an attacker can call transferFrom to transfer tokens approved in the contract. BlockSecTeam reminds users to revoke contract approval as soon as possible and transfer funds to a new wallet.
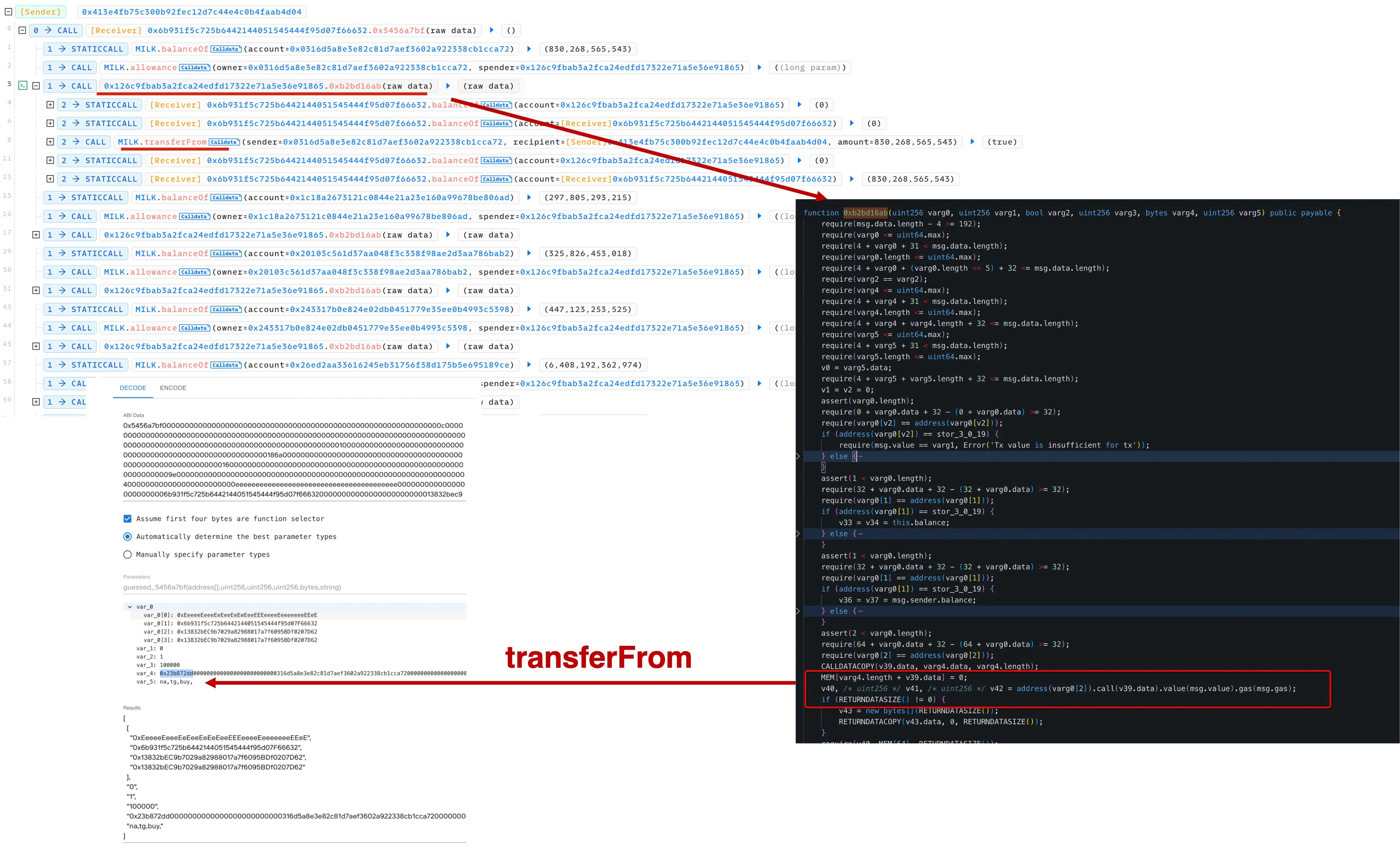
Beosin security team analysis believes that the root cause of Unibots attack is CAll injection. Attackers can pass custom malicious call data to the 0xb2bd16ab contract, thereby transferring tokens approved by the Unibot contract. Beosin Trace is tracking the stolen funds, and Beosin reminds users to cancel wallet authorization on Revoke, link: https://revoke.cash/. The attack-related addresses are as follows:https://eagleeye.space/address/0x413e4Fb75c300B92fEc12D7c44e4c0b4FAAB4d04
Hackers lay dormant for half a year to carry out attacks
One strange thing about Unibot this time is that the hacker address has been squatting since the Unibot contract was deployed in May this year. According to Scopescan monitoring, the hacker received 1 ETH from FixedFloat (coin mixer) as the gas for this attack one week after Unibot was launched. There was no related action for the next six months until the attack today.
Many users in the crypto community speculated that this attack may be the work of Unibot insiders, because the time of the incident was very coincidental, which happened to be the window period after Unibot changed to a new contract (the new contract was upgraded just two days ago), and the hackers easily found it. Contract loopholes.
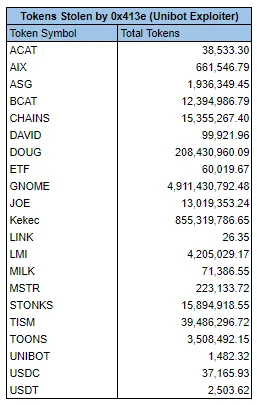
Information on the chain shows that the hacker’s wallet address currently has approximately US$630,000 in remaining assets. The largest proportion of remaining assets is ETH, which is approximately US$573,000. Other stolen assets involve currencies as follows:
In addition, according to Lookonchain monitoring, a users assets were stolen twice in this attack. The user account initially received 20,789 USDC and spent $1,000 to purchase SMilk. The remaining USDC worth $19,789 was stolen by the attacker, but the user did not notice it yet. This afternoon, the user sold SMilk at a price of $2,194 and earned $1,194 (120% yield); an hour later, the last remaining $2,194 of USDC was stolen again.
Routers have vulnerabilities and attacks continue
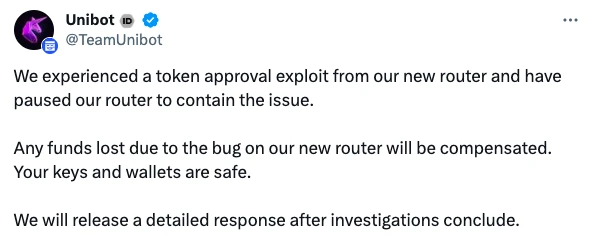
Unibot officially announced that this attack is mainly due to a token approval vulnerability in the new router (router), and the router has been suspended; any financial losses caused by the vulnerability will be compensated, and Unibot will release details after the investigation is completed. reply.
Community user @tomkysar said that attacks against Unibot are still continuing. Two attacker addresses still seem to be able to obtain funds from addys approved by 0x126 Router, and user funds are still at risk.
BOT product safety is questionable
Unibot is a popular new Telegram Bot that allows users to trade cryptocurrencies without leaving the Telegram app. The bot is easy to use, trades quickly, and offers features such as decentralized copy trading, DEX-based limit orders, and protection against MEV bots.
According to CoinGecko data, UniBOT has earned 8,950 ETH since its establishment, ranking second among all BOT products; Maestro ranks first, with a cumulative earnings of 13,200 ETH; Banana Gun ranks third, with earnings of 1,940 ETH.
However, BOT products also have major security risks, especially the same router vulnerability that recently appeared in the Maestro contract, resulting in a loss of approximately 281 ETH - this vulnerability allows attackers to transfer their Router 2 contract (https://etherscan.io/address/0x80a64c6d7f12c47b7c66c5b4e20e72bc1fcd5d9e…) has been approved on any token. In the end, Maestro chose to compensate users for part of their losses.










