Original article by May Pang , Chief Compliance Officer@OORT
Introduction
When DeFi protocols encounter the right to be forgotten of GDPR, and when NFT platforms face the right to withdraw data of CCPA, the blockchain industry is experiencing a fierce collision between the ideal of decentralization and the reality of regulation. According to the Chainalysis report, fines for global blockchain companies due to privacy compliance issues increased by 240% year-on-year in 2023. This article will deconstruct how blockchain projects can build compliance competitiveness in the Web3 era.
I. Core similarities and differences in global privacy regulations
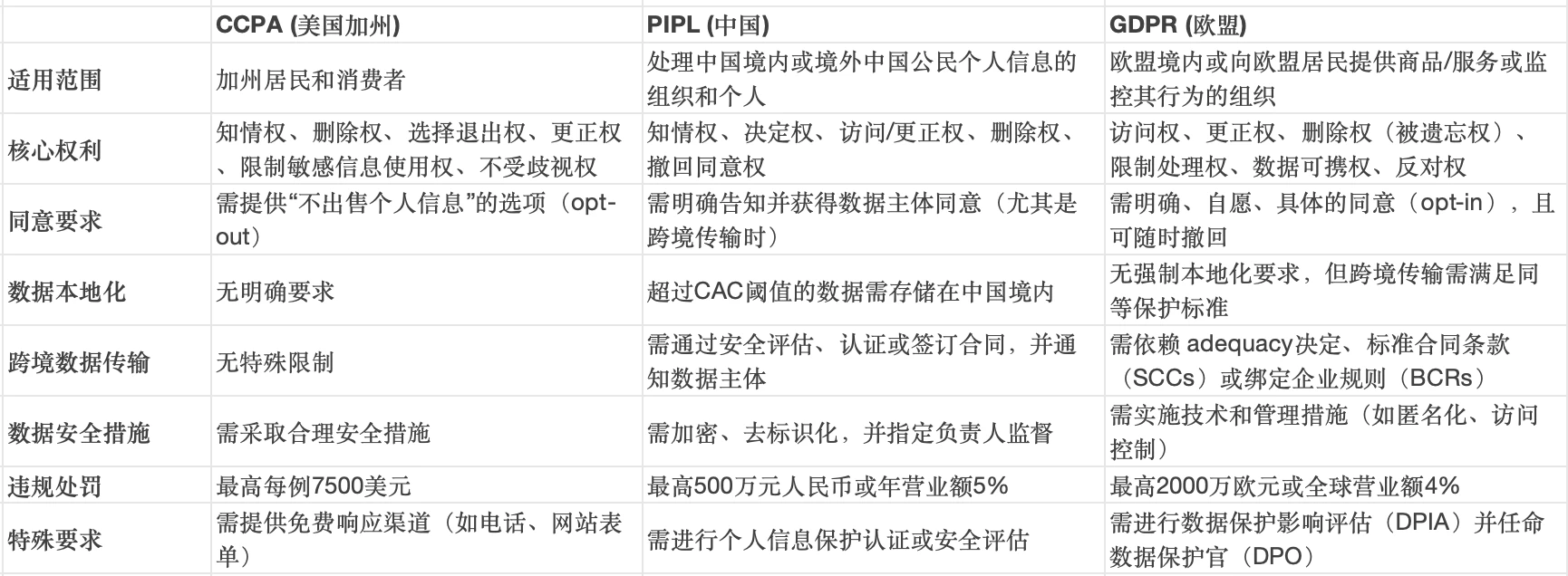
As data privacy issues have become increasingly important, Californias CCPA, Chinas PIPL, and the EUs GDPR have become three representative regulations. Although all three are aimed at protecting personal data, their focus and specific requirements are significantly different.
In terms of scope of application, CCPA only applies to California residents, while PIPL and GDPR have extraterritorial effect, covering scenarios where data of citizens of the country is processed overseas. In terms of core rights, GDPR is the most comprehensive, granting users the right to be forgotten and right to data portability; PIPL emphasizes the right to control the entire process of data processing; CCPA focuses on the right to be informed and the right to opt out. In cross-border data transfer, PIPL has the most stringent requirements and requires security assessment or certification; GDPR relies on standardized tools; CCPA has no special restrictions.
The differences in compliance measures are also worth noting: PIPL and GDPR both require data localization or cross-border assessment, while CCPA focuses more on transparency (such as providing a do not sell link). In terms of penalty intensity, GDPR and PIPL are calculated based on the proportion of turnover, which is more deterrent.
2. Conflicts between blockchain characteristics and privacy regulations and solutions
1. The paradox of immutability and the right to delete
The core feature of blockchain, immutability, makes it the cornerstone of trust machines. However, this feature directly conflicts with the right to be forgotten (Right to Erasure) in the three major privacy regulations. When users request to delete data, the only add but not change ledger feature of blockchain leads to compliance difficulties. How to balance data immutability and legal right to delete? The following is an exploration of technical solutions.
1.1 User Data Sovereignty Network: Ceramic Protocol
The core idea is to decouple sensitive data from the blockchain, save only hashes, and manage the original data by the user. Through the Ceramic protocol, data is stored in a decentralized storage network (such as IPFS), and the private key is controlled by the user. The blockchain only saves the data fingerprint (hash), and the private key can be destroyed when deleted to invalidate access. Successful cases include: Mask Network users use Ceramic to store encrypted social data (such as posts, follow lists), and IDX users use Ceramic streams to store verifiable credentials (such as KYC certificates, social account binding).
1.2 Logical deletion: Arweave+ZK-Rollup
A real-life example is Immutable Xs removal of infringing NFTs. The core idea is to physically store the data, but achieve logical invisibility through zero-knowledge proof (ZKP). In specific implementation, Arweave permanent storage can be used to write data into an unalterable layer, and then through the ZK-Rollup compliance layer, after the content is removed from the shelves, the verifier can reject transactions containing the data.
1.3 Dynamic permissions on consortium chains: Hyperledger Fabric private datasets
The core idea is to control data visibility through node permissions in a permissioned chain. For example, in an enterprise alliance chain, the implementation method is to set up private data collections so that sensitive data is only visible to authorized nodes and dynamically delete the data. For example, alliance members can vote to remove non-compliant data (such as the medical chain deleting erroneous medical records).
1.4 Programmable Privacy Layer: Aleo’s Opt-Out Mechanism
The core idea is to support selective disclosure with regulatory intervention under the premise of protecting privacy. User data is encrypted on the chain through zero-knowledge proof (zkSNARK), and the view key (View Key) is provided to the regulator when necessary, or Opt-Out deletion (such as hiding transaction history) is performed. Aleo provides financial institutions with compliant privacy transaction solutions.
2. The balance between anonymization and KYC
The worlds three major privacy regulations all have strict requirements for anonymization of personal information processing. At the same time, anti-money laundering (AML) regulations also require KYC verification. How can the blockchain industry find a balance between these two contradictions? Here are three innovative solutions.
2.1 ENS + Decentralized Identity (DID): Controllable Identity Disclosure
The core idea is to use Ethereum Name Service (ENS) as a readable identity identifier instead of directly exposing the real name, combined with decentralized identity protocols (such as Ceramic IDX, Spruce DID), allowing users to choose what information to disclose. Uniswap Wallet uses this technology to support ENS aliases and reduce the risk of address exposure.
2.2 Polygon ID: Zero-knowledge proof (ZKP) to minimize KYC
The technology uses zero-knowledge proofs to allow users to prove that they meet the requirements (such as over 18 years old) without revealing their specific age or ID number, and does not store the original identity data, only the proof. After verification, transactions can use anonymous addresses (such as zkRollup accounts). Users can also revoke credentials and stop data sharing at any time. This operation can meet the minimum necessary principle of the three major regulatory compliance requirements and only collect necessary information.
2.3 Circle TRUST Framework: The Tradeoff between Stablecoin Compliance and Privacy
TRUST (Travel Rule Universal Solution Technology) is a compliance protocol proposed by Circle (issuer of USDC) that allows VASPs to share KYC data securely without exposing it to the public. End-to-end encryption and permission access control are used to ensure that only compliant institutions can view the identity of traders. The framework is compatible with the FATF Travel Rule, meeting regulatory requirements while protecting user privacy. At the same time, the framework is a non-custodial architecture, that is, user data is not controlled by a single centralized institution, reducing the risk of leakage. The TRUST framework is also auditable, ensuring that regulators can access it on demand, but ordinary users cannot track it.
3. Smart contracts and data subject rights
All three regulations emphasize that individuals, as data subjects, have the right to decide on their own information. However, many current blockchain projects, including DAO operations, still cannot get rid of neutral governance. For example, Uniswap still relies on centralized front-end or foundation decisions, resulting in the users data rights being emptied. How can smart contracts truly respect the rights of data subjects? The following are two solutions that can be considered:
3.1: Aave introduces the Data Processing Impact Assessment (DPIA) mechanism for DAO voting
DPIA (Data Protection Impact Assessment) is a mandatory assessment process stipulated by GDPR, requiring companies to assess privacy impacts before processing high-risk data. The on-chain DPIA proposal requires that any changes involving user data (such as adding a KYC module, log storage strategy) must be voted on by DAO members, and the proposal must also be accompanied by a privacy impact analysis (such as whether the change increases the risk of data leakage), while deploying compliant smart contracts, managing user authorization through verifiable credentials (VC), and establishing a penalty mechanism. If the DAO passes a proposal that violates GDPR, its staked governance tokens (such as AAVE) can be confiscated. DAOs such as Aave have introduced it into on-chain governance to ensure transparency of its data decisions.
3.2: Filecoin implements automated data lifecycle management
The storage restriction principle of GDPR requires that data be retained only when necessary, and Filecoin, as a decentralized storage network, can achieve automatic expiration and deletion through smart contracts to avoid permanent storage violations. When users upload data, they set a storage period (such as automatic deletion after 1 year), and the Filecoin node performs cleanup after expiration. The storer does not need to disclose the content of the data, but only needs to prove that it has been deleted as agreed (such as submitting a deletion certificate through zk-SNARK). If the NFT platform uses Filecoin to store art metadata, it can embed automatic delisting logic (such as triggering deletion after copyright expiration). For example, Ocean Protocol automatically revokes data usage rights upon expiration.
4. PIPL cross-border transmission breakthrough
For Chinese companies, with the official implementation of the Personal Information Protection Law (PIPL) in November 2021, the regulatory environment for cross-border data flows faced by companies has undergone fundamental changes. Article 38 of the PIPL clearly stipulates that the export of personal information must go through compliance paths such as security assessments, standard contracts or certifications. This regulation poses a unique challenge to the blockchain industry - how to meet the compliance requirements of cross-border data transmission while maintaining the characteristics of distributed ledgers? The following are the technological innovations and compliance wisdom of Chinese blockchain companies in the PIPL era in recent years, which are of reference significance to other projects.
4.1 Changan Chains Regulatory Sandbox Model: Main Chain-Subchain Architecture Innovation
As Chinas self-controlled blockchain underlying technology platform, Changan Chain innovatively proposed a two-layer architecture design of domestic main chain + overseas sub-chain, providing a technical implementation path for PIPL compliance. Its domestic main chain stores original data, and the overseas sub-chain only stores data hash values and necessary transaction information. By deploying a cross-border transmission gateway certified by the Cyberspace Administration of China, refined control of data flow is achieved, and regulatory nodes with special permissions are set up in the sub-chain to meet audit requirements.
4.2 Oasis Network Privacy Computing Framework: The First Overseas Blockchain to Pass the Cyberspace Administration of China’s Security Assessment
In 2023, Oasis Network became the first overseas blockchain project to pass the security assessment of the Cyberspace Administration of China. Its privacy computing framework provides an innovative solution for cross-border data flow. It uses TEE (Trusted Execution Environment) technology to achieve data available but invisible, adds noise to the data analysis link to protect individual privacy, and sets up a permissioned blockchain through the access control (RBAC) mechanism. Finally, the dual mechanism of data desensitization + access control meets the PIPL requirements.
4.3. Ant Chain Trusple Platform: Best Practices for Standard Contract Recording
Ant Chains international trade platform Trusple has created a benchmark case for PIPL compliance by innovatively combining smart contracts with standard contracts. Its smart contract filing encodes standard contract terms into executable smart contracts, verifies cross-border transmission conditions in real time through oracles, achieves automated compliance, and records all transmissions on the chain to meet regulatory audit requirements.
Conclusion
The integration of blockchain and privacy regulations is by no means a zero-sum game. As Ethereum founder Vitalik Buterin said: The next generation of privacy protocols must have compliance embedded in their DNA. Projects that translate regulatory requirements into technical features are defining a new paradigm for the Web 3 era - both defending the spirit of decentralization and building a sustainable compliance moat.










