How the attack occurs Event overview
#1 Event Overview
How the attack occurs Event overview
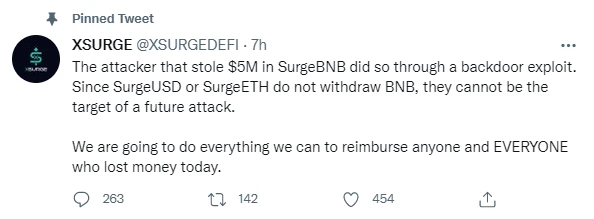
The DeFi project XSURGE encountered a flash loan attack today, but before XSURGE was attacked, the official statement on the SurgeBNB vulnerability was released.
XSURGE stated that a potential security vulnerability in the SurgeBNB contract was discovered on August 16 local time. Since the SurgeBNB contract is immutable and abandoned, the token cannot be retroactively patched. XSURGE did not disclose any specific details about the nature of this vulnerability, but users are strongly advised to migrate out of SurgereBnb as soon as possible, because the vulnerability may be triggered by an attacker at any time.
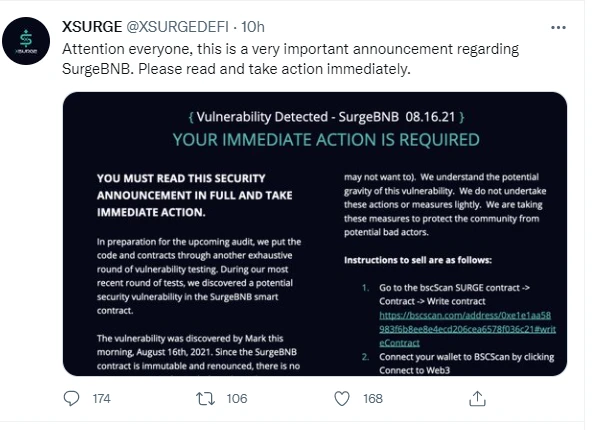
It was too late to say that, after the statement was released, XSURGE then stated that it was attacked. This sweet blow made the project hard to guard against. Attackers stole $5 million in SurgeBNB through a backdoor exploit, officials said. Since SurgeUSD or SurgeETH do not withdraw BNB, they cannot be targeted by future attacks.
#2 Event Specific Analysis
#2 Event Specific Analysis
attack contract
Attacker address:
0x59c686272e6f11dC8701A162F938fb085D940ad3
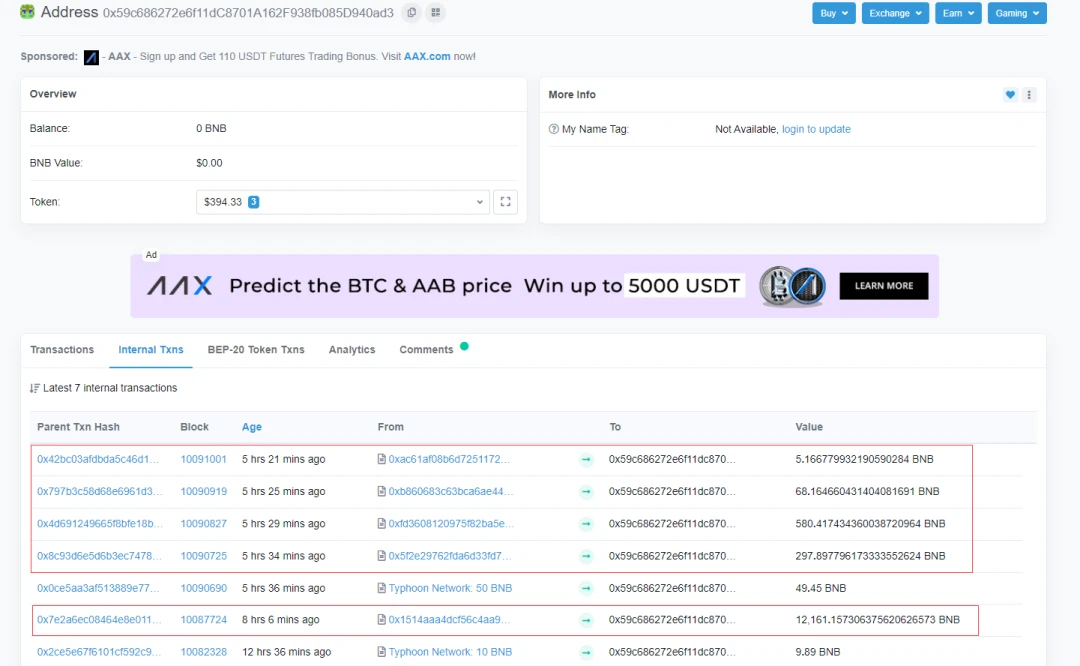
attack contract
to trade
0x8c93d6e5d6b3ec7478b4195123a696dbc82a3441be090e048fe4b33a242ef09d as an example
round 0
First lend 10,000BNB through flash loan.
Round 1
Use all the BNB to buy SURGE. According to the current price, you can buy 1,896,594,328,449,690 SURGE.
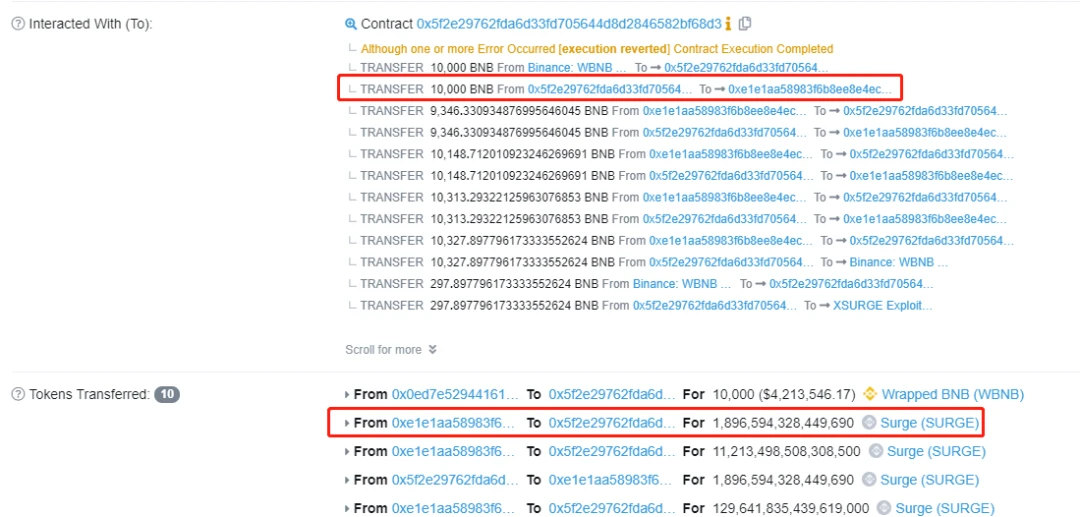
Acquired SURGE
Round 2
Call the sell function to sell the obtained SURGE, and sold 9346 BNB.
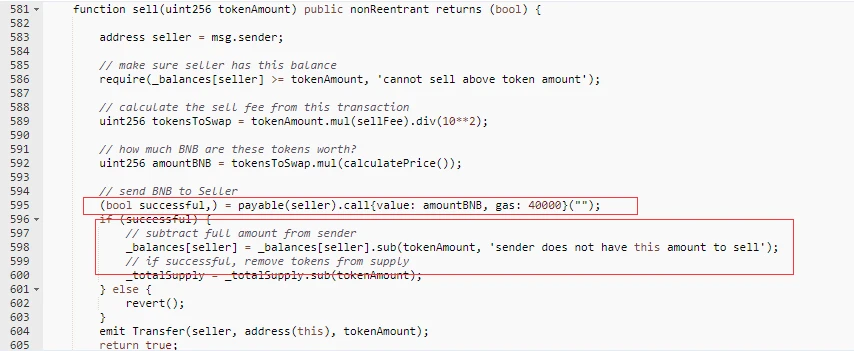 Round 3
Round 3
Because the sell function modifies the data after the transfer, and there is a reentrancy vulnerability in the transfer code. When the attack contract receives BNB, before the state of the SURGE contract changes (line 595), the attack contract can purchase SURGE again through the reentrancy vulnerability.
Since the attack contract uses all the BNB balance to purchase SURGE every time, the bnbAmount of the contract remains unchanged, and the total amount of SURGE tokens _totalSupply is not updated (it is still the amount before the sell), so the price of SURGE decreases, causing the attacker to Get more SURGE.
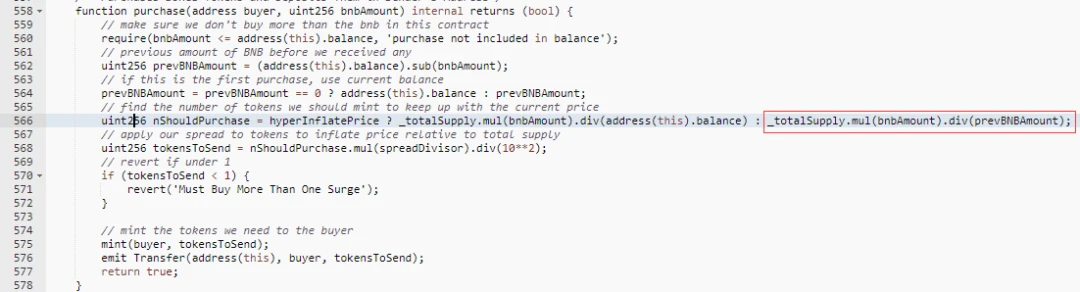
Round 4
Repeat Round2 and Round3 three times, the attacker accumulates a large amount of SURGE through reentry, and then sells all the SURGE to make a profit.
What do we need to pay attention to Case Review
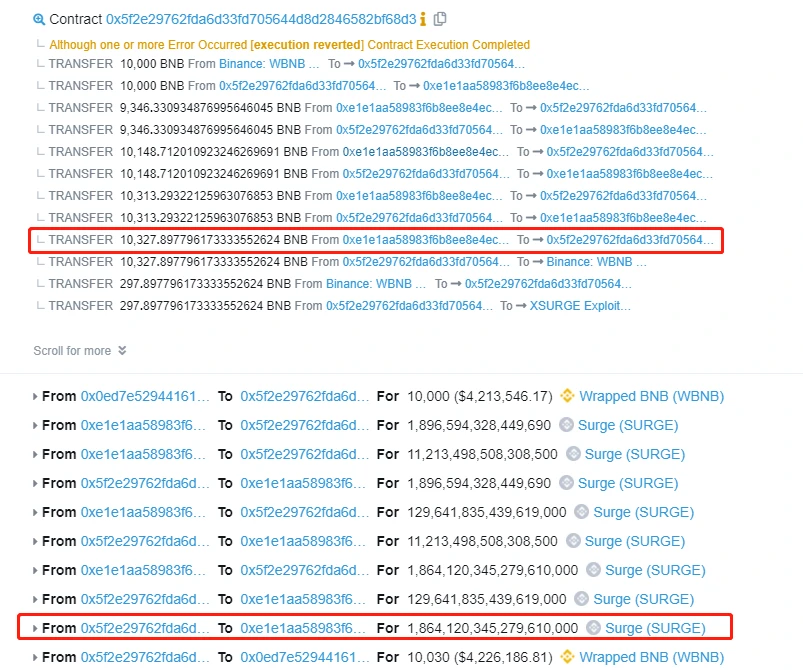
#3 Event review
What do we need to pay attention to Case Review
For this attack, Chengdu Lianan technical team gave suggestions for modification: 1. To prevent re-entry attacks, any transfer operation should occur after the state changes; 2. Use transfer or send to transfer, do not use call. value.
🌀Attention 🌀
🌀Attention 🌀
In this incident, the attacker made more than 13111BNB by exploiting the reentrancy vulnerability of the contract. Chengdu Lianan hereby reminds all users to pay attention to risk control, such as taking corresponding measures in a timely manner after the official statement on the SurgeBNB vulnerability.










