How XT.COM keeps users safe: Comprehensive protection against cyber threats
Key Summary
Enhanced security measures: XT.COM uses two-factor authentication (2FA), cold wallet storage, backup funding mechanism and penetration testing to fully protect user assets from cyber attacks.
November 2024 Security Incident Response: Despite a $1.7 million security breach, XT.COM quickly suspended withdrawals, ensured the safety of user assets, and launched an investigation to prevent similar incidents in the future.
Industry background comparison: Compared with the hacker attacks on Mt. Gox, Coincheck and KuCoin, the scale of the XT.COM incident was relatively small, highlighting the effectiveness of its security mechanism.
Future security upgrades: XT.COM plans to introduce the Merkle tree asset proof mechanism, strengthen wallet security, and deepen cooperation with cybersecurity agencies to further protect user assets.

The cryptocurrency trading market has grown rapidly, attracting a large number of investors and becoming a target for cybercriminals. For exchanges, a strong security system not only protects user funds, but also maintains market trust and meets regulatory requirements. XT.COM was founded in 2018 and is registered in Seychelles. It has launched more than 1,000 digital assets and continues to strengthen security protection. This article will deeply analyze XT.COM's security mechanism, the security incident in November 2024, and future user fund protection strategies, and provide a comparative perspective based on historical hacker attacks.
Table of contents
Why Exchange Security Is Crucial
XT.COM's Core Security Measures
Two-factor authentication (2FA)
Cold wallet storage solution
Reserve Insurance Fund
Anti-money laundering (AML) and user authentication (KYC) mechanism
Penetration Testing and Bug Bounty Programs
Review of security incidents in November 2024
Incident response and risk control
Survey results and improvement measures
Historical security incidents of cryptocurrency exchanges: A comparative analysis of XT.COM
Merkle Tree Asset Proof Mechanism
Continuously optimize infrastructure
Strengthen cooperation with cybersecurity agencies and law enforcement agencies
User Guide: How to improve personal account security
Balancing innovation and risk management
Why Exchange Security Is Crucial
Cryptocurrency exchanges usually manage a large amount of funds, making them a prime target for hackers. Once a security breach occurs, it may not only lead to huge financial losses, but also seriously affect user confidence and even shake the stability of the entire crypto market. In addition, global regulators are increasingly stringent in their requirements for exchanges, and more and more countries are promoting anti-money laundering (AML) and user authentication (KYC) regulations to build a safer trading environment.
As a fast-growing trading platform, XT.COM has invested a lot of resources in security audits and real-time defense to deal with potential cyber threats. In the context of rapid technological iteration, new vulnerabilities continue to emerge. In order to stay ahead of cyber criminals, we must remain highly vigilant and continue to strengthen security protection.

Image Credit: Token Metrics
About XT.COM
Founded in 2018 and registered in Seychelles, XT.COM has quickly attracted traders from around the world. The platform offers more than 1,000 digital assets, including mainstream cryptocurrencies such as Bitcoin (BTC) and Ethereum (ETH), as well as emerging tokens to meet the needs of different investors.
Key Features:
User-friendly interface: Suitable for both novice and professional traders, providing an intuitive operating experience.
Diverse trading options: Provide a variety of trading pairs to help users participate in market transactions flexibly.
Competitive transaction fees: Supports both retail and large traders, reducing transaction costs.
Professional customer support: Provide online help center and instant customer service to ensure that users get timely assistance.
Although XT.COM has many advantages, its core competitiveness still lies in its strong security protection mechanism, including multi-layer identity authentication and strict fund storage management to ensure the security of user assets.
XT.COM's Core Security Measures
Two-factor authentication (2FA)
Two-factor authentication (2FA) is a simple yet powerful security measure that can effectively reduce the risk of account theft. XT.COM supports a variety of 2FA options, including:
Google Authenticator: An application-based dynamic verification code that generates a separate password each time you log in, greatly reducing the possibility of an account being hijacked.
SMS and Email Verification: Send verification codes via SMS or email to add an extra layer of protection to your account.
Compared with SMS verification, Google Authenticator can better prevent phishing attacks and SIM card hijacking (SIM-swap) risks. Regardless of which 2FA you choose, enabling two-factor verification is the basis for ensuring account security. XT.COM strongly recommends that all users enable 2FA immediately after registration and regularly check and update security settings to reduce the risk of device loss or intrusion.
Cold wallet storage solution
XT.COM stores most of the user's assets in cold wallets, which are completely offline wallet systems, so that hackers cannot directly obtain these funds through network attacks. At the same time, only a small amount of funds is stored in hot wallets for daily transactions and withdrawals to reduce the risk of large-scale theft.
The effective implementation of a cold wallet relies on the following key elements:
Secure storage environment: Offline devices are stored in encrypted data centers or isolated computers.
Access rights are strictly controlled: only a very small number of senior authorized employees can access private keys.
Regular audits: Ensure that the funds in the cold wallet are completely consistent with the book data.
Although cold wallets may result in slightly slower withdrawals, it is still one of the industry's recognized best security practices.
Reserve Insurance Fund
XT.COM has set up a reserve insurance fund to protect user assets and provide liquidity support in emergencies. The platform ensures that its reserves reach 1.5 times the total amount of user deposits to cope with any emergencies.
The main functions of the fund include:
Emergency compensation: In the event of a hacker attack or market anomaly, XT.COM can use this fund to compensate for losses.
Reduce financial risks: ensure market stability and avoid platform financial crises caused by unexpected events.
Although the reserve fund cannot directly prevent security breaches, it can provide additional protection when an incident occurs, reflecting XT.COM's commitment to user security.
Anti-money laundering (AML) and user authentication (KYC) mechanism
In order to comply with global regulatory standards and combat illegal activities, XT.COM strictly implements Anti-Money Laundering (AML) and User Authentication (KYC) policies. Users generally need to complete the following steps:
Submit a personal identification document (such as a passport, driver's license, or ID card).
Provide proof of address or other necessary documents (such as bank statements, utility bills, etc.).
Under continuous monitoring, the trading platform will automatically detect and review suspicious trading behavior.
These measures are designed to identify and prevent fraudulent activities such as money laundering, terrorist financing, and other illegal activities. Although AML and KYC may add some steps to the account registration and trading process, they are essential to improving overall security and creating a safer trading environment for compliant traders.
Penetration Testing and Bug Bounty Programs
According to CER.live, an organization that specializes in evaluating the security of cryptocurrency exchanges, XT.COM has a security score of 76/100. This score partly reflects the exchange's continued investment in penetration testing and bug bounty programs:
Penetration Testing: Professional security teams will simulate hacker attacks to discover security vulnerabilities that may be exploited in advance and patch them in a timely manner.
Bug Bounty: XT.COM offers rewards to encourage independent security researchers to proactively report system vulnerabilities so that the exchange can fix them as soon as possible.
These measures enable XT.COM to remain vigilant to the latest cybersecurity risks and ensure that the platform's security mechanisms are always ahead of potential attackers and continuously strengthen defense capabilities.
Review of security incidents in November 2024
Despite the multiple security measures taken by XT.COM, it still suffered a major security incident in November 2024, in which hackers transferred approximately $1.7 million in crypto assets without authorization. The stolen funds were eventually converted into 461.58 ETH (Ether) and transferred to an external wallet.
Incident response and risk control
After discovering the anomaly, XT.COM immediately suspended all withdrawals to prevent further losses. This quick decision successfully reduced the greater impact that the attack could have caused.
At the same time, XT.COM immediately assured the community that the stolen funds came from the platform's reserves, not the user's personal wallet, to ensure that the user's assets were not directly affected. In addition, the exchange promised to conduct a full investigation and emphasized that its reserves are still 1.5 times the total amount of user deposits to ensure the financial stability of the platform.
Investigation and Lessons Learned
After successfully containing the attack, XT.COM will work with cybersecurity experts and possibly law enforcement agencies to conduct an in-depth investigation with the following goals:
Identify the vulnerability: Find out how the hackers were able to penetrate XT.COM's defenses and successfully extract funds.
Prevent similar incidents from happening again: fix security vulnerabilities and strengthen internal security mechanisms.
Maintain transparency: Regularly disclose survey results to users and the community to enhance user trust through open communication.
This incident highlights the complexity of protecting crypto assets. Even if the exchange has multiple layers of protection measures, it may still be attacked by highly skilled hackers. This reminds all trading platforms that the security system must be continuously optimized and upgraded to cope with the evolving cyber threats.
Historical security incidents of cryptocurrency exchanges: A comparative analysis of XT.COM
While any security breach is cause for concern, placing the XT.COM November 2024 security incident in a broader historical context helps assess its severity. Over the past decade, several large crypto exchanges have suffered serious hacks resulting in huge losses, including:
Mt. Gox (2014): This incident is considered the most notorious hack in the history of cryptocurrency. 850,000 Bitcoins (BTC) were stolen from Mt. Gox, which was worth hundreds of millions of dollars at the time and billions of dollars at today’s market prices.
Coincheck (2018): The Tokyo-based exchange was hacked, losing approximately $530 million in NEM (XEM) tokens, making it one of the largest hacks in history.
KuCoin (2020): Hackers stole approximately $275 million in various cryptocurrencies. Although KuCoin successfully recovered some of the funds, it was still a serious security incident.
Poly Network (2021): As a cross-chain protocol, Poly Network lost more than $600 million in digital assets in the attack. Although most of the funds were returned through negotiations, this incident still highlights the high risk of DeFi platforms.
The losses in these incidents ranged from hundreds of millions to billions of dollars, demonstrating the huge security challenges facing cryptocurrency trading platforms. In contrast, the $1.7 million loss in the hacker attack on XT.COM was serious but relatively small, reflecting that its security system still has a certain degree of defense. In addition, XT.COM responded quickly, freezing withdrawals immediately, using reserve funds to compensate for losses, and conducting in-depth investigations, demonstrating the exchange's effective risk control and crisis management capabilities.

Image Credit: Bitcoin.com
Future security upgrade plans
Merkle Tree Asset Proof Mechanism
XT.COM plans to introduce a Merkle Tree asset proof mechanism , allowing users to independently verify the exchange's on-chain assets without revealing sensitive information. This increased transparency will enhance users' trust in the exchange's solvency.
Continuously optimize infrastructure
XT.COM is implementing a series of security enhancement measures to further enhance the platform's protection capabilities, mainly including:
Strengthen hot wallet security: Introduce a multi-signature mechanism to ensure that large withdrawals require authorization from multiple parties, reducing the risk of single-point attacks by hackers.
Real-time threat detection: Deploy advanced firewalls and intrusion detection systems to monitor and block abnormal behaviors and prevent hacker attacks.
Access rights management and employee training: Limit access rights to key systems and provide regular security training to employees to prevent social engineering attacks (such as phishing scams).
Strengthen cooperation with cybersecurity agencies and law enforcement agencies
In addition to internal security upgrades, XT.COM will also work closely with cybersecurity companies and law enforcement agencies to enhance risk monitoring and asset recovery capabilities.
Share threat intelligence: Collaborate with leading global security teams to obtain the latest hacker attack trends and ensure that exchanges can identify and prevent new security threats in advance.
Strengthen fund tracing and recovery: Improve the success rate of tracing and recovering stolen funds through cooperation with law enforcement agencies.
Continue to promote the Bug Bounty Program: Encourage global security researchers to proactively discover and report system vulnerabilities, allowing XT.COM to fix security risks in advance rather than after an attack occurs.
These measures will help XT.COM maintain its security leadership, ensure that the exchange continues to adapt to changing security threats, and provide users with a safer trading environment.
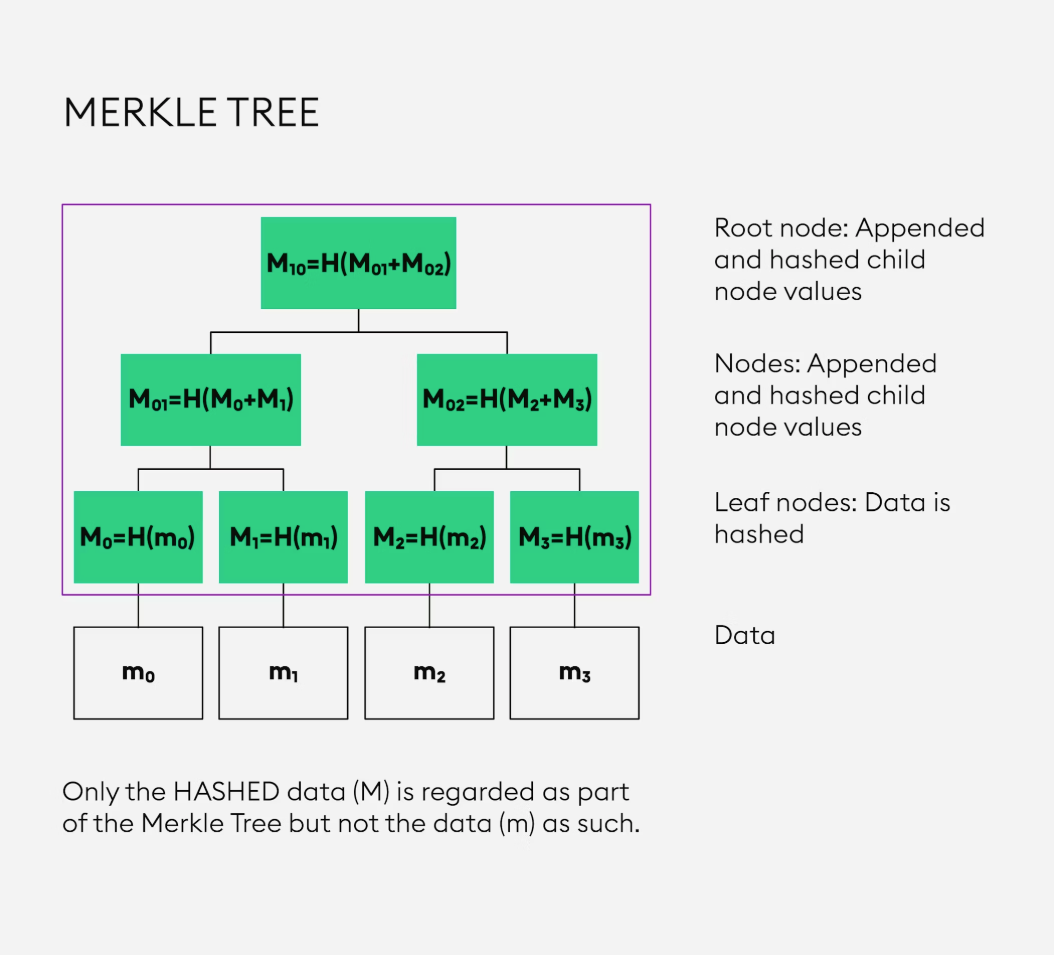
Image Credit: BitPanda
User Guide: How to improve personal account security
Even if the exchange has a strong security mechanism, the user's own security habits are still crucial. Here are a few key suggestions to effectively improve account security:
Enable two-factor authentication (2FA): Google Authenticator is preferred as it is more effective in preventing phishing and SIM-swap attacks than SMS verification codes.
Use strong passwords and avoid reusing them: Make sure your passwords contain uppercase and lowercase letters, numbers, and special characters, and use a different password for each website or application.
Beware of phishing attacks: Do not click on suspicious links, and always verify that the URL is correct before entering your account information.
Check account activities regularly: monitor login records, transaction records and withdrawals. If any abnormality is found, change your password immediately and contact official customer service.
Stay updated: Follow XT.COM official announcements to get the latest security tips and risk warnings.
Balancing innovation and risk management
The hack in November 2024 proved that even exchanges with multiple defense mechanisms can still be attacked by advanced hackers. However, XT.COM responded quickly, demonstrating its transparency and commitment to user protection by freezing withdrawals, using reserve funds to compensate losses, and launching a full investigation.
In the future, XT.COM will continue to upgrade its security mechanisms, including the Merkle Tree asset proof system and infrastructure optimization, indicating that the exchange recognizes that security is not static, but needs to evolve. In the rapidly changing crypto market, XT.COM must continue to assess new risks, test security defenses, and adjust operational strategies to ensure the security of user assets and remain competitive.
About XT.COM
Founded in 2018, XT.COM currently has more than 7.8 million registered users, more than 1 million monthly active users, and more than 40 million user traffic within the ecosystem. We are a comprehensive trading platform that supports 800+ high-quality currencies and 1,000+ trading pairs. XT.COM cryptocurrency trading platform supports a variety of trading products such as spot trading , leveraged trading , and contract trading . XT.COM also has a safe and reliable NFT trading platform . We are committed to providing users with the safest, most efficient, and most professional digital asset investment services.



